[ad_1]
Every SaaS app person and login is a possible menace; whether or not it is dangerous actors or potential disgruntled former associates, identification administration and entry management is essential to stop undesirable or mistaken entrances to the group’s knowledge and techniques.
Since enterprises have hundreds to tens of hundreds of customers, and tons of to hundreds of various apps, guaranteeing every entrance level and person position is safe is not any straightforward feat. Security groups want to observe all identities to make sure that person exercise meets their group’s safety pointers.
Identity and Access Management (IAM) options administer person identities and management entry to enterprise assets and functions. As identities grew to become the brand new perimeter, ensuring this space is ruled by the safety crew is important.
Gartner has just lately named a brand new safety self-discipline referred to as Identity Threat Detection and Response (ITDR) that includes detection mechanisms that examine suspicious posture adjustments and actions, and responds to assaults to revive the integrity of the identification infrastructure.
ITDR incorporates sturdy SaaS Security IAM Governance methodologies and greatest practices which might be present in SaaS Security Posture Management options (SSPM), enabling safety groups to realize steady and consolidated visibility of person accounts, permissions, and privileged actions throughout the SaaS stack, corresponding to:
- Identifying who’s accessing what and when, and with the proper ranges of privileges
- Forensics associated to person actions, specializing in privileged customers
- Roles’ steady and automatic discovery and consolidation
- Role right-sizing by revoking pointless or undesirable entry
Whether you’re a CISO, IT or on the Governance, Risk and Compliance (GRC) crew, this text will cowl the position of Identity and Access Management Governance as a part of the group’s SaaS safety program.
Learn how one can implement IAM governance in your SaaS Security.
What is IAM Governance
IAM Governance permits the safety crew to behave upon arising points by offering fixed monitoring of the corporate’s SaaS Security posture in addition to its implementation of entry management.
There are a couple of important prevention domains the place an SSPM, like Adaptive Shield, can handle Identity and Access Management Governance: 1) Misconfigurations 2) Vulnerabilities 3) Exposure.
Misconfigurations
IAM controls should be correctly configured on a steady foundation. The IAM configurations must be monitored for any suspicious adjustments and be certain that the suitable steps are taken to analyze and remediate when related.
For instance, a company can allow MFA throughout the group and never require it. This hole in coverage enforcement can go away the group in danger — and an SSPM can alert the safety crew about this hole.
Vulnerabilities
The SSPM resolution can make the most of patching or compensating controls to handle generally exploited vulnerabilities within the identification infrastructure such because the SaaS person’s gadget. For instance, a privileged CRM person can current a excessive danger to the corporate if their gadget is susceptible. To remediate potential threats that stem from units, safety groups want to have the ability to correlate SaaS app customers, roles, and permissions with their related units’ hygiene. This end-to-end tactic permits a holistic zero-trust strategy to SaaS safety.
Another important vulnerability stems from authentication protocols that the password entry is proscribed to a single-factor authentication methodology, corresponding to with legacy protocols like IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can establish the place these protocols are in place throughout the group’s SaaS stack.
Exposure
The SSPM helps to cut back the assault floor by figuring out and mitigating locations of publicity. For instance, eradicating pointless or extreme privileges or permitting an exterior admin for a business-critical app. (See determine 1.)
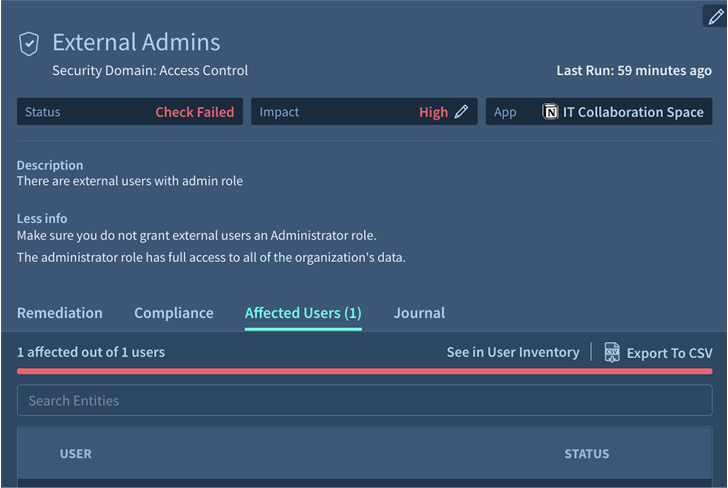 |
| Figure 1. Adaptive Shield’s safety verify for exterior admins |
Additionally, third celebration app entry, often known as SaaS-to-SaaS entry can go away a company uncovered. Users join one app to a different app to both present enhanced options or person’s info (e.g contacts, recordsdata, calendar, and so on). This connection boosts workflow effectivity and in consequence, staff’ workspaces are linked to multitudes of various apps. However, the safety crew is most frequently at midnight about which apps have been linked to their group’s ecosystem, unable to observe or mitigate any threats.
Wrap-Up
IAM is a technique for hardening entry management, whereas IAM Governance in SSPMs provide steady monitoring of those options to make sure safety groups have full visibility and management of what is taking place within the area.
Get a reside demo to discover ways to achieve Identity and Access Governance to your SaaS stack.

