[ad_1]
A brand new analysis report from SentinelOne exposes a web optimization poisoning assault marketing campaign that hijacks model names in paid search adverts.

SentinelOne has reported a rise in malicious search engine commercials in current weeks. The researchers clarify that attackers utilizing SEO poisoning are usually extra profitable “when they SEO poison the results of popular downloads associated with organizations that do not have extensive internal brand protection resources.”
Jump to:
What is an web optimization poisoning assault?
web optimization poisoning assaults encompass altering search engines like google and yahoo outcomes in order that the primary marketed hyperlinks really result in attacker managed websites, usually to contaminate guests with malware or to draw extra folks on ad fraud. SentinelOne supplied an instance of a current web optimization poisoning marketing campaign of their report.
SEE: Mobile machine safety coverage (TechRepublic Premium)
The Blender 3D web optimization poisoning marketing campaign
A routine search on Google’s search engine for the model title Blender 3D, an open-source 3D graphics design software program, supplied the next outcomes on Jan. 18, 2023 (Figure A):
Figure A
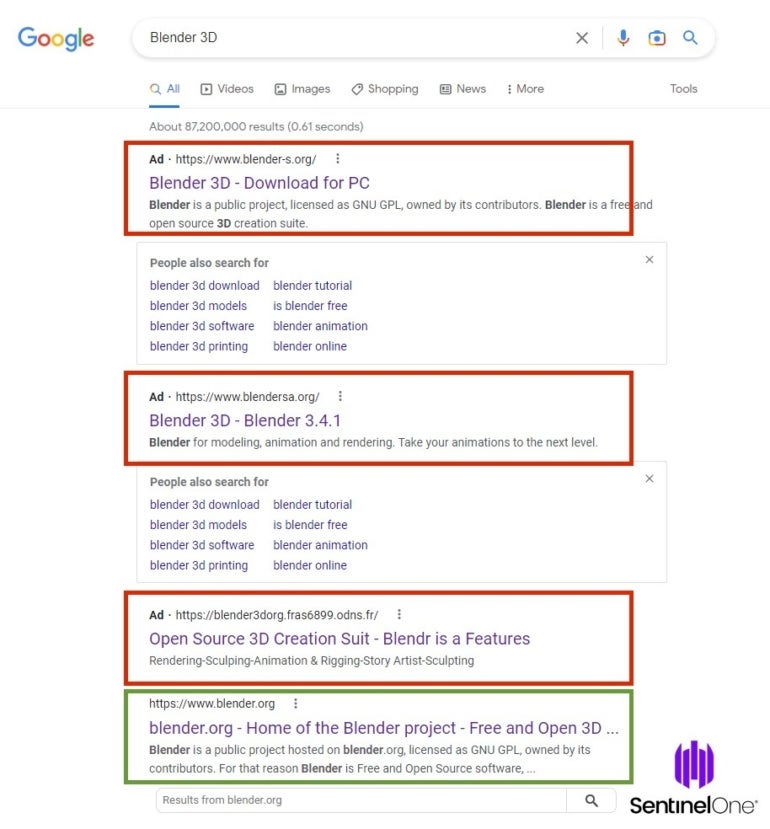
A person who doesn’t learn the URL intently or is not sure of the precise URL of the software program may click on on any of these attacker-controlled domains, which may end in a compromise.
The malicious prime consequence blender-s.org is a close to actual copy of the authentic web site from Blender, but the obtain hyperlink doesn’t result in a obtain on blender.org however to a DropBox URL delivering a blender.zip file.
The second malicious web site at blenders.org is analogous: It exhibits a close to excellent copy of the authentic Blender web site, but the obtain hyperlink results in one other DropBox URL, additionally delivering a blender.zip file.
The third and final malicious web site can be a duplicate of the authentic one, but it offers a Discord URL and delivers a file named blender-3.4.1-windows-x64.zip.
The web optimization poisoning payloads
The zip recordsdata that are downloaded from Dropbox include executable recordsdata. The first one instantly raises suspicion because it exhibits an invalid certificates from AVG Technologies USA, LLC (Figure B) which has been already noticed as being utilized by different malware together with the notorious Racoon Stealer.
Figure B

It can be value mentioning that the zip file has a measurement that’s lower than 2 MB, however the executable file extracted from it’s near 500 MB. This might be an try and bypass some safety options who don’t analyze such massive recordsdata.
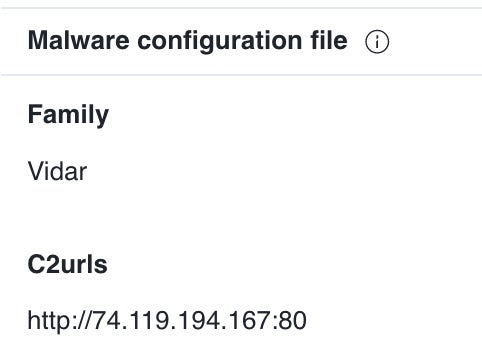
According to VirusTotal, the malware could be the Vidar malware (Figure C), an info stealer with the power to steal monetary info, passwords and shopping historical past from browsers, password managers and cryptocurrency wallets.
Figure C
The second zip file, unknown to VirusTotal, could be comparable, because the zip file has the identical measurement and has been created 5 minutes after the primary one. The last file, downloaded from Discord, accommodates an ISO file that’s in all probability additionally malicious.
Widening the assault floor
According to SentinelOne researchers, the risk actor behind the primary two malicious web sites are additionally accountable for dozens of different comparable web sites, all the time impersonating standard software program similar to Photoshop or distant entry software program.
All of these web sites had been shortly blocked by CloudFlare, whose companies had been utilized by the cybercriminals. Any person trying to connect with the fraudulent web sites is now proven a warning web page from CloudFlare mentioning their phishy nature.
How to mitigate this risk and defend your organization’s repute
As talked about, web optimization poisoning attackers often select to impersonate standard merchandise or manufacturers with the intention to run their malicious operations. This has a huge effect on customers, as they may find yourself being compromised by malware, which may result in stolen information. Yet it additionally has a huge effect on firms, as the typical person usually doesn’t perceive this sort of fraud and ultimately thinks that the actual model is accountable.
Companies with highly regarded merchandise or manufacturers ought to be cautious about their manufacturers and deploy safety options to assist them detect such fraud earlier than it’s too late.
For starters, organizations ought to rigorously examine each new area that’s registered on the Internet that accommodates similarities with any of their manufacturers or names. As fraudsters usually register domains which are similar to the authentic ones, it’s attainable to detect them inside 48 hours typically, instantly analyze the state of affairs and take motion to mitigate the chance.
Companies can work on the authorized facet to have the fraudulent domains transferred to them after they can justify {that a} trademark infringement exists, however that may take some time. In the meantime, ought to any fraudulent content material seem on the fraudulent area, they may wish to shut it down by contacting the internet hosting firm, registrar or DNS supplier to render the fraud unreachable.
Finally, firms can preventively register completely different variants of their authentic domains in order that fraudsters can’t achieve this. However, this technique takes power and cash, and never each firm could wish to go down this path.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
