[ad_1]
A latest scoop by Reuters revealed that cellular apps for the U.S. Army and the Centers for Disease Control and Prevention (CDC) had been integrating software program that sends customer information to a Russian firm known as Pushwoosh, which claims to be based mostly within the United States. But that story omitted an vital historic element about Pushwoosh: In 2013, certainly one of its builders admitted to authoring the Pincer Trojan, malware designed to surreptitiously intercept and ahead textual content messages from Android cellular gadgets.
Pushwoosh says it’s a U.S. based mostly firm that gives code for software program builders to profile smartphone app customers based mostly on their on-line exercise, permitting them to ship tailored notifications. But a latest investigation by Reuters raised questions in regards to the firm’s actual location and truthfulness.
The Army informed Reuters it eliminated an app containing Pushwoosh in March, citing “security concerns.” The Army app was utilized by troopers at one of many nation’s principal fight coaching bases.
Reuters stated the CDC likewise just lately eliminated Pushwoosh code from its app over safety considerations, after reporters knowledgeable the company Pushwoosh was not based mostly within the Washington D.C. space — as the corporate had represented — however was as a substitute operated from Novosibirsk, Russia.
Pushwoosh’s software program additionally was present in apps for “a wide array of international companies, influential nonprofits and government agencies from global consumer goods company Unilever and the Union of European Football Associations (UEFA) to the politically powerful U.S. gun lobby, the National Rifle Association (NRA), and Britain’s Labour Party.”
The firm’s founder Max Konev informed Reuters Pushwoosh “has no connection with the Russian government of any kind” and that it shops its information within the United States and Germany.
But Reuters discovered that whereas Pushwoosh’s social media and U.S. regulatory filings current it as a U.S. firm based mostly variously in California, Maryland and Washington, D.C., the corporate’s workers are situated in Novosibirsk, Russia.
Reuters additionally realized that the corporate’s tackle in California doesn’t exist, and that two LinkedIn accounts for Pushwoosh workers in Washington, D.C. had been faux.
“Pushwoosh never mentioned it was Russian-based in eight annual filings in the U.S. state of Delaware, where it is registered, an omission which could violate state law,” Reuters reported.
Pushwoosh admitted the LinkedIn profiles had been faux, however stated they had been created by a advertising and marketing agency to drum up enterprise for the corporate — not misrepresent its location.
Pushwoosh informed Reuters it used addresses within the Washington, D.C. space to “receive business correspondence” in the course of the coronavirus pandemic. A evaluation of the Pushwoosh founder’s on-line presence through Constella Intelligence exhibits his Pushwoosh e-mail tackle was tied to a cellphone quantity in Washington, D.C. that was additionally related to e-mail addresses and account profiles for over a dozen different Pushwoosh workers.
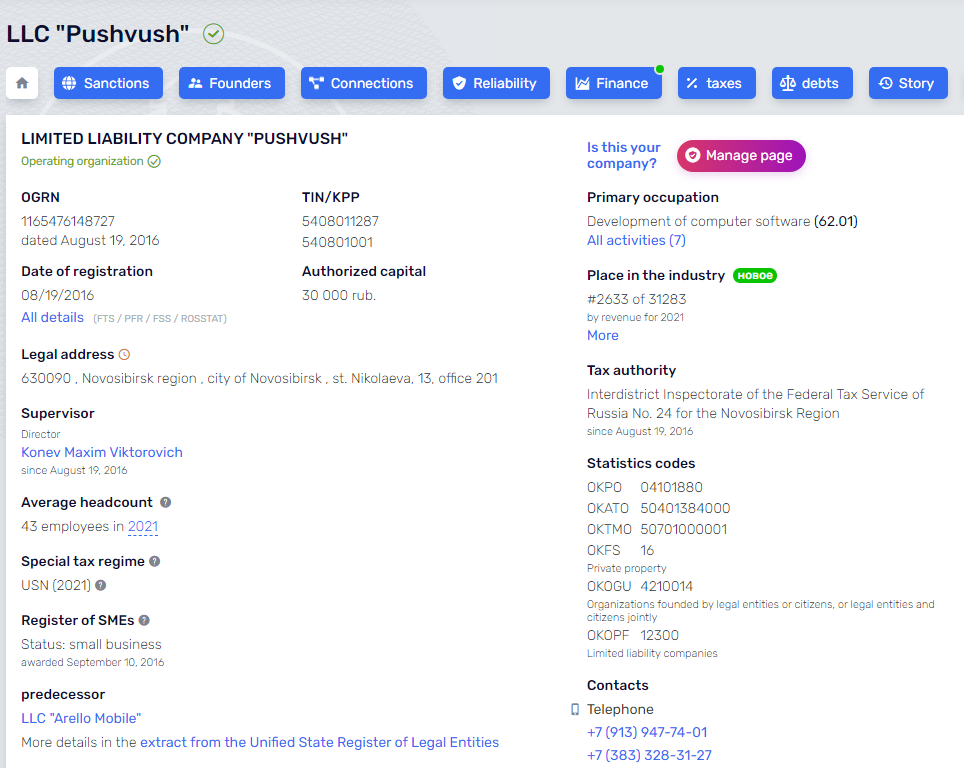
Pushwoosh was included in Novosibirsk, Russia in 2016.
