[ad_1]
There are 3 components of cybersecurity. If you’re lacking any
one in every of them, you might be making your self a straightforward goal for knowledge thieves
and sure buying a one-way ticket to a world of harm.
You could be questioning if that is one thing you actually want to fret about. Well, Embroker requested enterprise house owners that precise factor. In their current Cyber Risk Index Report, founders in 2022 admitted that they had been far more fearful about cyber assaults than they had been within the earlier 12 months.
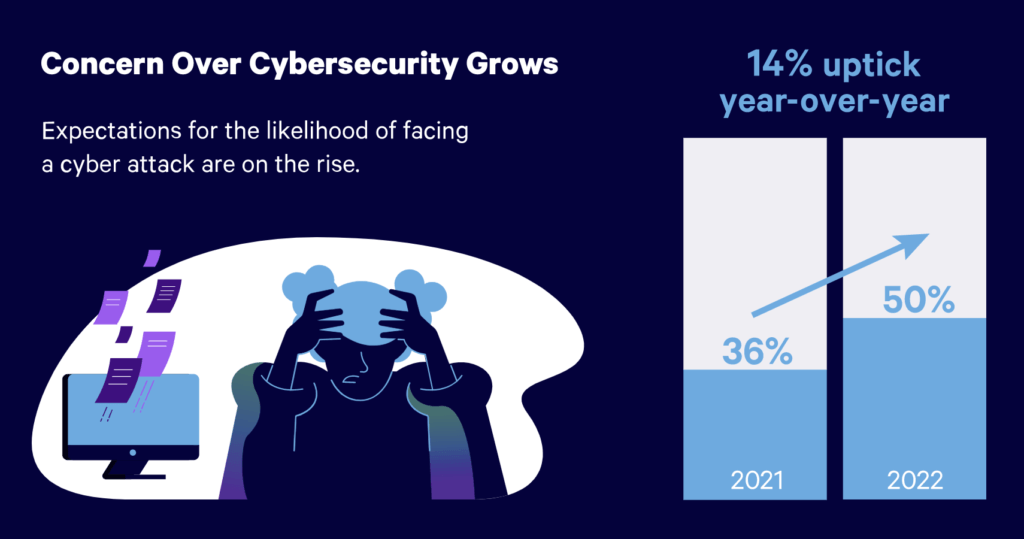
Check out the total report for extra particulars.
The 3 components of cybersecurity are prevention, detection, and response. Within every of
these are particular steps it’s worthwhile to take to provide your self the very best likelihood of
foiling cybercriminals who need your knowledge—particularly, your consumer’s names,
addresses, Social Security numbers, checking account particulars, taxpayer
info, and varied different secrets and techniques, together with confidential
correspondences, statements in opposition to curiosity, and your pre-trial technique
notes.
These are knowledge you have got an obligation to safeguard, and breaching that responsibility
carries with it some disagreeable penalties. For instance, it may price you
a ton of cash to pay out to injured purchasers. It may price you your repute
since an information breach isn’t something you possibly can conceal—when it occurs, you have got
an ethical obligation and nearly certainly a statutory one as nicely to publicly
disclose that confidential knowledge entrusted to you have got been compromised.
And a breach of the responsibility to safeguard consumer info as outlined in Rule
1.6(c) of the American Bar Association’s Model Rules of Professional
Responsibility may price you your regulation license, both briefly or
completely.
So, with out additional fanfare, let’s have a look at the three parts of
cybersecurity. We start with arguably crucial of the three components of cybersecurity: the ingredient of prevention.
The 3 Elements of Cybersecurity: Prevention
When it involves cybersecurity, the previous saying about an oz of prevention
being value a pound of treatment is totally true. Indeed, probably the most cost-
efficient (and sanity-sparing) manner of saving your self from the results
of a cyberattack shouldn’t be permitting it to happen.
Here’s what you need to do if you wish to stop a cyberattack.
The first order of enterprise—and that is super-important, which is why I’m
telling you about it proper up entrance—procure a cyber-insurance coverage. Do not
depend on some other type of insurance coverage to guard your self from the
penalties of a cyberattack. Cyber-insurance is the one kind of protection
that may maintain you from going underneath financially due to a knowledge breach.
Granted, this insurance coverage received’t cease hackers and different malefactors from
efficiently dipping their sticky fingers into your jar of honey-sweet knowledge,
but it surely’s an important safety measure, nonetheless.
Next, get within the behavior of being stingy with the quantity of data you
share on-line. The much less you share, the higher since you by no means know who
would possibly lurk within the digital shadows to spy in your e-mail exchanges and
web site visits. Say “no thanks” when the little popup in your display invitations
you to share location knowledge. Decline the supply to simply accept cookies, if attainable.
Frequently run safety scans of your methods. Ensure your pc’s
working system, browsers, packages, and all the things else is updated.
That means it’s worthwhile to have the newest model of every put in. You additionally
ought to have the most recent safety patches in place. Cobwebbed software program is
often a critical vulnerability.
From there, apply a scrutinizing eye to all of your passwords. If you’re utilizing
weak passwords, cease. Swap them out for brand new and powerful passwords. A weak
password is one thing alongside the strains of 123456. A powerful password
accommodates a randomized mixture of upper- and lower-case letters plus numerals
and particular characters. Your greatest guess is to amass a password administration
app—it’ll mechanically create hyper-strong passwords, and no two will ever
be the identical. The password supervisor can even keep in mind each for you,
so that you’ll by no means want to put in writing them down. One thing more: activate multi-
issue authentication (MFA), which would require you to supply no less than one
extra piece of proof to show you’re who you declare to be (and never
some hacker who managed to pilfer your password) earlier than it can roll out the
welcome mat and grant you entry.
Start utilizing a digital personal community (VPN) everytime you hop onto the
web, whether or not to ship an e-mail or go to an internet site. Backup your information
often: as soon as a day is sweet, as soon as a minute is right (there are safety
packages you possibly can get hold of that may mechanically backup your information for you
and, as a bonus, encrypt them—encryption being an impressive solution to
frustrate cybercriminals).
Finally, to actually get a grasp of learn how to stop a cyber assault (in addition to the three components of cybersecurity) join cybersecurity coaching—not only for your self however everybody
in your workplace. With coaching, you’ll discover ways to spot phishing scams, e-mail
compromise assaults, and different types of trickery designed to lull you into
freely giving your entry credentials or unwittingly initiating a lethal
obtain of viruses or malware. Training can even instill in you and your
workforce quite a few good habits, resembling not sharing private passwords and
by no means leaving the desk with out first locking the pc display.
The 3 Elements of Cybersecurity: Detection
Cyberthieves are so good at what they do this it usually takes the sufferer
200 days to appreciate an information breach has occurred. It takes that lengthy as a result of
the common sufferer isn’t sufficiently vigilant in watching out for the indicators of a
cyberattack.
Therefore, you need to evaluation your financial institution and bank card statements recurrently.
Also, take a extra frequent have a look at what the credit score bureaus (Equifax,
TransUnion, and Experian) are saying about you—for instance, are they
reporting that you simply’ve taken out a mortgage you recognize nothing about or have
moved to a brand new handle in a location you’ve by no means a lot as visited?
Those are indicators you’ve been knowledge breached.
Pay nearer consideration to how your computer systems and cell units are
behaving. Be suspicious in the event that they’re all of a sudden operating gradual or doing
inexplicable bizarre issues—likelihood is they’re contaminated with viruses or
malware, or maybe a hacker has burrowed in and brought management.
Another signal of a cyberattack is that you simply’ll begin to obtain emails seemingly
from colleagues and others with whom you have got a trusted relationship.
These emails will seem genuine however are literally from cybercrooks doing a
actually good impersonation of your colleague. The giveaway that they’re
frauds is that you simply’ll be requested to share your login credentials with them or to
pay this bill for one thing you recognize you paid months in the past.
The 3 Elements of Cybersecurity: Response
The sooner you shift into response mode after a cyberattack is detected, the
higher off you’ll be. It will assist in the event you took time in the course of the prevention section
to create an motion plan detailing your response so that you simply and your workforce
know precisely what to do and through which order. No guessing, no operating round
together with your hair on fireplace.
In the occasion of a breach, instantly contact your cyber-insurance firm
to allow them to start coming to your assist with the money and different help you
might want to keep away from monetary and reputational destroy.

