[ad_1]
This report reveals cybercriminals want solely a pair days to entry your full company community and exfiltrate its information. Read on to be taught extra.

New analysis from Cybereason exposes how briskly cybercriminals will be in relation to exploit an preliminary an infection obtained on a company person.
SEE: Mobile gadget safety coverage (TechRepublic Premium)
Jump to:
What is the IcedID malware menace?
IcedID is a banking Trojan that has been actively utilized by cybercriminals since 2017 and shared a part of its code with one other broadly used malware household referred to as Pony, whose supply code leaked in 2015.
While principally distributed through spam emails constructed to contaminate customers, IcedID was additionally delivered at first of 2023 by a phishing marketing campaign pretending to unfold a Zoom software program replace.
IcedID has additionally regularly been distributed as payload, unfold by the notorious Emotet and Trickbot infrastructure, and to run ransomware assaults, as uncovered by the FBI.
IcedID: Initial level of compromise
In this assault marketing campaign, customers obtain and open a password protected archive containing an ISO file. Once the ISO file is clicked on, it creates a digital disk. If the person navigates and clicks on the one seen file, a Link File Format file, the LNK file begins the an infection course of by launching a batch file.
This drops a Dynamic Link Library file that’s executed in a brief listing. The DLL file then downloads the IcedID payload from a distant server and hundreds the payload into the method (Figure A).
Figure A
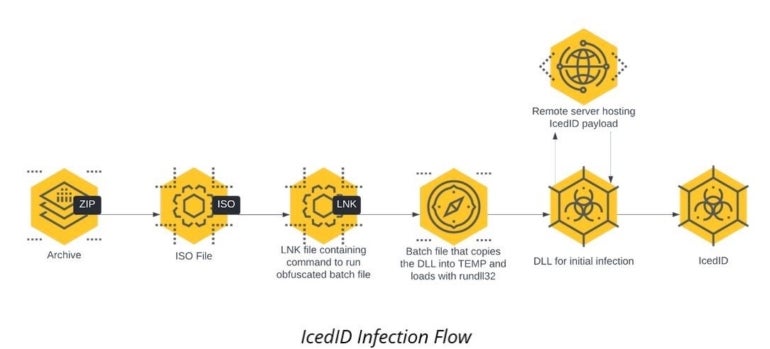
The malware then makes use of the professional internet.exe binary from the contaminated system to gather details about the area, workstation and members of the Domains Admins group.
Persistence is established by making a scheduled activity on the pc, which executes the malware each hour and at every logon operation.
The banking Trojan’s accelerated assault timeline
Cybereason researchers uncovered how briskly cybercriminals will be in relation to exploiting preliminary entry to an organization.
Once the preliminary IcedID an infection is completed, an interactive command line (cmd.exe) session is began, which downloads extra information on the contaminated system. Seven minutes after the preliminary an infection, a Cobalt Strike beacon is used on the contaminated laptop. The Cobalt Strike code hundreds Rubeus, a device designed for Kerberos interplay and abuse, which additionally collects extra community information from the system. Attackers get hold of the credentials of a service account through Kerberoasting, a identified approach based mostly on abusing legitimate Kerberos tickets, quarter-hour after the preliminary an infection.
57 minutes after the an infection, the lateral motion operation begins. The attacker makes use of the professional command line device ping.exe from the system to test if the host is alive, then executes the identical Cobalt Strike payload on the distant workstation through wmic.exe. That course of is repeated a number of instances, every time bouncing on a distinct endpoint or server. Large parts of the community infrastructure are scanned.
A DCSync assault is carried out 19 hours after the preliminary compromise. This approach permits an attacker to impersonate a site controller to acquire password hashes from different area controllers, enabling the attacker to extend their foothold on each area of the focused firm.
Shortly earlier than the exfiltration begins and 46 hours after the preliminary an infection, the attackers deploy the professional Atera distant administration device on a number of completely different machines. The implementation of that device on a number of computer systems permits the attackers to come back again to the system even when the IcedID malware is found and computer systems are cleaned from it.
How the malware steals your information
The IcedID malware hooks into a number of Internet browsers to steal credentials, session cookies and saved info. In addition, the attackers used the professional rclone wonderful syncing device to encrypt and ship a number of directories they selected to the Mega file sharing service. This information exfiltration begins roughly 50 hours after the preliminary compromise.
Cybereason reveals how briskly menace actors will be in relation to transferring laterally on completely different computer systems inside a goal community and exfiltrating information from them. While a number of of the reported strategies will be achieved mechanically with out human intervention, the lateral actions and the exfiltration phases want extra human energy. It is regarding to see {that a} menace actor can do all of this in solely 50 hours.
The report notes the ultimate step is information exfiltration, however the assault might simply result in a ransomware demand. The tooling and TTP described by Cybereason is harking back to the OnePercent group, which used IcedID, Cobalt Strike, PowerShell and Rclone in a way much like the actions documented on this report.
How to guard your group from this menace
Have all working techniques and software program updated and patched to forestall any compromise through the usage of a standard vulnerability. Do not permit customers on the community to open any ISO information until strictly wanted by customers. That file sort ought to solely be allowed for directors.
Finally, safety options have to be deployed on all endpoints and servers to detect suspicious conduct. Security consciousness must be supplied to all staff, particularly on electronic mail threats, which continues to be probably the most prevalent preliminary an infection vector.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