THE PINCER TROJAN CONNECTION
The dust-up over Pushwoosh got here partially from information gathered by Zach Edwards, a safety researcher who till just lately labored for the Internet Safety Labs, a nonprofit group that funds analysis into on-line threats.
Edwards stated Pushwoosh started as Arello-Mobile, and for a number of years the 2 co-branded — showing facet by facet at varied know-how expos. Around 2016, he stated, the 2 firms each began utilizing the Pushwoosh title.
A search on Pushwoosh’s code base exhibits that one of many firm’s longtime builders is a 41-year-old from Novosibirsk named Yuri Shmakov. In 2013, KrebsOnSecurity interviewed Shmakov for the story, “Who Wrote the Pincer Android Trojan?” whereby Shmakov acknowledged writing the malware as a contract mission.
Shmakov informed me that, based mostly on the consumer’s specs, he suspected it’d in the end be put to nefarious makes use of. Even so, he accomplished the job and signed his work by together with his nickname within the app’s code.
“I was working on this app for some months, and I was hoping that it would be really helpful,” Shmakov wrote. “[The] idea of this app is that you can set it up as a spam filter…block some calls and SMS remotely, from a Web service. I hoped that this will be [some kind of] blacklist, with logging about blocked [messages/calls]. But of course, I understood that client [did] not really want this.”
Shmakov didn’t reply to requests for remark. His LinkedIn profile says he stopped working for Arello Mobile in 2016, and that he at the moment is employed full-time because the Android staff chief at a web-based betting firm.
In a weblog submit responding to the Reuters story, Pushwoosh stated it’s a privately held firm included below the state legal guidelines of Delaware, USA, and that Pushwoosh Inc. was by no means owned by any firm registered within the Russian Federation.
“Pushwoosh Inc. used to outsource development parts of the product to the Russian company in Novosibirsk, mentioned in the article,” the corporate stated. “However, in February 2022, Pushwoosh Inc. terminated the contract.”
However, Edwards famous that dozens of developer subdomains on Pushwoosh’s principal area nonetheless level to JSC Avantel, an Internet supplier based mostly in Novosibirsk, Russia.
WAR GAMES
Edwards stated the U.S. Army’s app had a customized Pushwoosh configuration that didn’t seem on another buyer implementation.
“It had an extremely custom setup that existed nowhere else,” Edwards stated. “Originally, it was an in-app Web browser, where it integrated a Pushwoosh javascript so that any time a user clicked on links, data went out to Pushwoosh and they could push back whatever they wanted through the in-app browser.”
An Army Times article revealed the day after the Reuters story ran stated at the very least 1,000 individuals downloaded the app, which “delivered updates for troops at the National Training Center on Fort Irwin, Calif., a critical waypoint for deploying units to test their battlefield prowess before heading overseas.”
In April 2022, roughly 4,500 Army personnel converged on the National Training Center for a struggle video games train on the way to use classes realized from Russia’s struggle towards Ukraine to organize for future fights towards a significant adversary corresponding to Russia or China.
Edwards stated regardless of Pushwoosh’s many prevarications, the corporate’s software program doesn’t seem to have executed something untoward to its clients or customers.
