[ad_1]
Ransomware: up to date threats, methods to forestall them and the way the FBI can assist
In April 2021, Dutch supermarkets confronted a meals scarcity. The trigger wasn’t a drought or a sudden surge within the demand for avocados. Rather, the rationale was a ransomware assault. In the previous years, firms, universities, colleges, medical services and different organizations have been focused by ransomware risk actors, turning ransomware into the web’s most extreme safety disaster.
The Ransomware Landscape
Ransomware has existed for greater than 30 years, but it surely grew to become a profitable supply of revenue for cyber actors and gangs prior to now decade. Since 2015, ransomware gangs have been concentrating on organizations as a substitute of people. Consequently, ransom sums have elevated considerably, reaching thousands and thousands of {dollars}.
Ransomware is efficient as a result of it pressures victims in two, complementary methods. First, by threatening victims to destroy their information. Second, by threatening to publicize the assault. The second risk has an oblique impression, but it’s simply as severe (if no more). Publication may set off regulatory and compliance points, in addition to unfavorable long-term model results.
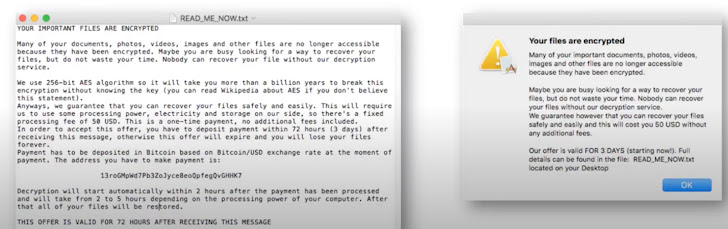
Here are some examples of actual ransomware notes:
Ransomware as a Service (RaaS) has develop into essentially the most widespread kind of ransomware. In RaaS assaults, the ransomware infrastructure is developed by cyber criminals after which licensed out to different attackers for his or her use. The buyer attackers will pay for the usage of software program or they’ll cut up the loot with the creators. Etay maor, Senior Director Security Strategy at Cato Networks commented, “There are different types of RaaS. After receiving the ransomware fee some Ransomware teams promote all the info concerning the sufferer’s community to different gangs. This means the subsequent assault is far easier and could be absolutely automated because it doesn’t require weeks of discovery and community evaluation by the attackers.”
Some of the most important RaaS gamers, who’re infamous for turning the RaaS panorama into what it’s right this moment, are CryptoLocker, who contaminated over 1 / 4 million methods within the 2000s and profited greater than $3 million in lower than 4 months, CryptoWall, who revamped $18 million and prompted an FBI advisory, and at last Petya, NotPetya and WannaCry who used numerous varieties of exploits, ransomware included.
How the FBI Helps Combat Ransomware
An group beneath assault is certain to expertise frustration and confusion. One of the primary beneficial programs of motion is to contact an Incident Response workforce. The IR workforce can help with investigation, recuperation and negotiations. Then, the FBI can even assist.
Part of the FBI’s mission is to boost consciousness about ransomware. Thanks to a large native and world community, they’ve entry to worthwhile intelligence. This info can assist victims with negotiations and with operationalization. For instance, the FBI would possibly have the ability to present profiler details about a risk actor primarily based on its Bitcoin pockets.
To assist ransomware victims and to stop ransomware, the FBI has arrange 56 Cyber Task Forces throughout its area places of work. These Task Forces work intently with the IRS, the Department of Education, the Office of Inspector General, the Federal Protective Service and the State Police. They’re additionally in shut contact with the Secret Service and have entry to regional forensics labs. For National Security cyber crimes, the FBI has a chosen Squad.
Alongside the Cyber Task Force, the FBI operates a 24/7 CyWatch, which is a Watch Center for coordinating the sector places of work, the personal sector and different federal and intelligence companies. There can also be an Internet Crime Complaint Center, ic3.gov, for registering complaints and figuring out developments.
Preventing Ransomware Attacks On Time
Many ransomware assaults haven’t got to achieve the purpose the place the FBI is required. Rather, they are often prevented beforehand. Ransomware isn’t a single-shot assault. Instead, a collection of techniques and methods all contribute to its execution. By figuring out the community and safety vulnerabilities prematurely that permits the assault, organizations can block or restrict risk actors’ means to carry out ransomware. Etay Maor added “We must rethink the idea that “the attackers should be proper simply as soon as, the defenders should be proper on a regular basis”. A cyber assault is a mix of a number of techniques and methods. As such, it might solely be countered with a holistic method, with a number of converged safety methods that every one share context in actual time. This is precisely what a SASE structure, and no different, provides the defenders”.