Industry-leading safety on your tech firm.
Get the best protection at the very best worth.
This subsequent step, some say, needs to be carried out earlier than you contact your
cyber-insurance firm, whereas others say to do it proper after. Either manner,
it’s worthwhile to seal off your methods from the surface world in order that no additional
knowledge loss can happen. That means chopping your web connections and killing
your community feed. Please don’t return on-line till a pc safety
specialist or IT-managed service supplier sift by your methods with a
fine-tooth comb to find out the way you had been breached after which plug that
gap.
Then you have to start the method of notifying all affected events—first and
foremost, your purchasers. You have to inform them that you simply had been the sufferer of a
knowledge breach and clarify how that occasion impacts them. It’s a wise transfer to
embody in that notification a promise to pay for credit score monitoring in order that
these impacted by the breach will likely be well timed alerted if their stolen private
info is subsequently used to have interaction in monetary crimes.
The relaxation is fairly simple. Contact regulation enforcement to allow them to know
what occurred. Ditto Social Security, your financial institution, and your collectors so that they
can put holds in your accounts and challenge new ones.
And there you have got it. The 3 components of cybersecurity; are
prevention, detection, and response. You want all three in place if you would like
to return out on the opposite facet of an information breach, a phishing rip-off, a
ransomware assault, or the rest cyber-based together with your funds, consumer
roster, model repute, and probably even your regulation license intact.

Is cyber danger on the rise?
Read our 2022 Cyber Risk Index Report to search out out what companies are fearful about, how they’re defending themselves, and what the long run holds.

Tom Lambotte
CEO of Boba Guard
This article was offered by Tom Lambotte, a cybersecurity skilled who has been within the tech help business for over a decade. Tom based BobaGuard in 2019, which provides turnkey options to solo legal professionals and small-to-medium regulation companies. In addition, Tom can be the CEO and Founder of GlobalMac IT, a longtime managed service supplier specializing in serving legal professionals nationwide who use Macs by implementing his Proven Process™.
