[ad_1]
Five malicious dropper Android apps with over 130,000 cumulative installations have been found on the Google Play Store distributing banking trojans like SharkBot and Vultur, that are able to stealing monetary information and performing on-device fraud.
“These droppers proceed the unstopping evolution of malicious apps sneaking to the official retailer,” Dutch cellular safety agency ThreatFabric advised The Hacker News in a press release.
“This evolution consists of following newly launched insurance policies and masquerading as file managers and overcoming limitations by side-loading the malicious payload by the online browser.”
Targets of those droppers embrace 231 banking and cryptocurrency pockets apps from monetary establishments in Italy, the U.Ok., Germany, Spain, Poland, Austria, the U.S., Australia, France, and the Netherlands.
Dropper apps on official app shops like Google Play have more and more grow to be a preferred and environment friendly approach to distribute banking malware to unsuspecting customers, even because the menace actors behind these campaigns frequently refine their techniques to bypass restrictions imposed by Google.
The listing of malicious apps, 4 of that are nonetheless out there on the digital market, is beneath –
The newest wave of SharkBot assaults aimed toward Italian banking customers because the begin of October 2022 entailed using a dropper that masqueraded as an to find out the tax code within the nation (“Codice Fiscale 2022”).
While Google’s Developer Program Policy limits using the REQUEST_INSTALL_PACKAGES permission to forestall it from being abused to put in arbitrary app packages, the dropper, as soon as launched, will get round this barrier by opening a pretend Google Play retailer web page impersonating the app itemizing, resulting in the obtain of the malware underneath the guise of an replace.
Outsourcing the malware retrieval to the browser will not be the one technique adopted by felony actors. In one other occasion noticed by ThreatFabric, the dropper posed as a file supervisor app, which, per Google’s revised coverage, is a class that is allowed to have the REQUEST_INSTALL_PACKAGES permission.
Also noticed have been three droppers that provided the marketed options but additionally got here with a covert perform that prompted the customers to put in an replace upon opening the apps and grant them permission to put in apps from unknown sources, resulting in the supply of Vultur.
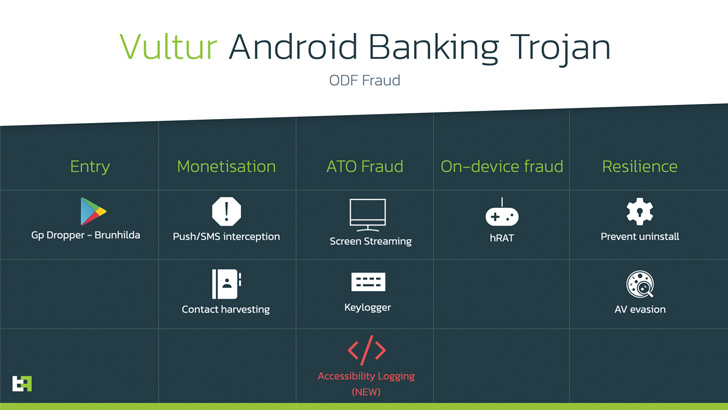
The new variant of the trojan is notable for including capabilities to extensively log person interface components and interplay occasions (e.g., clicks, gestures, and so forth.), which ThreatFabric stated could possibly be a workaround to using the FLAG_SECURE window flag by banking apps to forestall them from being captured in screenshots.
The findings from ThreatFabric additionally come as Cyble uncovered an upgraded model of the Drinik Android trojan that targets 18 Indian banks by impersonating the nation’s official tax division app to siphon private data by the abuse of the accessibility companies API.
“Distribution by droppers on Google Play nonetheless stays essentially the most ‘inexpensive’ and scalable approach of reaching victims for a lot of the actors of various ranges,” the corporate famous.
“While refined techniques like telephone-oriented assault supply require extra sources and are onerous to scale, droppers on official and third-party shops enable menace actors to succeed in a large unsuspecting viewers with affordable efforts.”