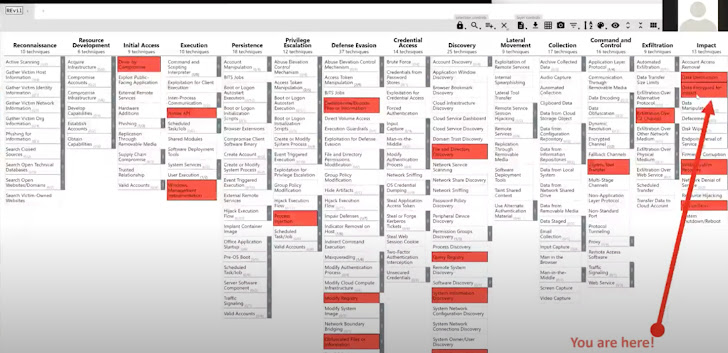
For instance, listed below are all of the steps in a REvil assault on a well known producer, mapped out to the MITRE ATT&CK framework. As you may see, there are quite a few phases that occurred earlier than the precise ransom and have been important to its “success”. By mitigating these dangers, the assault might need been prevented.
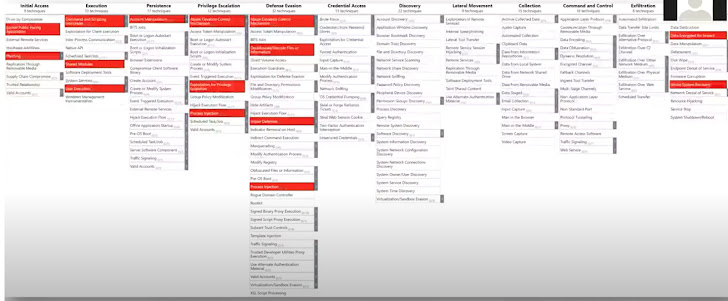
Here is an identical mapping of a Sodinokobi assault:
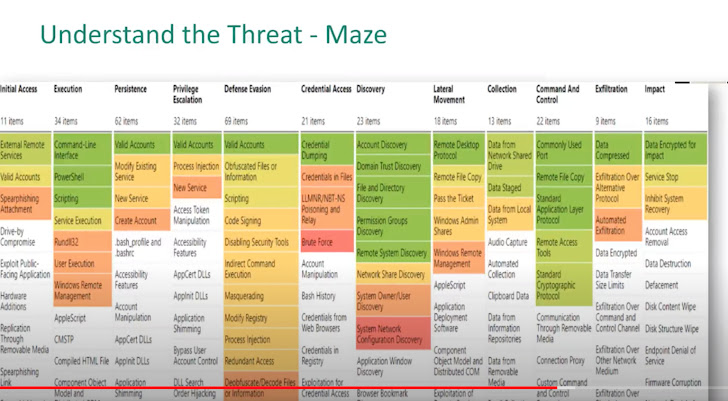
Maze assault mapping to the MITRE framework:
Another method to map ransomware assaults is thru warmth maps, which present how usually completely different techniques and methods are used. Here is a warmth map of Maze assaults:
One manner to make use of these mappings is for community evaluation and methods testing. By testing a system’s resilience to those techniques and methods and implementing controls that may mitigate any dangers, organizations cut back the chance of a ransomware assault by a sure actor on their vital assets.
How to Avoid Attacks – From the Horse’s Mouth
But do not take our phrase for it. Some ransomware attackers are “sort” sufficient to offer organizations with finest practices for securing themselves from future ransomware assaults. Recommendations embody:
- Turning off native passwords
- Using safe passwords
- Forcing the top of admin classes
- Configuring group insurance policies
- Checking privileged customers’ entry
- Ensuring solely mandatory purposes are working
- Limiting the reliance of Anti-Virus
- Installing EDRs
- 24 hour system admins
- Securing weak ports
- Watching for misconfigured firewalls
- And extra
Etay Maor of Cato Networks highlights “Nothing in what a number of Ransomware teams say organizations must do is new. These finest practices have been mentioned for years. The motive they nonetheless work is that we attempt to apply them utilizing disjoint, level options. That did not work and won’t work. A SASE, cloud native, structure, the place all safety options share context and have the aptitude to see each networks circulate and get a holistic view of the assault lifecycle can stage the taking part in area in opposition to cyber assaults”.
Ransomware Prevention: An Ongoing Activity
Just like brushing your tooth or exercising, safety hygiene is an ongoing, methodical apply. Ransomware attackers have been identified to revisit the crime scene and demand a second ransom, if points have not been resolved. By using safety controls that may successfully mitigate safety threats and having a correct incident response plan in place, the dangers could be minimized, in addition to the attackers’ pay day. The FBI is right here to assist and supply info that may help, let’s hope that help will not be wanted.
To study extra about ransomware assaults and methods to forestall them, Cato Networks’ Cyber Security Masterclass collection is on the market to your viewing.