[ad_1]
Authorities within the United States and United Kingdom at this time levied monetary sanctions towards seven males accused of working “Trickbot,” a cybercrime-as-a-service platform primarily based in Russia that has enabled numerous ransomware assaults and checking account takeovers since its debut in 2016. The U.S. Department of the Treasury says the Trickbot group is related to Russian intelligence providers, and that this alliance led to the focusing on of many U.S. firms and authorities entities.
Initially a stealthy computer virus program delivered by way of e mail and used to steal passwords, Trickbot developed into “a highly modular malware suite that provides the Trickbot Group with the ability to conduct a variety of illegal cyber activities, including ransomware attacks,” the Treasury Department stated.
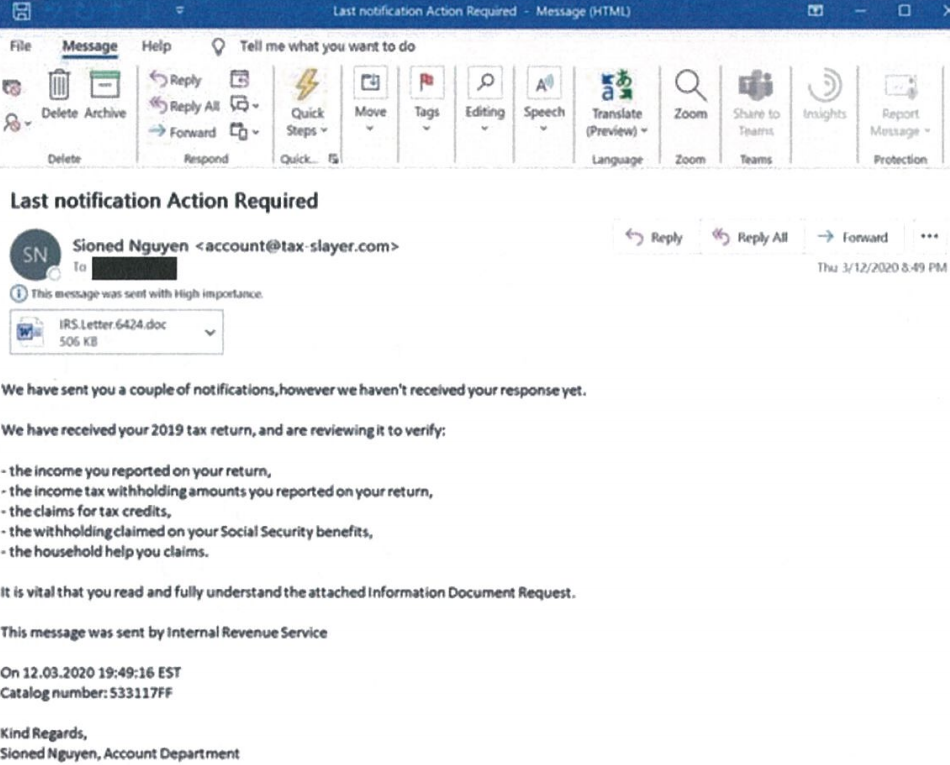
A spam e mail from 2020 containing a Trickbot-infected attachment. Image: Microsoft.
“During the height of the COVID-19 pandemic in 2020, Trickbot targeted hospitals and healthcare centers, launching a wave of ransomware attacks against hospitals across the United States,” the sanctions discover continued. “In one of these attacks, the Trickbot Group deployed ransomware against three Minnesota medical facilities, disrupting their computer networks and telephones, and causing a diversion of ambulances. Members of the Trickbot Group publicly gloated over the ease of targeting the medical facilities and the speed with which the ransoms were paid to the group.”
Only one of many males sanctioned at this time is thought to have been criminally charged in reference to hacking exercise. According to the Treasury Department, the alleged senior chief of the Trickbot group is 34-year-old Russian nationwide Vitaly “Bentley” Kovalev.
A New Jersey grand jury indicted Kovalev in 2012 after an investigation by the U.S. Secret Service decided that he ran a large “money mule” scheme, which used phony job gives to trick individuals into laundering cash stolen from hacked small to mid-sized companies within the United States. The 2012 indictment towards Kovalev pertains to cybercrimes he allegedly perpetrated previous to the creation of Trickbot.
BOTNET, THE MOVIE
In 2015, Kovalev reportedly started filming a film in Russia about cybercrime referred to as “Botnet.” According to a 2016 story from Forbes.ru, Botnet’s opening scene was to depict the plight of Christina Svechinskaya, a Russian pupil arrested by FBI brokers in September 2010.

Christina Svechinskaya, a cash mule employed by Bentley who was arrested by the FBI in 2010.
Svechinskaya was one in every of Bentley’s cash mules, most of whom had been younger Russian college students on non permanent journey visas within the United States. She was amongst 37 alleged mules charged with aiding a global cybercrime operation — mainly, organising phony company financial institution accounts for the only objective of laundering stolen funds.
Although she possessed no actual hacking expertise, Svechinskaya’s mugshot and social media photographs went viral on-line and she or he was shortly dubbed “the world’s sexiest computer hacker” by the tabloids.
Kovalev’s Botnet movie mission was disrupted after Russian authorities raided the movie manufacturing firm’s workplaces as a part of a cybercrime investigation. In February 2016, Reuters reported that the raid was linked to a crackdown on “Dyre,” a complicated trojan that U.S. federal investigators say was the precursor to the Trickbot malware. The Forbes.ru article cited sources near the investigation who stated the movie studio was working as a money-laundering entrance for the cybercrooks behind Dyre.
