[ad_1]
Cybersecurity researchers have disclosed two high-severity safety flaws within the Ubuntu kernel that would pave the way in which for native privilege escalation assaults.
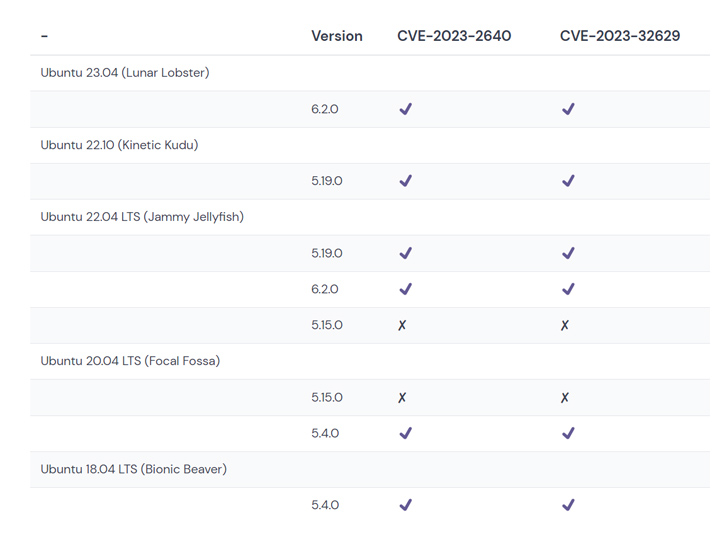
Cloud safety agency Wiz, in a report shared with The Hacker News, stated the easy-to-exploit shortcomings have the potential to influence 40% of Ubuntu customers.
“The impacted Ubuntu variations are prevalent within the cloud as they function the default working techniques for a number of [cloud service providers],” safety researchers Sagi Tzadik and Shir Tamari stated.
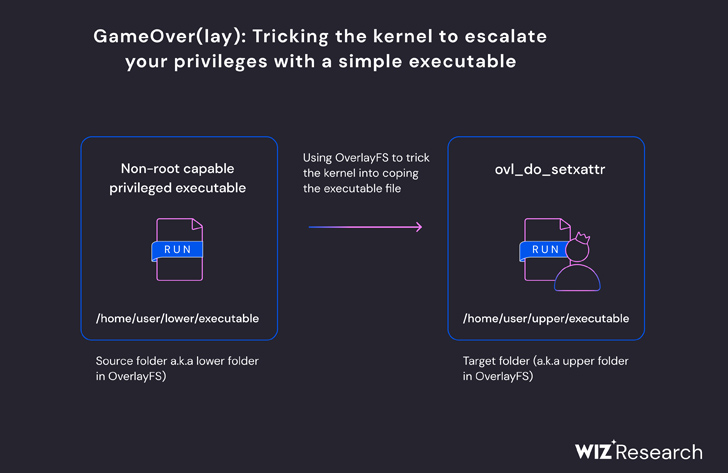
The vulnerabilities – tracked as CVE-2023-32629 and 2023-2640 (CVSS scores: 7.8) and dubbed GameOver(lay) – are current in a module known as OverlayFS and come up on account of insufficient permissions checks in sure situations, enabling a neighborhood attacker to achieve elevated privileges.
Overlay Filesystem refers to a union mount file system that makes it potential to mix a number of listing bushes or file techniques right into a single, unified filesystem.
A short description of the 2 flaws is beneath –
- CVE-2023-2640 – On Ubuntu kernels carrying each c914c0e27eb0 and “UBUNTU: SAUCE: overlayfs: Skip permission checking for trusted.overlayfs.* xattrs,” an unprivileged consumer could set privileged prolonged attributes on the mounted recordsdata, main them to be set on the higher recordsdata with out the suitable safety checks.
- CVE-2023-32629 – Local privilege escalation vulnerability in Ubuntu Kernels overlayfs ovl_copy_up_meta_inode_data skip permission checks when calling ovl_do_setxattr on Ubuntu kernels
In a nutshell, GameOver(lay) makes it potential to “craft an executable file with scoped file capabilities and trick the Ubuntu Kernel into copying it to a distinct
Shield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We’ve bought you lined! Join this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Security Posture Management.
location with unscoped capabilities, granting anybody who executes it root-like privileges.”
Following accountable disclosure, the vulnerabilities have been mounted by Ubuntu as of July 24, 2023.
The findings underscore the truth that refined modifications within the Linux kernel launched by Ubuntu may have unexpected implications, Wiz CTO and co-founder Ami Luttwak stated in an announcement shared with the publication.
“Both vulnerabilities are distinctive to Ubuntu kernels since they stemmed from Ubuntu’s particular person modifications to the OverlayFS module,” the researchers stated, including the problems are similar to different vulnerabilities similar to CVE-2016-1576, CVE-2021-3493, CVE-2021-3847, and CVE-2023-0386.
[ad_2]