[ad_1]
We current the Active Adversary Report for Security Practitioners, analyzing information amassed by Sophos’ Incident Response group and masking the six quarters ending June 2023. This is the third and closing Active Adversary Report of the yr.
Our earlier 2023 experiences, which have been geared towards enterprise leaders (April) and tech leaders (August), targeted on broad tendencies in attacker conduct. This report will dive deeper into matters that have been famous however not beforehand highlighted, bringing forth findings that, although fascinating from any cybersecurity standpoint, are almost definitely to be actionable for safety practitioners.
Unlike enterprise leaders or tech leaders, who’re primarily targeted on technique, operations, and useful resource deployment (each human and monetary), practitioners are targeted on finer particulars and actionable intelligence with which to guard the group. Among the roles generally dealt with by practitioners, menace hunters do the forward-facing work that, when finished effectively, ensures the group sees round corners when it must. And responders look backward to grasp what occurred on programs in disaster whilst they scramble to get the state of affairs again beneath management, and stop related outcomes sooner or later.
Key Takeaways
- Urgency on the a part of the attackers doesn’t (essentially) represent an emergency on the a part of defenders
- Attack speeds change; assault instructions and processes don’t
- Bad system hygiene issues extra in quick occasions
- To decelerate rushing assaults, simply add some friction
- Defenders, a TAC!
Where the info comes from
The Active Adversary Reports current what the X-Ops’ Incident Response (IR) group has discovered in regards to the present adversary panorama from tackling safety crises all over the world. This version of the report is anchored in information from 232 instances chosen from the info obtainable from January 1, 2022 to June 30, 2023. We present extra element on the demographics represented on this evaluation on the finish of the report.
This version of the report expands our view to incorporate data from X-Ops’ Managed Detection and Response (MDR) group, together with a take a look at how that group frames their menace intelligence work when it comes to Threat Activity Clusters (TACs). To illustrate one distinction in perspective the MDR group will carry to those experiences going ahead, this version features a side-by-side comparability of two instances – one touching an present MDR buyer, one coming to Sophos by means of Incident Response. The assaults have been related on the outset, however we’ll present that the paths to wellness have been very completely different.
Hunting High and Low
Security practitioners come from numerous backgrounds and fill an ever-growing roster of roles and capabilities in at the moment’s organizations. As we assembled the findings on this report, we targeted on menace hunters, analysts, and incident responders, and the way they could use the knowledge contained in a long-form report resembling this. We’ll take a second firstly of this report to stipulate what meaning.
Once completely the area of governments and enormous enterprises, menace searching is turning into extra commonplace in safety groups because the operate matures and demonstrates its worth. Not everybody studying this report might be as intimately conversant in this specialised function as they’re with incident response or with the various varieties of research. As such, we’ll try to summarize the menace hunter’s function as clearly and succinctly as potential.
One of the tenets of menace searching is to “assume breach” and systematically go attempting to find present threats within the atmosphere. This requires full telemetry of the atmosphere, since attackers will discover and conceal in your blind spots. (That’s in the event that they don’t create the blind spot within the first place, which itself is an indicator of compromise [IoC]. More on that later within the report.) Early detection of potential threats permits for faster response, which often results in higher outcomes for the group.
Threat hunters are each shoppers and producers of menace intelligence; the sharing of intelligence inside circles {of professional} belief contained in the group is without doubt one of the nice success tales of cybersecurity tradition. Threat intelligence could be something from a extremely granular indicator resembling an IP deal with or a file hash to broader campaign-level demographics. As the identify implies, menace hunters actually comb by means of information in an atmosphere, searching for these indicators of compromise. Existing IoCs inform the hunt, and new IoCs are added to the ever-expanding universe of menace intelligence information.
Another approach that menace intelligence is gathered and fortified is thru the work of incident responders. Unlike menace searching, which is a proactive self-discipline, incident responders’ work is usually reactive. They examine detected breaches and ongoing energetic assaults with the target of containing and mitigating the harm attributable to safety incidents, and returning the affected programs to a working state as rapidly as potential. Incident response could be initiated by telemetry, from proactive menace hunts, or because of different procedural or institutional triggers.
When responding to an energetic menace, it’s crucial that the time between recognizing the preliminary indicator of compromise and full menace mitigation be as transient as potential. As an adversary progresses by means of the phases of an assault, it’s a race towards time to stop them from reaching their goals – and the deeper the adversary will get within the assault chain, the more severe the defender’s prospects of catching up. With that long-understood fact in thoughts, the invention within the earlier report that dwell occasions have telescoped appeared to spell potential mayhem for defenders. This report is an effort to higher perceive, on the practitioner degree, the place that’s and isn’t the case.
Movin’ Too Fast?
In the newest Active Adversary report, we highlighted the precipitous decline in dwell time for all assaults. In explicit, we famous a 44% year-on-year and 72% all-time drop in dwell time for ransomware assaults. These decreases have been particularly eye-catching with ransomware assaults, the dwell time of which decreased to a median of 5 days. One of our conclusions is that not solely do ransomware attackers know that detection capabilities have improved, necessitating faster assaults, however many are merely well-practiced.
They’ve had steerage. In the wake of the Conti leaks of early 2022, our menace researchers noticed that many ransomware operators and associates have been adopting the very well-developed playbooks authored by the infamous group. As with any course of, iteration and apply tends to result in higher outcomes. With fashionable ransomware turning 10 years outdated this yr, apply has definitely made a few of them proficient. This is doubly true when many defensive methods haven’t saved tempo.
It is with the ominous ransomware dwell-time decline in thoughts that we started to have a look at attacker dwell occasions within the five-days-or-less class. To make sure of the statistical significance of the dataset and to grasp how these “fast” assaults develop, we selected to incorporate all assaults we investigated in 2022 and the primary six months of 2023, leaving out a single DDoS case that for numerous causes didn’t lend itself to helpful evaluation right here.