TREASON
But shifting political winds in Russia would quickly convey excessive treason prices towards three of the Russian cybercrime investigators tied to the investigation into the movie studio. In a serious shakeup in 2017, the Kremlin levied treason prices towards Sergey Mikhaylov, then deputy chief of Russia’s high anti-cybercrime unit.
Also charged with treason was Ruslan Stoyanov, then a senior worker at Russian safety agency Kaspersky Lab [the Forbes.ru report from 2016 said investigators from Mikhaylov’s unit and Kaspersky Lab were present at the film company raid].
Russian media shops have speculated that the lads had been accused of treason for serving to American cybercrime investigators pursue high Russian hackers. However, the fees towards each males had been categorised and have by no means been formally revealed. After their transient, closed trial, each males had been convicted of treason. Mikhaylov was given a 22 yr jail sentence; Stoyanov was sentenced to 14 years in jail.
In September 2021, the Kremlin issued treason prices towards Ilya Sachkov, previously head of the cybersecurity agency Group-IB. According to Reuters, Sachkov and his firm had been employed by the movie studio “to advise the Botnet director and writers on the finer points of cybercrime.” Sachkov stays imprisoned in Russia pending his treason trial.
A WELL-OILED CYBERCRIME MACHINE
Trickbot was closely utilized by Conti and Ryuk, two of Russia’s most ruthless and profitable ransomware teams. Blockchain evaluation agency Chainalysis estimates that in 2021 alone, Conti extorted greater than USD $100 million from its hacking victims; Chainalysis estimates Ryuk extorted greater than USD $150 million from its ransomware victims.
The U.S. cybersecurity agency CrowdStrike has lengthy tracked the actions of Trickbot, Ryuk and Conti beneath the identical moniker — “Wizard Spider” — which CrowdStrike describes as “a Russia-nexus cybercriminal group behind the core development and distribution of a sophisticated arsenal of criminal tools, that allow them to run multiple different types of operations.”
“CrowdStrike Intelligence has observed WIZARD SPIDER targeting multiple countries and industries such as academia, energy, financial services, government, and more,” stated Adam Meyers, head of intelligence at CrowdStrike.
This will not be the U.S. authorities’s first swipe on the Trickbot group. In early October 2020, KrebsOnSecurity broke the information that somebody had launched a sequence of coordinated assaults designed to disrupt the Trickbot botnet. Every week later, The Washington Post ran a narrative saying the assault on Trickbot was the work of U.S. Cyber Command, a department of the Department of Defense headed by the director of the U.S. National Security Agency (NSA).
Days after Russia invaded Ukraine in February 2022, a Ukrainian researcher leaked a number of years of inner chat logs from the Conti ransomware gang. Those candid conversations provide a captivating view into the challenges of working a sprawling felony enterprise with greater than 100 salaried staff. They additionally confirmed that Conti loved safety from prosecution by Russian authorities, so long as the hacker group took care to not goal Russian organizations.
In addition, the leaked Conti chats confirmed there was appreciable overlap within the operation and management of Conti, Trickbot and Ryuk.
Michael DeBolt, chief intelligence officer at cybersecurity agency Intel 471, stated the leaked Conti chats confirmed Bentley oversaw a workforce of coders tasked with guaranteeing that the Trickbot and Conti malware remained undetected by the completely different antivirus and safety software program distributors.
In the years previous to the emergence of Trickbot in 2016, Bentley labored intently on the Gameover ZeuS trojan, a peer-to-peer malware risk that contaminated between 500,000 and 1,000,000 computer systems with an automatic ransomware pressure referred to as Cryptolocker, DeBolt stated.
The FBI has a standing $3 million bounty provided for the seize of Evgeny “Slavik” Bogachev, the alleged creator of the Zeus trojan. And there are indications that Bentley labored instantly with Bogachev. DeBolt pointed to an October 2014 dialogue on the unique Russian hacking discussion board Mazafaka that included a grievance by a Russian internet hosting agency towards a discussion board consumer by the identify “Ferrari” who had did not pay a $30,000 internet hosting invoice.
In that dialogue thread, it emerged that the internet hosting firm thought it was submitting a grievance towards Slavik. But the Mazafaka member who vouched for Ferrari’s membership on the discussion board stated they knew Ferrari as Bentley the mule handler, and in some unspecified time in the future Slavik and Bentley should have been sharing the Ferrari consumer account.
“It is likely that Slavik (aka. Bogachev) and Bentley (aka. Kovalev) shared the same ‘Ferrari’ handle on the Mazafaka forum circa 2014, which suggests the two had a working relationship at that time, and supports the recent US and UK Government announcements regarding Kovalev’s past involvement in cybercrime predating Dyre or the Trickbot Group,” DeBolt stated.
CrowdStrike’s Meyers stated whereas Wizard Spider operations have considerably lowered following the demise of Conti in June 2022, at this time’s sanctions will possible trigger non permanent disruptions for the cybercriminal group whereas they search for methods to bypass the monetary restrictions — which make it unlawful to transact with or maintain the property of sanctioned individuals or entities.
“Often, when cybercriminal groups are disrupted, they will go dark for a time only to rebrand under a new name,” Meyers stated.
The prosecution of Kovalev is being dealt with by the U.S. Attorney’s Office in New Jersey. A replica of the now-unsealed 2012 indictment of Kovalev is right here (PDF).
