[ad_1]
Microsoft has developed a brand new option to preserve clients knowledgeable about safety vulnerabilities that have an effect on their Azure sources. When a vulnerability is disclosed that impacts their sources, clients will likely be notified via Service Health within the Azure Portal. This Service Health message will embody details about the vulnerability’s frequent vulnerabilities and exposures quantity (CVE), severity, and steps clients can take to safeguard in opposition to it. In most instances, it can additionally embody an inventory of the particular sources of their subscription that clients have to take motion on.
Our aim is to offer a extra constant and dependable expertise for purchasers. Recent improvements in Azure Service Health now enable us to ship communications with impacted sources and goal messaging at tenant admins. With these new improvements, we will leverage current work finished by the Microsoft Security Response Center (MSRC) in vulnerability reporting to carry actionable info to clients that’s tailor-made to their distinctive setting.
Below is an summary of how Microsoft discloses new vulnerabilities, the place to search out messages concerning CVEs in Azure Service Health, and tips on how to perceive the content material in a Service Health message.
About vulnerabilities at Microsoft
Microsoft discloses a variety of vulnerabilities each month throughout the spectrum of Microsoft product teams, together with Windows, Microsoft 365, and Azure. When these vulnerabilities are publicly disclosed and require buyer motion, they’re assigned a CVE quantity and printed within the Security Update Guide by the Microsoft Security Response Center (MSRC).
Customers can be taught extra about how Microsoft collaborates with the safety analysis group to establish and mitigate vulnerabilities within the Anatomy of a Cloud-Service Security Update weblog from MSRC.
A CVE signifies that motion is required from clients as a way to stay safe. Whenever a vulnerability is disclosed that impacts an Azure services or products, the Azure communications staff collaborates with MSRC and product engineering to make sure that weak clients are notified of any actions they should take to mitigate the vulnerability. Like communications concerning ongoing outages or upcoming upkeep, these notifications are printed to Service Health within the Azure Portal.
Note that, even when we message clients concerning a CVE, this doesn’t point out any abuse, exploitation, or hacking has occurred. While vulnerabilities are frequent, these are sometimes reported and stuck earlier than any risk actor can exploit them or manipulate buyer information.
Service Health messages for Azure CVEs
Where to search out messages for Azure CVEs
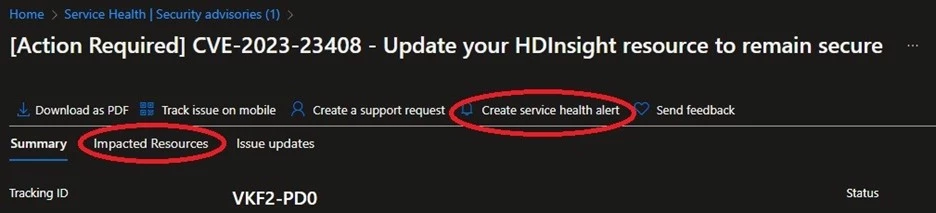
Advisories for newly disclosed CVEs will seem below the Security advisories blade in Service Health within the Azure Portal. The title of those communications will sometimes lead with “[Action Required]” and embody the CVE quantity. From right here, clients can click on the title of the message and drill down into the message contents.
We will solely ship communications to clients that both have sources which are weak to the CVE or who in any other case have to take some type of motion to remediate. If a given CVE impacts Azure App Service ASP.NET deployments, for instance, you gained’t obtain a message if you happen to don’t have any App Service sources or in case your App Service sources solely encompass Python net apps. On uncommon events, it might be harder for us to find out which particular sources are weak to a given CVE. In such instances, we could ship a CVE notification to an approximate set of consumers. If we publish messaging to an approximate set of consumers, we goal to incorporate steerage that clients can comply with to validate whether or not they have sources deployed which are weak to the CVE.
How to learn messages for Azure CVEs
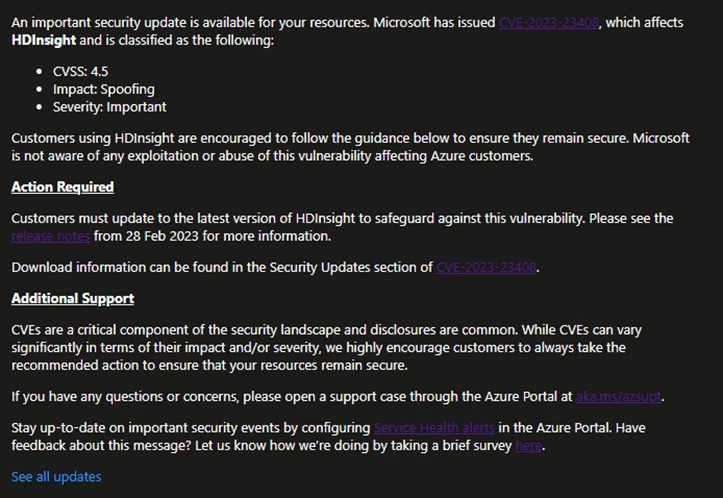
Service Health messages for Azure CVEs sometimes encompass three elements:
- An overview of the CVE.
- A abstract of the motion required from clients.
- Links to extra help.