We first requested whether or not there are notable variations about sooner assaults. The quick reply is not any. Most assaults, whether or not “fast” or “slow,” don’t seem to have any vital markers, aside from velocity, that will inform a change in protection technique.
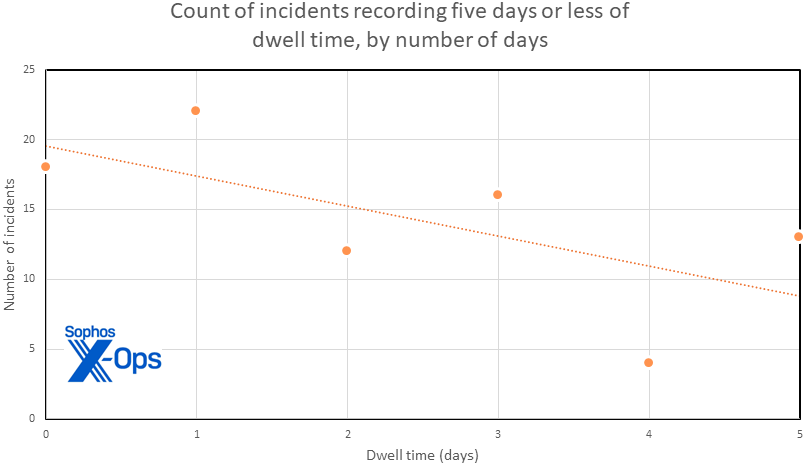
The first step to understanding the state of affairs is to dig into the info. As proven in Figure 1, the distribution of assaults by dwell time provides a glimpse into the decline highlighted in our earlier reporting. Even on this 18-month dataset, we will clearly see that longer assaults pattern downwards. They’re merely not as frequent.
Figure 1: In this distribution of dwell occasions throughout the primary 5 days of our quickest instances, there’s a reasonably even (however declining) incidence of time spent in sufferer networks. There’s a reasonably sturdy inverse pattern seen between the size (in days) of dwell time and the variety of instances confirming to that size of time
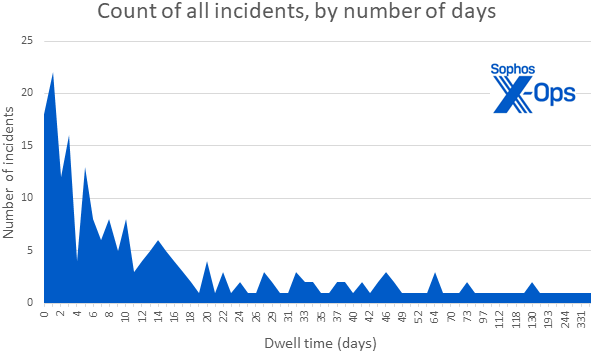
Looking additional on the dataset, we see in Figure 2 that the pattern of declining continues into the lengthy tail of dwell time, with 50% of all assaults occurring inside 9 days or much less of preliminary entry.
Figure 2: Incidents with dwell occasions of a month or extra nonetheless happen, however they’re very a lot not the norm within the 18-month dataset. (Note that the X-axis scale reveals incidence and isn’t to scale)
We then sorted our 18-month dataset into assaults with a dwell time of 5 days or much less and assaults that lasted greater than 5 days, in an effort to evaluate assault sorts, instruments detected, LOLBin (living-off-the-land binary) use detected, and noticed methods to see what variations may be discoverable. We have been searching for sorts of findings that may very well be strongly related to both quick or gradual assaults — or that may very well be equally related to both kind.
The information sorted into one group of 85 instances with dwell time of 5 days or much less, 141 instances with dwell occasions of over 5 days, and 6 instances for which inadequate proof existed to find out dwell time. (Such instances often contain a telemetry failing, as we’ll talk about later within the report.) The instances during which dwell time couldn’t be decided have been excluded from the dwell-time evaluation that follows, leaving a dataset of 226 instances.
Fast and gradual vs assault sorts
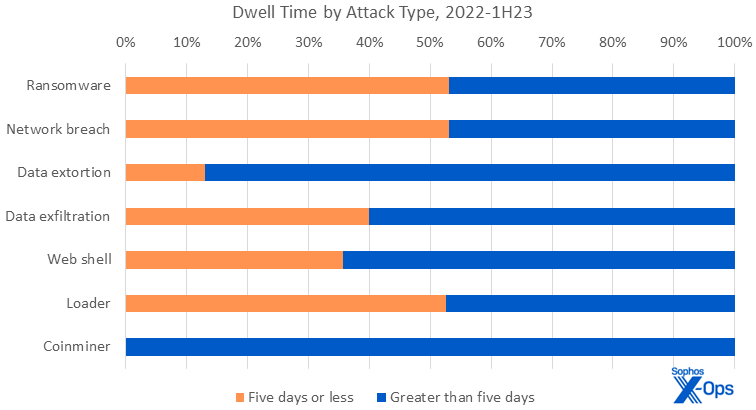
Focusing our consideration on assault sorts, we start to see in Figure 3 how “fast” assaults (<= 5 days dwell time) don’t fluctuate considerably in kind from “slow” ones (>5 days dwell time) for essentially the most half.
Figure 3: For ransomware, community breach, and loader assaults, it’s actually about fifty-fifty whether or not dwell time is quick (5 days or much less) or gradual (longer than 5 days). Web shells and information exfiltration assaults are barely extra prone to have longer dwell occasions, and each information extortion and coinmining usually tend to have longer dwell occasions
Ransomware assaults, nonetheless essentially the most prevalent kind of assault, are distributed evenly throughout the info set of 226 instances. An identical commentary could be made regarding (in descending order) community breach, loaders, information exfiltration, and net shells.
