
Researchers have linked the comparatively new Ransom Cartel ransomware operation with the infamous REvil gang based mostly on code similarities in each operations’ encryptors.
REvil reached its pinnacle of success within the first half of 2021, compromising 1000’s of firms in a Kaseya MSP supply-chain assault, demanding a $50 million fee from laptop maker Acer, and extorting Apple utilizing stolen blueprints of non-yet-released gadgets.
The REvil ransomware gang lastly shut down in October 2021 following intense stress from regulation enforcement. Nonetheless, in January 2022, the Russian authorities introduced arrests, cash seizures, and expenses towards eight of the gang’s members.
In December 2021, a brand new ransomware operation named ‘Ransom Cartel’ was launched that shared many code similarities to REvil’s malware.
A potential rebrand?
A brand new report from Palo Alto Community’s Unit 42 sheds additional gentle on the connection between the 2 cybercrime gangs, sharing similarities in methods, techniques, and procedures (TTPs) and, most significantly, frequent floor within the code of their malware.
As a result of the supply code of REvil’s encrypting malware was by no means leaked on hacking boards, any new mission utilizing related code is both a rebrand or a brand new operation launched by a core member of the unique gang.
When analyzing encryptors for Ransom Cartel, the researchers discovered similarities within the construction of the configuration embedded within the malware, though the storage places are completely different.
The samples analyzed by Unit 42 present that Ransom Cartel is lacking some configuration values, that means that the authors are both attempting to make the malware leaner or that their foundation is an earlier model of the REvil malware.
The encryption scheme is the place the similarities change into stronger, with Ransom Cartel’s samples producing a number of pairs of public/non-public keys and session secrets and techniques, an REvil system that shined within the Kaseya assaults.
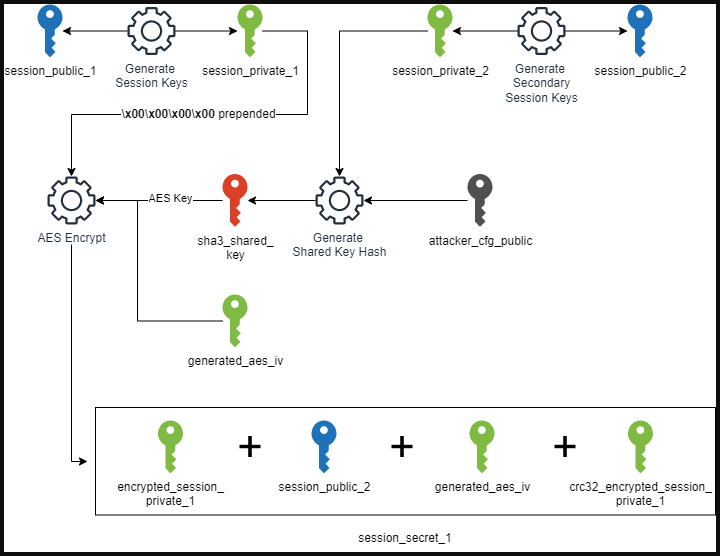
“Each use Salsa20 and Curve25519 for file encryption, and there are only a few variations within the structure of the encryption routine moreover the construction of the interior kind structs,” explains the report by Unit 42 researchers Daniel Bunce and Amer Elsad.
An attention-grabbing discovering is that the Ransom Cartel samples don’t function REvil’s robust obfuscation, which could imply that the authors of the brand new malware do not possess REvil’s authentic obfuscation engine.
Ransom Cartel operations
There are additionally similarities within the techniques, methods, and procedures (TTPs) utilized by REvil and Ransom Cartel, corresponding to double-extortion assaults, giant ransom calls for, and a knowledge leak web site to stress victims into paying a ransom.
Nonetheless, one method utilized by Ransom Cartel, and never seen in REvil assaults, is utilizing the Home windows Information Safety API (DPAPI) to steal credentials.
For this technique, Ransom Cartel makes use of a device named “DonPAPI,” which may search hosts for DPAPI blobs containing Wi-Fi keys, RDP passwords, and credentials saved in net browsers after which obtain and decrypt them regionally on the machine.
These credentials are then used to compromise Linux ESXi servers and authenticate to their vCenter net interfaces.
Lastly, the risk actors shut down VMs, terminate all associated processes, and encrypt Vmware-related information (.log, .vmdk, .vmem, .vswp and .vmsn).
The existence of DonPAPI, a not generally used device, signifies that the operators of Ransom Cartel are skilled risk actors.
.png)
One other REvil-linked ransomware operation?
Whereas there are robust connections between Ransom Cartel and REvil, they don’t seem to be the one ransomware gang at the moment utilizing REvil’s code.
In April 2022, one other ransomware operation we name ‘BlogXX’ was discovered, whose encryptors had been nearly equivalent to the REvil encryptors.
Researchers on the time instructed BleepingComputer that the BlogXX encryptor was not solely compiled from REvil’s supply code but additionally included new adjustments.
“Sure, my evaluation is that the risk actor has the supply code. Not patched like “LV Ransomware” did,” safety researcher R3MRUM instructed BleepingComputer on the time.
AdvIntel CEO Vitali Kremez additionally instructed BleepingComputer that BlogXX’s encryptors included a brand new ‘accs’ configuration possibility that contained account credentials for the focused sufferer.
Moreover, the brand new ransomware operation used equivalent ransom notes and known as themselves ‘Sodinokibi,’ an alternate identify for REvil, on their Tor fee websites.
Supply: BleepingComputer
Nonetheless, in contrast to Ransom Cartel, BlogXX’s historical past has a further part that lends robust proof that they’re, in truth, the REvil rebrand.
After REvil’s shut down, the gang’s previous Tor web sites had been revived, however this time redirected guests to the BlogXX operation’s information leak web site.
Whereas these websites appeared nothing like REvil’s earlier web sites, the truth that the previous Tor websites had been redirecting to BlogXX’s websites confirmed that the brand new operation had management of REvil’s Tor non-public keys.
As solely the unique REvil operators would possess these Tor non-public keys, it confirmed a powerful connection between the 2 gangs.
Whereas irrefutable proof that BlogXX or Ransom Cartel are rebrands of the REvil operation is but to be discovered, it’s fairly clear that no less than a number of the authentic members are behind these new ransomware operations.

