
Google is testing a brand new function to stop malicious public web sites from pivoting by means of a person’s browser to assault units and providers on inside, non-public networks.
More merely, Google plans to stop dangerous web sites on the web from attacking a customer’s units (like printers or routers) in your house or in your pc. People normally think about these units secure as they are not straight linked to the web and are protected by a router.
“To forestall malicious web sites from pivoting by means of the person agent’s community place to assault units and providers which fairly assumed they had been unreachable from the Internet at giant, by advantage of residing on the person’s native intranet or the person’s machine,” Google described the thought in a help doc.
Block unsafe requests to inside networks
The proposed “Private Network Access protections” function, which can be in a “warning-only” mode in Chrome 123, conducts checks earlier than a public web site (known as “website A”) directs a browser to go to one other website (known as “website B”) throughout the person’s non-public community.
The checks embrace verifying if the request comes from a safe context and sending a preliminary request to see if website B (e.g. HTTP server operating on loopback deal with or router’s net panel) permits entry from a public web site by means of particular requests known as CORS-preflight requests.
Unlike current protections for subresources and employees, this function focuses particularly on navigation requests. Its major objective is to defend customers’ non-public networks from potential threats.
In an instance supplied by Google, the builders illustrate an HTML iframe on a public web site that performs a CSRF assault that adjustments the DNS configuration of a customer’s router on their native community.
<iframe href="https://admin:admin@router.local/set_dns?server1=123.123.123.123">
</iframe>
Under this new proposal, when the browser detects {that a} public website makes an attempt to connect with an inside machine, the browser will ship a preflight request to the machine first.
If there is no such thing as a response, the connection can be blocked. However, if the inner machine responds, it might inform the browser whether or not the request must be allowed utilizing an ‘Access-Control-Request-Private-Network‘ header.
This permits requests to units on an inside community to be routinely blocked until the machine explicitly permits the connection from public web sites.
While within the warning stage, even when the checks fail, the function will not block the requests. Instead, builders will see a warning within the DevTools console, giving them time to regulate earlier than stricter enforcement begins.
However, Google warns that even when a request is blocked, an computerized reload by the browser will enable the request to undergo, as it will be seen as an inside => inside connection.
“Private Network Access protections won’t apply on this case for the reason that function was designed to guard customers’ non-public community from more-public net pages,” warns Google.
To forestall this, Google proposes to dam auto-reloading of a web page if the Private Network Access function beforehand blocked it.
When this occurs, the online browser will show an error message stating that you would be able to enable the request to undergo by manually reloading the web page, as proven under.
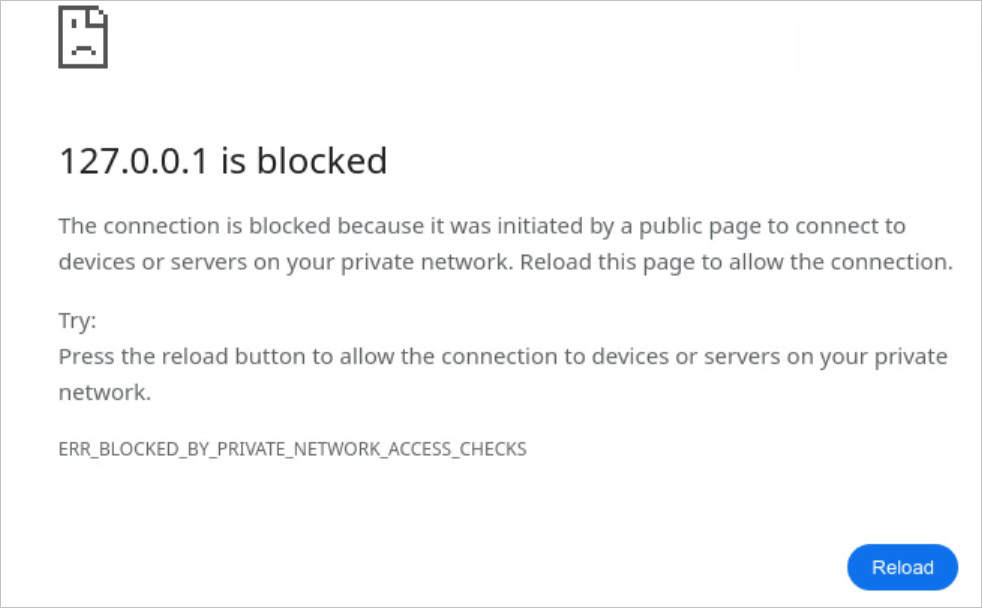
Source: Google
This web page would come with a brand new Google Chrome error message, “BLOCKED_BY_PRIVATE_NETWORK_ACCESS_CHECKS,” to inform you when a web page cannot load as a result of it did not cross Private Network Access safety checks.
The thought behind the safety improve
The motivation behind this growth is to stop malicious web sites on the web from exploiting flaws on units and servers in customers’ inside networks, which had been presumed secure from internet-based threats.
This consists of defending in opposition to unauthorized entry to customers’ routers and software program interfaces operating on native units—a rising concern as extra purposes deploy net interfaces assuming nonexistent protections.
According to a help doc, Google began exploring this concept in 2021 to stop exterior web sites from making dangerous requests to assets throughout the non-public community (localhost or a personal IP deal with).
While the instant purpose is to mitigate dangers like these from “SOHO Pharming” assaults and CSRF (Cross-Site Request Forgery) vulnerabilities, the specification doesn’t purpose to safe HTTPS connections for native providers—a crucial step for integrating public and private assets securely however past the present scope of the specification.