Amongst the outliers, coinminers are skewed by their low incidence in our dataset, but in addition by the truth that they’re meant to be long-running. Coinminers will fortunately squat on a server, accruing fractions of a cent monthly, in perpetuity. #web3isgoinggreat
Of observe is the info extortion class, during which most however not all assaults fell into the “slower” dataset. In an extortion, the menace actors have a tendency to stay longer within the community than in instances when information is solely exfiltrated however no extortion is tried. We consider that since there isn’t a encryption part to those assaults, the menace actors are capable of function extra silently, and subsequently extra slowly and intentionally. This is all too usually abetted by the goal’s personal ignorance on what their baseline visitors appears to be like like — encryption creates substantial load on a system, however easy exfiltration with out encryption doesn’t, that means that exercise could also be much less noticeable. The downside is compounded when the goal doesn’t monitor outbound visitors. In many instances, attackers have been capable of exfiltrate giant portions of knowledge with out discover.
Data exfiltration, a variation on information extortion (all extortions contain exfiltration of some type; however not all exfiltrations embody extortion), additionally suggestions barely within the favor of longer assaults, for related causes. (“Data exfiltration” in our dataset signifies instances during which the info was confirmed to have left the affected community, however no additional data is accessible as to what the attacker did with that information.)
Web shells, whether or not the work of preliminary entry brokers (IABs) or dropped in assist of another type of marketing campaign, signify one other class for which dwell occasions are anticipated to be longer.
Fast and gradual vs root causes
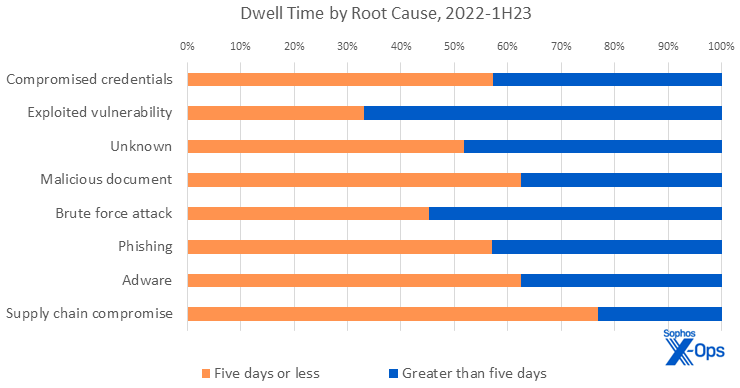
We flip our consideration subsequent to root causes, taking a look at which if any are extra carefully related to sooner or with slower assaults.
Figure 4: In these instances for which assaults may very well be ascribed to root causes, some fascinating correlations between trigger and period grew to become evident
The root causes of assaults present higher distribution. Compromised credentials, which rocketed to the highest of the root-cause chart within the first half of 2023, have a slight prevalence in sooner assaults. This is usually because of the reality that there have been additionally a better proportion of quick assaults within the first six months of 2023.
Likewise, the incidents for which the foundation trigger was a malicious doc, phishing, adware, or a supply-chain compromise have been extra prone to transfer quickly. On the opposite hand, about two-thirds of the assaults with roots in exploit of a system vulnerability have been “slow” assaults, which once more maps to that class’s lower within the 2023 assault statistics. Unfortunately, the “unknown” class, which covers assaults for which the foundation trigger can’t be derived from obtainable information, nonetheless plagues each side of the velocity equation.
The notable outlier on this view of the info is provide chain assaults. Supply chain compromises are the ready meal kits of threats — all of the substances are there and it’s only a matter of creating it occur. For instance, Sophos incident responders investigated a knot of three associated Hive ransomware incidents in 2022 that exemplify this situation.
Those incidents began with compromised credentials getting used towards a single-factor VPN resolution. Two-way belief relationships between all three domains meant that the compromised credentials have been legitimate throughout the affected organizations, and protracted tunnels meant entry was available. When the assaults began in earnest, the was little or no time between them: Only 11 hours separated the abuse of the stolen credentials and protracted VPN tunnels. On the opposite finish of the assault, there have been lower than 6 hours between ransomware deployments. In two of the instances, information was stolen a couple of day earlier than the ransomware was deployed.
The administrative perils of supply-chain relationships are a subject greatest left for a later version of this report. For practitioners, although, this story shouldn’t be solely an instance of how this type of assault can rip by means of a number of estates at high velocity, however a reminder that offer chains pose extra dangers and alternatives for defenders, which we’ll contact on later.
Where we observe essentially the most uniform distribution between quick and gradual incidents is within the instruments, LOLBins, and particularly the methods utilized by attackers. The following part compares the highest 5 outcomes for quick and gradual assaults in every of those three classes, ranked by prevalence. (Why are there greater than 5 gadgets in every checklist? The fifth merchandise in some lists was truly additional down the comparability desk. We embody them to make sure the highest 5 gadgets for each quick and gradual assaults are represented in every class, and supply every desk for readability.)
Fast and gradual vs the artifacts
As in earlier experiences, we glance as soon as once more on the mostly famous artifacts seen within the information. Both the April and August experiences go into vital element about these datasets. Since they’re nearly unchanged because the August report, we’ll focus this time on evaluating artifacts in quick and gradual assaults.