The opening portion of the message will give clients a high-level overview of the vulnerability, frequent vulnerability scoring system (CVSS) rating, influence, and severity as outlined within the CVE itself. This part can even clarify which Azure companies or options are weak to this CVE and embody a hyperlink to the CVE within the Security Update Guide.
The Action Required part dives into the steerage for purchasers to safeguard in opposition to the particular vulnerability. In the Service Health message, we could present a summarized model of the mitigation steps for fast reference, however clients are inspired to confer with the Security Update Guide for hyperlinks to the suitable sources wanted to mitigate, together with documentation and replace packages.
Lastly, the Additional Support part contains hyperlinks to sources that clients can confer with as a way to open a help case and configure alerting in Service Health. Customers who’ve questions concerning a CVE past the knowledge offered within the Service Health message, or want additional help in making use of mitigation steps, are inspired to open a help case via the Azure Portal.
We try to offer the identical degree of element from message to message, whatever the perceived influence of the vulnerability. A CVSS 8.0 could imply one thing completely different for a buyer internet hosting an e-commerce website on a digital machine (VM) scale set than for a buyer utilizing one VM to host a Minecraft server as a sandbox for his or her associates. As such, our aim is to offer the mandatory info for purchasers to make an knowledgeable determination about tips on how to method their safety. We all the time encourage clients to comply with the really useful steerage offered as quickly as doable and comply with safety greatest practices.
Who can learn Service Health messages concerning Azure CVEs?
In most instances, we’ll goal a Service Health message concerning an Azure CVE to the particular subscriptions with sources recognized as weak or the place clients have to take some motion. Any person with reader privileges within the subscription will be capable to navigate to Service Health and look at the message.
On some events, we could goal the message to specific tenants if the vulnerability impacts customers on the tenant degree. In such instances, solely tenant admins, or roles with tenant admin entry, will be capable to view the message after toggling their view for tenant-level occasions. Communications for tenant-level occasions are solely obtainable within the new Azure Portal expertise.
Impacted sources and Service Health alerts
For these instances the place we will establish particular sources that could be weak to a given CVE, a brand new characteristic of Azure Service Health permits us to give you details about the sources in your subscription that will require motion. Customers can view this info by clicking the “Impacted Resources” tab in direction of the highest of the message subsequent to the “Summary” tab. The useful resource info offered can vary from a selected useful resource ID (together with useful resource group and useful resource title) to the present runtime model and will differ relying on the character of the vulnerability. For extra details about the brand new Service Health expertise, see our documentation about useful resource influence from Azure safety incidents.
Additionally, clients can configure Service Health alerts for his or her Azure sources. Service Health alerts will notify you thru your most popular notification channel corresponding to SMS and e mail when your sources are affected by a platform occasion. These alerts might be configured for various kinds of occasions, from safety occasions to outages to deliberate upkeep updates.
What about third-party CVEs that have an effect on Microsoft merchandise?
These instances are uncommon, however they do occur sometimes. There are two major conditions through which this is able to occur:
- When a non-Microsoft product comprises a vulnerability, however that product is used as an underlying element of a Microsoft providing (ex. sure open-source software program).
- When an providing from an Independent Software Vendor (ISV) offered on the Azure Marketplace comprises a vulnerability.
In such instances, Microsoft wouldn’t launch the CVE, however slightly the disclosure of the CVE could be finished by the third celebration that owns the weak software program. Regardless, Microsoft could publish our personal messaging concerning third celebration CVEs to Azure Service Health.
If a third celebration CVE has a downstream influence on a Microsoft services or products, we could publish messaging to affected clients to boost consciousness and inform them of any motion they should take.
If a CVE is disclosed that impacts an providing on the Azure Marketplace, Microsoft could message clients utilizing that providing on the request of the ISV or if we decide there’s some imminent danger to our clients. In basic, for CVEs affecting choices on the Azure Marketplace, clients are inspired to work with the related ISV for questions concerning the safety of their providing.
Stay up to date on safety occasions
To summarize, these are the important thing issues to bear in mind concerning how Microsoft retains clients knowledgeable about vulnerabilities affecting Azure Services:
- Customers recognized as weak to a given CVE will likely be notified via Service Health within the Azure Portal.
- In some instances, we could not be capable to establish a exact set of affected clients. In such instances, we could goal an approximate set of consumers with messaging.
- We goal to incorporate details about the particular sources in a buyer’s subscription that could be weak and must be up to date.
- If we’re unable to offer details about particular affected sources, we’ll present steps that clients can comply with to examine for weak sources inside their subscription.
- Disclosure of a CVE, or receipt of a message in Service Health concerning a CVE, doesn’t entail that any abuse or exploitation has taken place.
- The Security Update Guide from MSRC is the place new vulnerabilities are disclosed by Microsoft. CVEs within the Security Update Guide sometimes embody details about its exploitability and hyperlinks to the mandatory safety updates to stay safeguarded in opposition to it.
Customers are extremely inspired to configure Service Health alerts to be notified when a platform occasion impacts their Azure sources. You can obtain alerts via your most popular channel, together with SMS, e mail, and webhook. Microsoft values our ongoing collaboration with the safety analysis group to establish vulnerabilities in our services and products. We encourage all researchers to work with distributors below Coordinated Vulnerability Disclosure (CVD) and abide by the guidelines of engagement for penetration testing to keep away from impacting buyer information whereas conducting safety analysis.
[ad_2]
