[ad_1]

Security researchers warn that the ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ WordPress plugins, with tens of millions of installs, are susceptible to cross-site scripting assaults (XSS).
The two plugins are amongst WordPress’s hottest customized area builders, with 2,000,000 energetic installs on websites worldwide.
Patchstack’s researcher Rafie Muhammad found the high-severity mirrored XSS vulnerability on May 2, 2023, which was assigned the identifier CVE-2023-30777.
XSS bugs usually enable attackers to inject malicious scripts on web sites considered by others, ensuing within the execution of code on the customer’s internet browser.
Patchstack says the XSS flaw might enable an unauthenticated attacker to steal delicate info and escalate their privileges on an impacted WordPress website.
“Note that this vulnerability may very well be triggered on a default set up or configuration of Advanced Custom Fields plugin,” explains Patchstack within the bulletin.
“The XSS additionally might solely be triggered from logged-in customers which have entry to the Advanced Custom Fields plugin.”
This implies that the unauthenticated attacker would nonetheless need to social engineer somebody with entry to the plugin to go to a malicious URL to set off the flaw.
The plugin’s developer was notified of the problem upon Patchstack’s discovery and launched a safety replace on May 4, 2023, in model 6.1.6.
The XSS flaw
The CVE-2023-30777 flaw stems from the ‘admin_body_class’ operate handler, which didn’t correctly sanitize the output worth of a hook that controls and filters the CSS lessons (design and structure) for the principle physique tag within the admin space of WordPress websites.
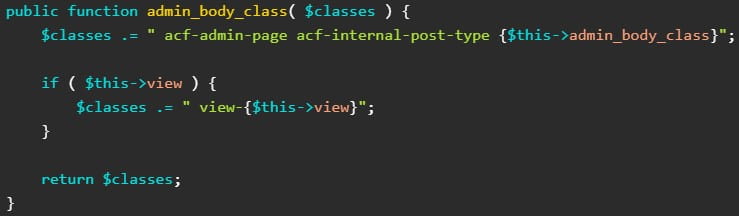
An attacker can leverage an unsafe direct code concatenation on the plugin’s code, particularly the ‘$this→view’ variable, so as to add dangerous code (DOM XSS payloads) in its parts that may move to the ultimate product, a category string.
The cleansing operate utilized by the plugin, ‘sanitize_text_field,’ is not going to cease the assault as a result of it will not catch the malicious code injection.
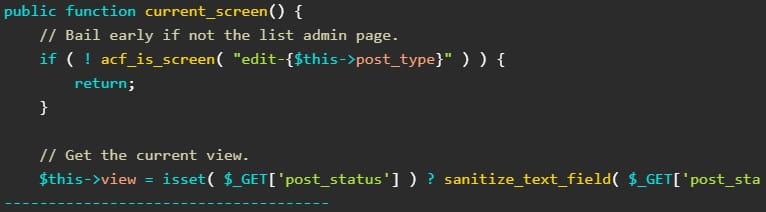
The developer fastened the flaw in model 6.1.6 by implementing a brand new operate named ‘esc_attr‘ that correctly sanitizes the output worth of the admin_body_class hook, therefore, stopping the XSS.
All customers of ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ are suggested to improve to model 6.1.6 or later as quickly as potential.
Based on WordPress.org obtain stats, 72.1% of the plugin’s customers are nonetheless utilizing variations under 6.1, that are susceptible to XSS and different recognized flaws.