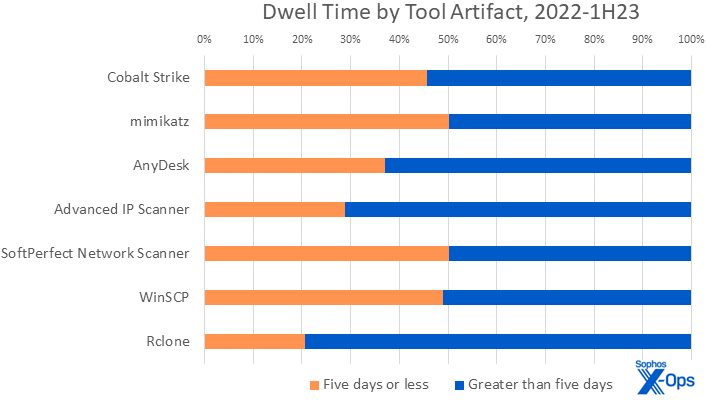
Figure 5: Of the instruments mostly introduced onto the goal community and deployed by attackers, there’s vital distinction in utilization between quick and gradual assaults for under a handful of artifacts
| 2022-1H23 Tools Occurrence (by rank) | |||
| Rank | Five days or much less | Greater than 5 days | Rank |
| 1 | Cobalt Strike | Cobalt Strike | 1 |
| 2 | mimikatz | AnyDesk | 2 |
| 3 | AnyDesk | mimikatz | 3 |
| 4 | SoftPerfect Network Scanner | Advanced IP Scanner | 4 |
| 5 | WinSCP | Rclone | 5 |
| 8 | Advanced IP Scanner | SoftPerfect Network Scanner | 7 |
| 18 | Rclone | WinSCP | 14 |
All 226 instances on this dataset included a minimum of one artifact of device use. Most of the instruments have been evenly distributed between sooner and slower assaults. Mainstays resembling Cobalt Strike, mimikatz, and AnyDesk occupied their pure spots within the high three of each lists, matching their rating on the all-time checklist. Other attacker favorites, Advanced IP Scanner and SoftPerfect’s Network Scanner, fourth and fifth respectively on the all-time checklist, additionally ranked extremely; instruments resembling community scanners are steadily (ab)utilized by attackers and their prevalence shifts over time, as we see right here, however stay fixed in the long term. File switch instruments WinSCP and Rclone spherical out the highest 5.
As talked about, the third most (ab)used device in quick assaults (and all-time) is AnyDesk. Interestingly, the longer assaults used it greater than the shorter ones. Generally, longer assaults see extra use of distant entry instruments than sooner ones. Remote entry instruments make up 40% of the highest 10 instruments versus 20% for quick assaults. (Perhaps sooner assaults – significantly ones involving extortion reasonably than simply encryption — don’t have as excessive a necessity for persistence, particularly if you already know you gained’t be contained in the community very lengthy?)
Slight variations may also be seen within the alternative of exfiltration instruments. While WinSCP sees even utilization between quick and gradual assaults, practitioners will discover that Rclone is much much less generally seen in quick assaults. While we will’t actually know why, it’s potential that Rclone’s considerably much less pleasant interface makes it a much less appropriate candidate for smash-and-grab-style assaults. (On the opposite hand, WinSCP is well-suited to the type of assaults that merely exfiltrate to attacker-controlled infrastructure; maybe Rclone’s simply too subtle for the smash-and-grab crowd. This is a superb instance of 1 indicator of compromise hinting at a number of potential strains of threat-hunter inquiry.) There have been additionally extra exfiltration makes an attempt within the slower assaults, which implies extra alternative to make use of a various toolset.
In the ultimate two comparisons, we see that the LOLBins and methods getting used don’t fluctuate considerably between quick and gradual assaults. Frankly, they merely work and there’s no incentive to alter them till they cease working. Cybercriminals solely innovate once they should, and solely to the extent that it will get them to their goal. For instance, multifactor authentication (MFA) bypasses have been round for a while. It wasn’t till extra organizations began deploying MFA (albeit solely essentially the most primary types, resembling SMS-based or TOTP), that we began seeing earnest makes an attempt at circumvention. And as extra phishing-resistant types of MFA grow to be commonplace, so will cookie stealing and authentication token theft.
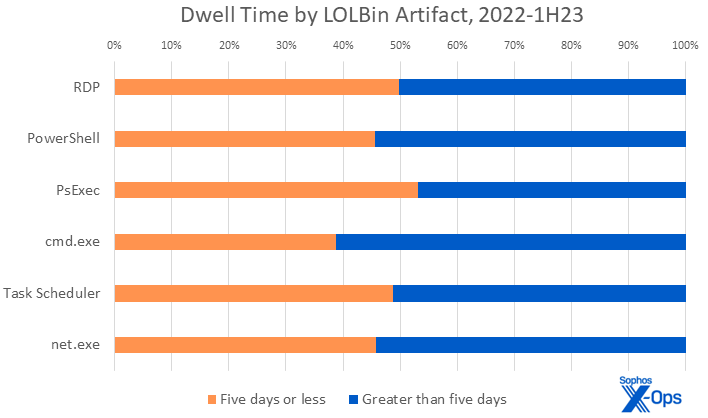
Figure 6: Just as the recognition rankings for LOLBins not often change in our information, one can fairly anticipate to see the identical binaries abused whether or not the assault is quick or gradual
| 2022-1H23 LOLBin Occurrence (by rank) | |||
| Rank | Five days or much less | Greater than 5 days | Rank |
| 1 | RDP | RDP | 1 |
| 2 | PowerShell | PowerShell | 2 |
| 3 | PsExec | Cnd.exe | 3 |
| 4 | Cmd.exe | PsExec | 4 |
| 5 | Task Scheduler | internet.exe | 5 |
| 6 | internet.exe | Task Scheduler | 6 |
In this dataset, 218 instances included a minimum of one artifact of LOLBin abuse. The majority of essentially the most generally abused LOLBins are commandeered as a result of they’re helpful and customary, so it needs to be to nobody’s shock that Remote Desktop Protocol (RDP) comes out on high in both rating. With some slight variations within the percentages, the remaining LOLBins observe effectively inside statistical variability. Practitioners ought to anticipate LOLBin exploitation to stay comparatively steady over time; when wanting on the high 20 LOLBins in both quick or gradual assaults, 90% happen in each lists, and occupy the identical spot of their respective rankings.
