[ad_1]
One of the oldest malware methods within the e-book — hacked web sites claiming guests must replace their Web browser earlier than they will view any content material — has roared again to life up to now few months. New analysis reveals the attackers behind one such scheme have developed an ingenious means of maintaining their malware from being taken down by safety specialists or legislation enforcement: By internet hosting the malicious information on a decentralized, nameless cryptocurrency blockchain.
In August 2023, safety researcher Randy McEoin blogged a few rip-off he dubbed ClearFake, which makes use of hacked WordPress websites to serve guests with a web page that claims that you must replace your browser earlier than you may view the content material.
The pretend browser alerts are particular to the browser you’re utilizing, so for those who’re browsing the Web with Chrome, for instance, you’ll get a Chrome replace immediate. Those who’re fooled into clicking the replace button can have a malicious file dropped on their system that tries to put in an data stealing trojan.
Earlier this month, researchers on the Tel Aviv-based safety agency Guardio stated they tracked an up to date model of the ClearFake rip-off that included an necessary evolution. Previously, the group had saved its malicious replace information on Cloudflare, Guardio stated.
But when Cloudflare blocked these accounts the attackers started storing their malicious information as cryptocurrency transactions within the Binance Smart Chain (BSC), a know-how designed to run decentralized apps and “smart contracts,” or coded agreements that execute actions routinely when sure situations are met.
Nati Tal, head of safety at Guardio Labs, the analysis unit at Guardio, stated the malicious scripts stitched into hacked WordPress websites will create a brand new sensible contract on the BSC Blockchain, beginning with a novel, attacker-controlled blockchain deal with and a set of directions that defines the contract’s features and construction. When that contract is queried by a compromised web site, it should return an obfuscated and malicious payload.
“These contracts offer innovative ways to build applications and processes,” Tal wrote alongside together with his Guardio colleague Oleg Zaytsev. “Due to the publicly accessible and unchangeable nature of the blockchain, code can be hosted ‘on-chain’ without the ability for a takedown.”
Tal stated internet hosting malicious information on the Binance Smart Chain is right for attackers as a result of retrieving the malicious contract is a cost-free operation that was initially designed for the aim of debugging contract execution points with none real-world influence.
“So you get a free, untracked, and robust way to get your data (the malicious payload) without leaving traces,” Tal stated.
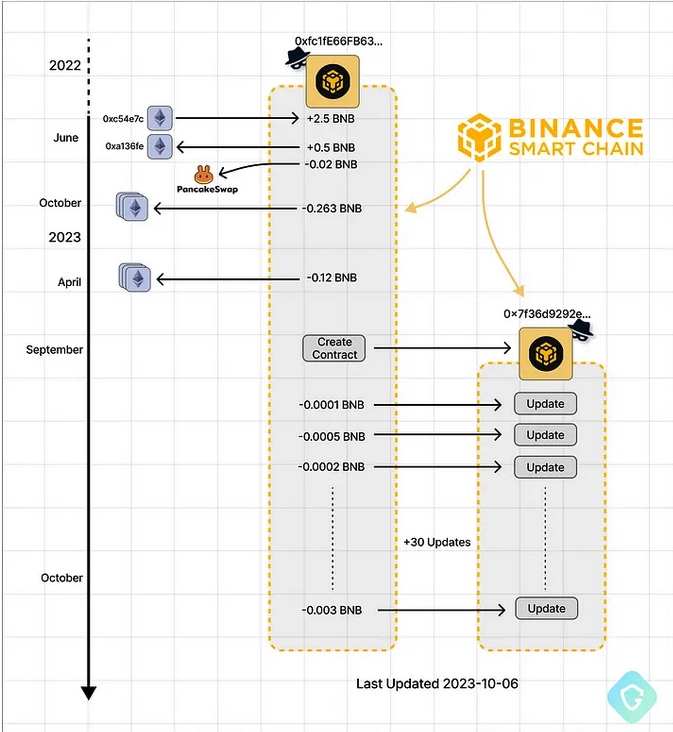
Attacker-controlled BSC addresses — from funding, contract creation, and ongoing code updates. Image: Guardio
In response to questions from KrebsOnSecurity, the BNB Smart Chain (BSC) stated its workforce is conscious of the malware abusing its blockchain, and is actively addressing the difficulty. The firm stated all addresses related to the unfold of the malware have been blacklisted, and that its technicians had developed a mannequin to detect future sensible contracts that use related strategies to host malicious scripts.
“This model is designed to proactively identify and mitigate potential threats before they can cause harm,” BNB Smart Chain wrote. “The team is committed to ongoing monitoring of addresses that are involved in spreading malware scripts on the BSC. To enhance their efforts, the tech team is working on linking identified addresses that spread malicious scripts to centralized KYC [Know Your Customer] information, when possible.”
Guardio says the crooks behind the BSC malware scheme are utilizing the identical malicious code because the attackers that McEoin wrote about in August, and are doubtless the identical group. But a report revealed as we speak by e-mail safety agency Proofpoint says the corporate is at present monitoring not less than 4 distinct risk actor teams that use pretend browser updates to distribute malware.
Proofpoint notes that the core group behind the pretend browser replace scheme has been utilizing this method to unfold malware for the previous 5 years, primarily as a result of the strategy nonetheless works effectively.
“Fake browser update lures are effective because threat actors are using an end-user’s security training against them,” Proofpoint’s Dusty Miller wrote. “In security awareness training, users are told to only accept updates or click on links from known and trusted sites, or individuals, and to verify sites are legitimate. The fake browser updates abuse this training because they compromise trusted sites and use JavaScript requests to quietly make checks in the background and overwrite the existing website with a browser update lure. To an end user, it still appears to be the same website they were intending to visit and is now asking them to update their browser.”
More than a decade in the past, this web site revealed Krebs’s Three Rules for Online Safety, of which Rule #1 was, “If you didn’t go looking for it, don’t install it.” It’s good to know that this technology-agnostic strategy to on-line security stays simply as related as we speak.
[ad_2]
