[ad_1]
A cybercrime group often called Vice Society has been linked to a number of ransomware strains in its malicious campaigns aimed on the training, authorities, and retail sectors.
The Microsoft Security Threat Intelligence staff, which is monitoring the menace cluster beneath the moniker DEV-0832, stated the group avoids deploying ransomware in some instances and somewhat probably carries out extortion utilizing exfiltrated stolen information.
“Shifting ransomware payloads over time from BlackCat, Quantum Locker, and Zeppelin, DEV-0832’s newest payload is a Zeppelin variant that features Vice Society-specific file extensions, comparable to .v-s0ciety, .v-society, and, most not too long ago, .locked,” the tech big’s cybersecurity division stated.
Vice Society, lively since June 2021, has been steadily noticed encrypting and exfiltrating sufferer information, and threatening corporations with publicity of siphoned info to stress them into paying a ransom.
“Unlike different RaaS (Ransomware-as-a-Service) double extortion teams, Vice Society focuses on moving into the sufferer system to deploy ransomware binaries bought on Dark internet boards,” cybersecurity firm SEKOIA stated in an evaluation of the group in July 2022.
The financially motivated menace actor is understood to depend on exploits for publicly disclosed vulnerabilities in internet-facing functions for preliminary entry, whereas additionally utilizing PowerShell scripts, repurposed authentic instruments, and commodity backdoors comparable to SystemBC previous to deploying the ransomware.
Vice Society actors have additionally been noticed leveraging Cobalt Strike for lateral motion, along with creating scheduled duties for persistence and abusing vulnerabilities in Windows Print Spooler (aka PrintNightmare) and Common Log File System (CVE-2022-24521) to escalate privileges.
“Vice Society actors try to evade detection by means of masquerading their malware and instruments as authentic recordsdata, utilizing course of injection, and sure use evasion strategies to defeat automated dynamic evaluation,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) stated final month.
In one July 2022 incident disclosed by Microsoft, the menace actor is alleged to have tried to initially deploy QuantumLocker executables, solely to comply with it up with suspected Zeppelin ransomware binaries 5 hours later.
“Such an incident may counsel that DEV-0832 maintains a number of ransomware payloads and switches relying on track defenses or, alternatively, that dispersed operators working beneath the DEV-0832 umbrella may preserve their very own most popular ransomware payloads for distribution,” Redmond famous.
Among different instruments utilized by DEV-0832 is a Go-based backdoor referred to as PortStarter that gives the aptitude to change firewall settings and open ports to determine connections with pre-configured command-and-control (C2) servers.
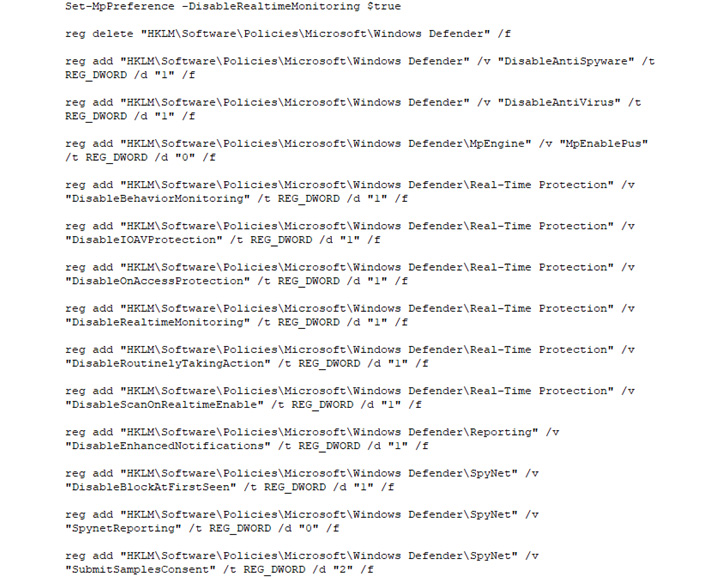
Vice Society, except for making the most of living-off-the-land binaries (LOLBins) to run malicious code, has additionally been discovered trying to show off Microsoft Defender Antivirus utilizing registry instructions.
Data exfiltration is ultimately achieved by launching a PowerShell script that transmits wide-ranging delicate info, starting from monetary paperwork to medical information, to a hard-coded attacker-owned IP tackle.
Redmond additional identified that the cybercrime group focuses on organizations with weaker safety controls and the next probability of a ransom payout, underscoring the necessity to apply obligatory safeguards to forestall such assaults.
“The shift from a ransomware as a service (RaaS) providing (BlackCat) to a bought wholly-owned malware providing (Zeppelin) and a customized Vice Society variant signifies DEV-0832 has lively ties within the cybercriminal economic system and has been testing ransomware payload efficacy or post-ransomware extortion alternatives,” Microsoft stated.