The class exhibiting essentially the most parity between quick and gradual assaults is the catchall “Techniques” (or ‘Other”) category – showing, once more, that whether the attackers are fast or slow, they are still recognizably the same attacks. To discern differences, we’ll want to determine the fundamentals after which get extra granular.
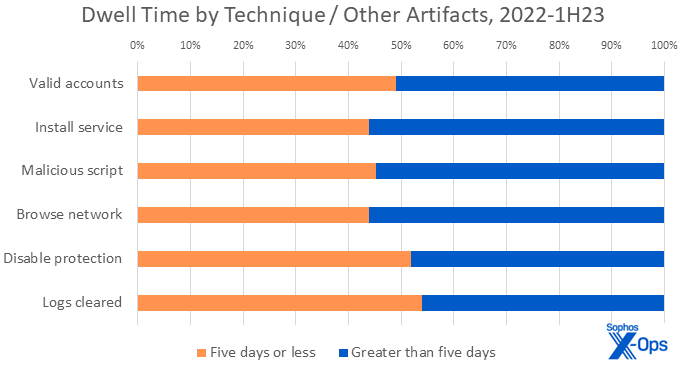
Figure 7: A chart with all of the tidal variation of a accumulate pond, the distribution of methods seen in quick and gradual assault is nearly the identical
| 2022-1H23 Techniques (“Other”) Occurrence (by rank) | |||
| Rank | Five days or much less | Greater than 5 days | Rank |
| 1 | Valid accounts | Valid accounts | 1 |
| 2 | Install service | Install service | 2 |
| 3 | Malicious scripts | Malicious scripts | 3 |
| 4 | Disable safety | Browse community | 4 |
| 5 | Logs cleared | Disable safety | 5 |
| 6 | Browse community | Logs cleared | 6 |
In this dataset, all instances included a minimum of one artifact of different device or approach use. Valid accounts, as an example, are helpful irrespective of the velocity of the attacker. We famous in our August report that we noticed legitimate accounts have been paired with exterior distant providers 70% of the time. In this comparability we noticed the identical pairing, however in several proportions for quick or gradual assaults: Fast assaults noticed the paring 75% of the time, in comparison with 62% for slower assaults. In the quick instances the place legitimate accounts have been used, 88% didn’t have MFA configured. Having legitimate credentials makes illicit entry simple; not having to take care of MFA makes it trivial. And once more, as with LOLBins, the methods in each lists don’t fluctuate a lot. There is an 80% overlap between the highest lists of quick or gradual assaults.
We conclude that with a number of exceptions, the instruments and methods noticed in quick assaults mirror the sort and proportion of these seen in longer assaults.
In our earlier report, we talked about that attackers are more and more disabling safety as a method of evading detection, however it has the facet impact of decreasing telemetry, placing defenders on the again foot. It’s with that in thoughts that we determined to look again on the 2023 information to see the state of logging inside organizations.
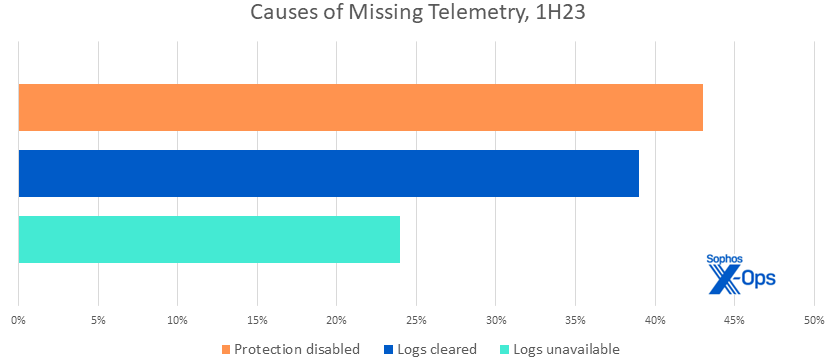
Figure 8: Missing telemetry complicates response and protection; a fast examination of the 1H23 information reveals numerous causes it was not obtainable to investigators for instances throughout that timeframe. Since a couple of purpose could be true in any given assault, the chances add as much as effectively over one hundred pc
Alarmingly, almost 1 / 4 of the organizations we investigated merely didn’t have acceptable logging obtainable for incident responders. This was resulting from a wide range of components, together with inadequate retention, re-imaging, or lack of configuration. In an investigation, not solely would this imply the info can be unavailable for examination, however the defenders must spend time determining why it wasn’t obtainable.
Now that Microsoft has (as of September 2023) begun to make logging free and obtainable for primary licenses, there’s no purpose to not use it to its fullest when it’s rolled out to your enterprise. Hands-on practitioners will not be able to determine this for his or her enterprises, however it’s necessary that they make the case if the case isn’t being made by management. And, like many different sorts of information, logs needs to be securely backed up to allow them to be used within the occasion {that a} forensic evaluation is required. (The basic confidentiality-integrity-availability trinity shouldn’t be often top-of-mind for the practitioner crowd, however it’s price invoking right here to talk the management language that’ll get the required processes in place.)
Zero
OK, so there’s no discernible distinction in the best way assaults unfold on the day scale, however there have to be after we take a look at hours, proper? While the story of 2023 to date has been velocity, taking a look at ever smaller time slices doesn’t reveal something revolutionary. The demographics of the sooner assaults mirror these over an extended time scale, as do the assault sorts and root causes. Ransomware nonetheless dominates (61%) and compromised credentials (44%) are the main root trigger adopted by exploited vulnerabilities (22%). Nearly three-quarters of instances abused RDP and the rankings for instruments, LOLBins and methods are almost an identical to their longer cousins.
