[ad_1]
As everybody appears about, sirens start to sound, creating a way of urgency; they solely have a break up second to find out what to do subsequent. The announcer repeats himself over the loudspeaker in brief bursts… This will not be a drill; report back to your particular person formations and proceed to the allotted zone by following the numbers in your squad chief’s purple cap. I take a breather and ponder whether or not that is an evacuation. What underlying hazard is coming into our every day actions? 1…2….3…. Let’s get this occasion began!
When I come to… I discover that the blue and purple lights solely exist within the safety operations heart. Intruders try to infiltrate our defenses in actual time; subsequently, we’re on excessive alert. The time has come to depend on incident response plans, catastrophe restoration procedures, and enterprise continuity plans. We function safety posture guardians and incident response technique executors as organizational safety leaders. It is significant to reply to and mitigate cyber incidents, in addition to to scale back safety, monetary, authorized, and organizational dangers in an environment friendly and efficient method.
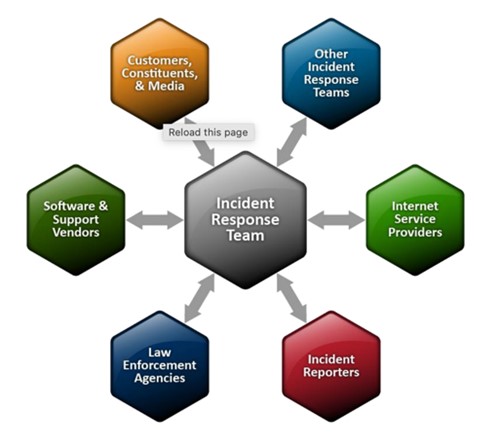
Stakeholder neighborhood
CISOs, as safety leaders, should develop incident response groups to fight cybercrime, information theft, and repair failures, which jeopardize every day operations and stop shoppers from receiving world-class service. To keep operations tempo, alert the on-the-ground, first-line-of-defense engagement groups, and stimulate real-time decision-making, Incident Response Plan (IRP) protocols should embrace end-to-end, various communication channels.
What does an incident response plan (IRP) do?
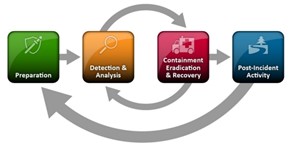
That’s a superb query. The incident response plan offers a construction or guideline to comply with to scale back, mitigate, and get well from a knowledge breach or assault. Such assaults have the potential to trigger chaos by impacting prospects, stealing delicate information or mental property, and damaging model worth. The essential steps of the incident response course of, in line with the National Institute of Standards and Technology (NIST), are preparation, detection and evaluation, containment, eradication, and restoration, and post-incident exercise that focuses on a continuous studying and enchancment cycle.
Lifecycle of Incident Response
Many firm leaders confront a bottleneck in the case of assigning a severity ranking that determines the influence of the incident and establishes the framework for decision methods and exterior messaging. For some corporations, having the ability to examine the harm and appropriately assign a precedence stage and influence ranking may be disturbing and terrifying.
Rating occasions can assist prioritize restricted sources. The incident’s enterprise influence is calculated by combining the practical impact on the group’s programs and the influence on the group’s data. The recoverability of the state of affairs dictates the attainable solutions that the crew might take whereas coping with the problem. A excessive practical influence incidence with a low restoration effort is suited to quick crew motion.
The coronary heart beat
Companies ought to comply with trade requirements which were tried and examined by fireplace departments to enhance total incident response effectiveness. This consists of:
- Current contact lists, on-call schedules/rotations for SMEs, and backups
- Conferencing instruments (e.g., distribution lists, Slack channels, emails, telephone numbers)
- Technical documentation, community diagrams, and accompanying plans/runbooks
- Escalation processes for inaccessible SMEs
Since enemies are transferring their emphasis away from established pathways to keep away from defenders, it’s vital to enlist third-party menace panorama evaluations. These can halt the bleeding and cauterize the wound, very like a surgeon in a high-stress operation. Threat actors are all the time enhancing their talents utilizing the identical rising scorching cyber applied sciences that defenders use.
Despite widespread recognition of the human facet because the weakest hyperlink, menace actors research their prey’s community to hunt different weak factors akin to straddle vulnerability exploitation and credential theft. Employ Managed Threat Detection Response (MTDR), Threat Model Workshop (TMW), and Cyber Risk Posture Assessment (CRPA) providers to expertly handle your infrastructure and cloud environments in a one-size-fits-all approach.
Takeaways
Take stock of your property
- Increase return on funding
- Provide complete protection
- Accelerate compliance wants
- Create a cybersecurity monitoring response technique
- Emphasize important sources, assault floor space, and menace vectors
- Deliver clear, seamless safety
Elevate safety ecosystem
In the long run, companies ought to implement an incident response technique, a set of well-known, verified greatest practices, and assess their precise versus realized property and safety assault floor portfolio. Is your group crisis-ready? A robust incident administration answer will increase organizational resiliency and continuity of operations within the occasion of a disaster.