[ad_1]
Users of Zoho ManageEngine are being urged to patch their cases towards a crucial safety vulnerability forward of the discharge of a proof-of-concept (PoC) exploit code.
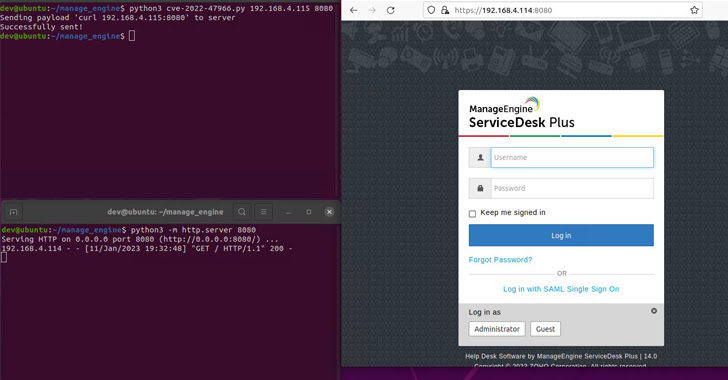
The concern in query is CVE-2022-47966, an unauthenticated distant code execution vulnerability affecting a number of merchandise resulting from using an outdated third-party dependency, Apache Santuario.
“This vulnerability permits an unauthenticated adversary to execute arbitrary code,” Zoho warned in an advisory issued late final 12 months, noting that it impacts all ManageEngine setups which have the SAML single sign-on (SSO) function enabled, or had it enabled prior to now.
Horizon3.ai has now launched Indicators of Compromise (IOCs) related to the flaw, stating that it was in a position to efficiently reproduce the exploit towards ManageEngine ServiceDesk Plus and ManageEngine Endpoint Central merchandise.
“The vulnerability is straightforward to use and candidate for attackers to ‘spray and pray’ throughout the web,” researcher James Horseman mentioned. “This vulnerability permits for distant code execution as NT AUTHORITYSYSTEM, primarily giving an attacker full management over the system.”
An attacker in possession of such elevated privileges might weaponize it to steal credentials with the objective of conducting lateral motion, the San Francisco-headquartered agency mentioned, including the menace actor might want to ship a specifically crafted SAML request to set off the exploit.
Horizon3.ai additional referred to as consideration to the truth that there are greater than 1,000 cases of ManageEngine merchandise uncovered to the web with SAML at present enabled, probably turning them into profitable targets.
It’s not unusual for hackers to use consciousness of a serious vulnerability for malicious campaigns. It’s subsequently important that the fixes are put in as quickly as attainable regardless of the SAML configuration.
Update: PoC Exploit Released
Horizon3.ai has formally launched an exploit for CVE-2022-47966, a crucial safety flaw in a number of Zoho ManageEngine merchandise that enables an adversary to achieve distant code execution by issuing a HTTP POST request containing a malicious SAML response.
Cybersecurity firm Rapid7 disclosed that it is “responding to varied compromises arising from the exploitation of CVE-2022-47966” since a minimum of January 17, 2023, with the menace actors weaponizing the flaw to drop PowerShell scripts to disable Microsoft Defender Antivirus real-time protections and obtain extra distant entry instruments.
“Organizations utilizing any of the affected merchandise […] ought to replace instantly and overview unpatched methods for indicators of compromise, as exploit code is publicly accessible and exploitation has already begun,” Rapid7 researcher Glenn Thorpe mentioned.