So, if the ever-shrinking time scales don’t change our method to protection, what does? In quick, it comes all the way down to having eyes on the atmosphere and performing rapidly when issues floor. Whether that’s from an energetic menace hunt or an alert from one in every of your safety merchandise. There is a world of distinction between these organizations that actively monitor and reply to IoCs and those that don’t. Don’t blame your self for what you may’t ignore. Instead, discover a technique to shut the hole between your present capabilities and the place you must be. And, with respect to Zeno’s paradox, whereas excellent detection can by no means be achieved, you’ll by no means be sorry that you simply tried to be as observant and as thorough as you may.
sTACed Actors
Of course it’s simple to say in a report like this that practitioners needs to be observing as a lot as they will as totally as they will. The downside is discovering methods to take action successfully, since even when the traces of assaults (quick or gradual) haven’t actually modified, the amount of fabric to parse will increase continuously. A carefully associated downside includes efficient information sharing. Even if one practitioner has helpful observations and data, what’s the best technique to convey these to others engaged on related issues, ideally in a approach that helps defenders draw additional helpful data from that work?
To remedy this downside in our personal analysis, Sophos in 2023 has been build up a Threat Activity Cluster (TAC) nomenclature. We wrote about this a number of months in the past, and supply a bit extra data on the method on this report for defenders curious to be taught extra.
Rather than making an attempt to establish particular adversaries after which accruing information about each’s TTPs, TACs focus much less on the who and extra on the what, on the speculation that defending towards the “what” (tightly associated TTPs and victimology, time-date proximity) will cowl whoever the “who” could also be.
So far this has been a productive method for our personal menace hunters and intel analysts. TAC considering permits us to rapidly spot patterns even when a number of the matches in obtainable information are a bit “fuzzy,” and lets us see by means of attacker shenanigans resembling adjustments in device utilization, or teams that break up and reassemble beneath one other identify (however do the identical outdated assaults in the identical outdated approach; most attacker teams are in spite of everything completely satisfied to reuse the identical outdated TTPs so long as they’re working). TAC considering additionally helps us to have a look at analysis from trade friends and see beforehand unnoticed relationships and evolutions.
The nomenclature itself is splendidly boring. As clusters of behaviors are recognized, they’re given a four-digit quantity, the primary digit of which signifies broadly what the cluster was concerned in (or, for those who choose, the motivation of the conduct). So far:
1 – State-Sponsored
2 – Hacktivist
3 – Initial Access Broker
4 – Financially Motivated (eg., malicious promoting)
5 – Ransomware
6 – Unknown (an identifiable cluster of behaviors exists, however extra analysis is required)
Focusing on what clusters of findings do, reasonably than the place or with whom they could originate, permits the group to see stunning issues. These embody our just lately printed findings on a serious change in tooling for the Vice Society gang (which is now, as our analysis reveals, extra accurately described because the Rhysida gang). More broadly, clustering implies that threat-actor attribution doesn’t overshadow different artifacts resembling device use or assault kind. This leads us to fascinating webs of correlation amongst these three datasets.
Our desire for TACs is to not say that different, adversary-centered defenders are doing it incorrect; the one approach to do that type of menace evaluation incorrect is in actual fact to insist that there’s Only One True Way. That mentioned, it’s most likely excessive time for the trade to stroll again from a number of the adversary-naming excesses of years previous, nevertheless thrilling these are for advertising functions. (Frankly, comic-book supervillain names like Magical Stinkbug or Flouncy Koala give the dangerous guys extra glamour and attraction than they deserve.) TACs lack flamboyance, however they greater than compensate in actionable data.
As talked about above, the method of including our MDR group’s perspective to our historically IR-centered Active Adversary Reports has been an interesting train. As an instance, we current right here a side-by-side comparability of two instances – a twin detective story, if you’ll. One case touched an present MDR buyer, one got here to Sophos by means of Incident Response.
Watching The Detectives
Our story begins in Cuba – or a minimum of within the Cuba ransomware, the infectant in each the instances we’ll evaluation. Both instances occurred in 2023 and each affected US-based entities (albeit in several enterprise sectors). For simplicity, we’ll name them “Red” and “Blue,” and since it is a story for safety practitioners, we’ll instantly spoil the ending by telling you the way it labored out for every case.
| Red Got and Blue: A Tale of Two Cuba Attacks | |
|
“Red” |
“Blue” |
| 8 artifacts logged | 203 artifacts logged |
| 2 gadgets affected | 215 gadgets affected |
| 0 accounts compromised | 9 accounts compromised |
| 2 servers remoted | All servers and PCs remoted |
| 2 days to BAU (Business As Usual) | 60+ days to BAU |
| No information exfiltrated | 75GB exfiltrated |
| Data leaked on menace actor’s web site | |
The Beginning
The first hour of the primary day began off a lot the identical for Red and Blue, with protection evasion makes an attempt together with the motive force C:WindowsTempaswArPot.sys. (This exploit is understood for terminating processes on the kernel degree.)
What Red Saw: The attacker additionally tried to load a second file, C:WindowsTempav.bat. Sophos Anti-Virus detected and terminated / deleted each makes an attempt.
What Blue Saw: The attacker tried to execute different defense-evasion methods. At this level, the system data later made obtainable to Sophos X-Ops investigators indicated {that a} Cobalt Strike C2 had simply dropped, and there are additionally authorizations from an unmanaged IP deal with.