“Nothing they did has been seen to be malicious,” he stated. “Other than completely lying about where they are, where their data is being hosted, and where they have infrastructure.”
GOV 311
Edwards additionally discovered Pushwoosh’s know-how embedded in practically two dozen cellular apps that had been offered to cities and cities throughout Illinois as a approach to assist residents entry normal details about their native communities and officers.
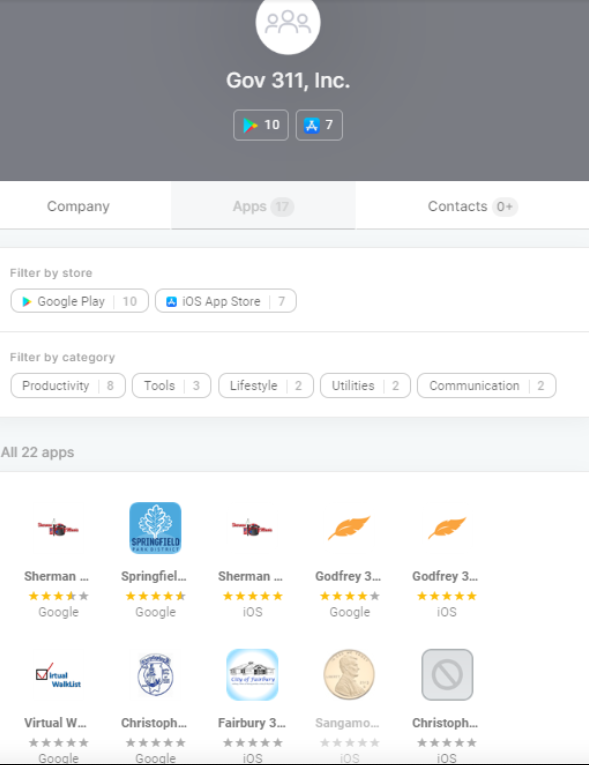 The Illinois apps that bundled Pushwoosh’s know-how had been produced by an organization known as Government 311, which is owned by Bill McCarty, the present director of the Springfield Office of Budget and Management. A 2014 story in The State Journal-Register stated Gov 311’s pricing was based mostly on inhabitants, and that the app would price round $2,500 per 12 months for a metropolis with roughly 25,000 individuals.
The Illinois apps that bundled Pushwoosh’s know-how had been produced by an organization known as Government 311, which is owned by Bill McCarty, the present director of the Springfield Office of Budget and Management. A 2014 story in The State Journal-Register stated Gov 311’s pricing was based mostly on inhabitants, and that the app would price round $2,500 per 12 months for a metropolis with roughly 25,000 individuals.
McCarty informed KrebsOnSecurity that his firm stopped utilizing Pushwoosh “years ago,” and that it now depends by itself know-how to offer push notifications by means of its 311 apps.
But Edwards discovered a number of the 311 apps nonetheless attempt to cellphone residence to Pushwoosh, such because the 311 app for Riverton, Ill.
“Riverton ceased being a client several years ago, which [is] probably why their app was never updated to change out Pushwoosh,” McCarty defined. “We are in the process of updating all client apps and a website refresh. As part of that, old unused apps like Riverton 311 will be deleted.”
FOREIGN ADTECH THREAT?
Edwards stated it’s removed from clear what number of different state and native authorities apps and Web websites depend on know-how that sends person information to U.S. adversaries abroad. In July, Congress launched an amended model of the Intelligence Authorization Act for 2023, which included a brand new part specializing in information drawn from on-line advert auctions that might be used to geolocate people or achieve different details about them.
Business Insider stories that if this part makes it into the ultimate model — which the Senate additionally has to move — the Office for the Director of National Intelligence (ODNI) can have 60 days after the Act turns into regulation to provide a threat evaluation. The evaluation will look into “the counterintelligence risks of, and the exposure of intelligence community personnel to, tracking by foreign adversaries through advertising technology data,” the Act states.
Edwards says he’s hoping these modifications move, as a result of what he discovered with Pushwoosh is probably going only a drop in a bucket.
“I’m hoping that Congress acts on that,” he stated. “If they were to put a requirement that there’s an annual audit of risks from foreign ad tech, that would at least force people to identify and document those connections.”
[ad_2]

