[ad_1]
When SaaS purposes began rising in reputation, it was unclear who was liable for securing the info. Today, most safety and IT groups perceive the shared accountability mannequin, wherein the SaaS vendor is liable for securing the appliance, whereas the group is liable for securing their information.
What’s far murkier, nevertheless, is the place the info accountability lies on the group’s aspect. For massive organizations, it is a notably difficult query. They retailer terabytes of buyer information, worker information, monetary information, strategic information, and different delicate information data on-line.
SaaS information breaches and SaaS ransomware assaults can result in the loss or public publicity of that information. Depending on the business, some companies might face stiff regulatory penalties for information breaches on high of the detrimental PR and lack of religion these breaches deliver with them.
Finding the appropriate safety mannequin is step one earlier than deploying any kind of SSPM or different SaaS safety answer.
Learn how Adaptive Shield’s SSPM answer may also help safe your SaaS stack.
Getting to Know the Players
There are a number of completely different teams of gamers concerned within the SaaS safety ecosystem.
SaaS App Owners – When enterprise items subscribe to SaaS software program, somebody from throughout the enterprise unit is usually liable for organising and onboarding the appliance. While they might have some assist from IT, the appliance is their accountability.
They select settings and configurations that align with their enterprise wants, add customers, and get to work. SaaS App Owners acknowledge the necessity for information safety, but it surely is not their accountability or one thing they know very a lot about. Some mistakenly assume that information safety is just the accountability of the SaaS vendor.
Central IT – In most massive organizations, Central IT is liable for issues like infrastructure, {hardware}, and passwords. They handle IDP and servers, in addition to oversee assist desk actions. SaaS purposes usually don’t fall beneath their direct area.
Central IT is extra accustomed to safety necessities than the typical worker, but it surely is not their main concern. However, it is very important take into account that they don’t seem to be safety professionals.
Security Teams – The safety staff is the pure match for implementing safety controls and oversight. They are tasked with creating and implementing a cybersecurity coverage that applies throughout the group.
However, they’ve a number of challenges inhibiting their capacity to safe purposes. For starters, they’re usually unaware of SaaS purposes which might be being utilized by the corporate. Even for purposes that they’re conscious of, they lack entry to the configuration panels throughout the SaaS stack, and are not all the time conscious of the distinctive safety points related to every utility. Those are managed and maintained by the SaaS App Owners and Central IT.
GRC Teams – Compliance and governance groups are tasked with guaranteeing that each one IT meets particular safety requirements. While they do not play a particular position in securing company property, they do have oversight and wish to find out whether or not the corporate resides as much as its compliance obligations.
SaaS Vendor – While the SaaS vendor is absolved from any accountability to safe the info, they’re the staff that constructed the safety equipment for the SaaS utility, and have a deep information of their utility and its safety capabilities.
Defining Roles and Responsibilities
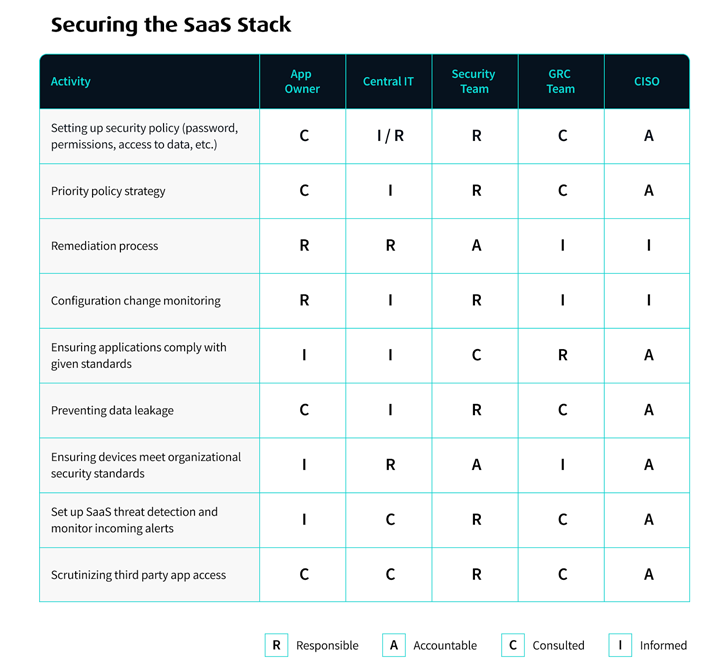
Securing your complete SaaS stack requires shut collaboration between the safety consultants and people managing and working their particular person SaaS purposes. We developed this RACI chart to share our perspective on the departments which might be accountable, accountable, consulted, and knowledgeable for the completely different duties concerned in securing SaaS information.
Bear in thoughts, this desk is just not one dimension suits all, however a framework based mostly on the way in which we see many corporations dealing with their SaaS safety roles. It ought to be tailored to the wants of your group.
Learn extra about SaaS person roles and obligations. Schedule a demo right this moment.
Building the Right Infrastructure
Developing the RACI matrix is vital, however with out the appropriate instruments in place, implementing safety obligations turns into a near-impossible job.
Organizations want a SaaS Security platform that facilitates clear communication between the safety staff and app homeowners. This communication ought to embody alerts when misconfigurations happen that weaken the person app’s safety posture and when threats are detected by its IAM governance instruments.
Communication ought to be channel agnostic, so customers can obtain messages and alerts over e-mail, Slack, Splunk, or the messaging platform of selection. All security-related notifications also needs to embody remediation steps, offering app homeowners and central IT with a transparent understanding of the steps required to mitigate the danger.
Within the platform, every proprietor ought to have visibility and entry to the app or apps beneath their management. They ought to be capable to see the standing of their safety settings, their safety rating, their customers, third-party SaaS purposes which might be related to their app, and the gadgets getting used to entry their SaaS app.
App homeowners and central IT also needs to have the capabilities to dismiss a safety alert due, both as a result of it would not apply or on account of enterprise wants, and seek the advice of with the safety staff on danger.
Securing SaaS Data Takes a Cross-Team Effort
It’s straightforward for SaaS utility safety to be neglected. It sits outdoors the view of the safety staff and is managed by competent professionals whose obligations do not embody safety.
However, the info contained throughout the SaaS purposes are sometimes the lifeblood of a corporation, and failure to safe the info can have disastrous penalties.
Fully defending the info from publicity requires a cross-team effort and dedication from all events concerned, in addition to a complicated SSPM platform constructed for SaaS in the true world.
Learn how an SSPM may also help safe your information. Book a demo.