Setting Up Shop, Or Not
The first hour has handed. The two paths start to diverge, as Cuba makes an attempt to completely set up itself. On each programs, throughout the subsequent 60 minutes three extra IoCs (C:WindowsTemp130.bat, C:WindowsTemp130.dll, C:WindowsTempauto.dll) execute, adopted by tried outreach to 38.135.122.[.]130/Agent64.bin – a Cuba ransomware C2.
What Red Saw: The mixture of the file executions plus the recognized Cuba C2 deal with are sufficient proof for MDR, and the system generates a case for SOPHOS-DET-WINDOWS-BEHAVIORAL-MALWARE-C2_11a (T1071.001). (The MITRE ATT&CK notation on the finish tells observers that the flagged conduct includes application-level protocols related to net visitors.)
What Blue Saw: Nothing, however behind the scenes the menace actor is busy – dropping extra ransomware binaries and (probably) compromising an admin-level consumer. More malicious instruments and LOLBin utilization might be seen within the logs, significantly AVKill and PSExec. Blue has a number of Sophos instruments in place right here and there, resembling CryptoGuard, however its alerts at the present time on Cobalt Strike and KillAV go unnoted.
A Three-Hour Tour
Three hours have handed because the begin of every incident; enter Sophos people, a minimum of on one facet of the equation.
What Red Saw: After isolating two suspicious-looking hosts on the client’s community, an MDR analyst reaches out to let the client know what has taken place, and to suggest that they block the detected C2s. The malicious information are taken off the affected gadgets and submitted to SophosLabs for additional scrutiny.
What Blue Saw: No formal monitoring was in place, however in accordance with reconstructions of the timeline and interviews after the very fact with the focused enterprise, the indicators of hassle (particularly, Cobalt Strike) have been already getting some in-house consideration. PSExec is now current on affected gadgets, and SSL-encrypted visitors is flowing to Russian IP addresses. At this level telemetry additionally signifies the attacker had reached Blue’s Active Directory, an indication of hassle we talked an excellent deal about in our final report.
Go On Without Me
Two days have handed. This is the place Red’s story ends. Blue’s is simply starting.
What Red Saw: In the intervening days, the 2 affected servers on the buyer property are cleaned up and despatched again into use. The ransomware is eradicated; no information encryption or exfiltration happened, and the client is again to enterprise as standard.
What Blue Saw: By now, the attackers have compromised a number of consumer accounts and are phoning house to 2 extra C2s related to the Cuba marketing campaign. Over the subsequent two weeks, the attackers will attain out to a different IP deal with (64.235.39[.]82) to obtain extra malware. They’ll additionally unfold extra malicious binaries throughout the property, together with the Backstab binary, which terminates privileged system processes; a batch script to put in KillAV and disable no matter antimalware protections could also be operating; and a further piece of malware concentrating on Microsoft ZeroLogon vulnerabilities. (The KillAV try raised one other flag with the Sophos wares on the system, however once more there was no follow-up.) System directors are conscious one thing’s not proper. They’ll discover out what quickly.
Making Themselves Known
Two weeks have handed. During an in a single day shift, an worker at Blue discovered their information encrypted; they alerted the helpdesk. When a second division reported related hassle close to the tip of that shift, Blue reached out to Sophos X-Ops IR. Within a number of hours, the Sophos IR group began its investigation.
What Blue Saw: Blue’s IT division is by now half a depressing month into taking part in whack-a-mole — blocking binaries, figuring out a minimum of one compromised account, and determining which machines have been secretly permitting RDP entry to the community. However, when customers began discovering information encrypted and sporting a brand new .cuba file extension, they referred to as exterior IR. As IR and the brand new buyer scramble to establish affected infrastructure, crown jewels, and what logs and backups could also be obtainable, it’s found that just about 80GB of so-far-unidentified information was exfiltrated to an IP deal with recognized to be related to this menace actor. Among the findings have been a welter of CryptoGuard alerts on the ransomware execution beginning a number of hours earlier than the occasion. Exfiltration started about an hour earlier than impression and lasted about an hour.
All PCs and servers are actually shut down throughout the group.
But Wait! There’s More!
This is the a part of the story nobody needs to listen to. Four days after locking up Blue’s property, the Cuba gang leaked the stolen information. This is the place we depart Blue – attorneys dealing with the authorized points of a giant information leak, IT restoring from backups from earlier made within the yr. The final time again to business-as-usual was simply over 9 weeks.
If there’s an ethical to this story, apart from There Are Some Horrible People In The World, it’s that nobody is alone, or needs to be alone, in terms of safety apply. Single-player whack-a-mole is a venerable however unwinnable recreation, particularly if you’re making an attempt to do a number of practitioner roles (searching, responding, analyzing, restoring) directly. Circles of belief – amongst trade colleagues, amongst skilled organizations, and throughout the group itself — stands out as the solely hope most enterprises have of leveling the taking part in area.
Conclusion
To flip attackers’ personal conduct towards them, we should enhance friction wherever potential. If your programs are effectively maintained, attackers must do extra to subvert them. That takes time, and will increase the detection window. Fancy methods resembling “bring your own vulnerable driver” (BYOVD) assaults are fourth or fifth in line on most attackers’ checklist of choices, after the whole lot else fails and they should go “nuclear.” Robust layered defenses – together with ubiquitous, sturdy protections and monitoring — equal friction, which will increase the talent degree the attacker must carry to the desk. Many merely gained’t have what it takes and can transfer on to simpler targets.
We should shield the whole lot. Not solely does safety provide an opportunity at prevention, however it additionally comes with much-needed telemetry. If an asset can’t be protected in situ, it have to be remoted and entry to it managed and monitored. Simply eschewing safety for worry that it might adversely have an effect on efficiency shouldn’t be the reply, and ignoring or papering over gaps in safety leaves assault surfaces open. You should shield ya neck.
The advantage of full telemetry implies that organizations can have their very own eye within the sky to allow them to all the time be watching. Complete telemetry eliminates deliberate blind spots, but in addition acts as a beacon when blind spots are created by attackers. A telemetry sign going darkish is an occasion that must be investigated. Monitoring extends past the community and working programs to understanding when a particular occasion is uncommon and sinister. For instance, registry adjustments – seen in 26% of investigations and #8 on the checklist of methods – are sometimes utilized by attackers to switch programs right into a extra compliant state, subvert their protections, or obfuscate their exercise. Such adjustments needs to be uncommon on servers and may all the time be evaluated as a possible menace indicator; your watching eyes ought to see that type of factor each single time it occurs. You are the maker of guidelines, take care of these fools.
An integral a part of monitoring, past proactively wanting on the telemetry, is that this type of understanding of what the knowledge means. Many organizations accumulate huge quantities of telemetry however wrestle to select related and necessary alerts. This is the place skilled menace hunters, and (later) incident responders, are available in. Threat hunters perceive the enterprise, they know what regular appears to be like like, they usually’re on high of all of the soiled tips attackers have at their fingertips. Together with incident responders they understand how and when to provoke a response. Be prepared to research — it may well imply the distinction between cleansing up a pesky coinminer or rebuilding the whole atmosphere from backup.
In the phrases of the good fight strategist (be that Moltke or Eisenhower or Tyson), everybody’s obtained a plan till the difficulty begins. That mentioned, have response plans for the sorts of assaults almost definitely to have an effect on your enterprise, and apply these plans prematurely with each your safety practitioners and the opposite firm stakeholders on whom you’d have to rely in a disaster. The course of will make it easier to to establish and deal with system weaknesses earlier than attackers do. Many Sophos IR investigations begin after organizations try their very own restoration and fail. This shouldn’t be an indictment on those that attempt, however a sign that many organizations want assist in the primary place. A vital and sincere evaluation of capabilities ought to tease this out. Open up the doorways and ask for assist.
Security practitioners on the whole and menace hunters particularly have discovered methods to construct and feed circles of belief to share findings and marshal defender forces. Prudent participation in these lets others be taught out of your errors (and successes), and also you from theirs. Organizations engaged on constructing these relationships ought to set up good in-house communications to find out what, how, and with whom they may share.
What have we discovered from analyzing all this information? In quick, whether or not quick or gradual, it doesn’t a lot matter: Other than velocity, there isn’t a tangible distinction between quick and gradual assaults. The quick assaults are a 78rpm playback of the slower ones; the music stays the identical.
That might sound like we’re advising defenders to only quit. We are usually not. Instead, defenders have to put aside the concept that elevated assault velocity makes protection’s job foundationally completely different. In reality, a number of the protections for which defenders have all the time been accountable simply may – if finished scrupulously – make attackers’ want for velocity a weapon for defenders. Where there may be urgency, there may be error; attackers’ velocity is prone to make them noisier, and if practitioners are listening on the hands-on degree these alerts gained’t go to waste.
Acknowledgements
Colin Cowie, Morgan Demboski, Karla Soler, Mauricio Valdivieso, and Hilary Wood contributed to the analysis offered on this report.
Appendix A: Demographics and methodology
For this report, 83% of the dataset was derived from organizations with fewer than 1000 workers. As in earlier years, higher than 50% of organizations requiring our help have 250 workers or fewer. For an in depth take a look at our demographics for years previous to 2023, please discuss with the Active Adversary Report for Business Leaders, printed earlier this yr.
To look at the dwell-time pattern over 18 months of knowledge we checked out instances from 2022 and the primary half of 2023. For the side-by-side comparability of two related instances (“Watching the Detectives”), we chosen an Incident Response case that fell exterior that 18-month dataset; the main points of that case are usually not represented elsewhere within the report statistics. Likewise, the MDR case shouldn’t be represented elsewhere within the report.
Protecting the confidential relationship between Sophos and our clients is in fact our first precedence, and the info you see right here has been vetted at a number of levels throughout this course of to make sure that no single buyer is identifiable by means of this information – and that no single buyer’s information skews the combination inappropriately. When doubtful a couple of particular case, we excluded that buyer’s information from the dataset.
Nations represented (2022-1H2023)
Figure A1: The thirty-four international locations we visited (nearly or in any other case) in 2022 and the primary half of 2023
| Australia | Japan | Singapore |
| Austria | Kenya | Somalia |
| Bahrain | Kuwait | South Africa |
| Belgium | Malaysia | Spain |
| Brazil | Mexico | Sweden |
| Canada | New Zealand | Switzerland |
| Colombia | Nigeria | Thailand |
| Finland | Philippines | United Arab Emirates |
| Germany | Poland | United Kingdom of Great Britain and Northern Ireland |
| Hong Kong | Qatar | |
| India | Romania | United States of America |
| Italy | Saudi Arabia |
Industries represented (2022-1H2023)
| Architecture | Government | News Media |
| Communication | Healthcare | Non-profit |
| Construction | Hospitality | Pharmaceutical |
| Education | Information Technology | Real property |
| Electronics | Legal | Retail |
| Energy | Logistics | Services |
| Entertainment | Manufacturing | Transportation |
| Financial | Mining | |
| Food | MSP/Hosting |
Methodology
The information on this report was captured over the course of particular person investigations undertaken by Sophos’ X-Ops Incident Response group. The Sophos MDR information described within the “Watching the Detectives” comparability was captured in the middle of regular MDR providers offered to that buyer.
When information was unclear or unavailable, the creator labored with particular person IR case leads and/or MDR analysts to clear up questions or confusion. Incidents that would not be clarified sufficiently for the aim of the report, or about which we concluded that inclusion risked publicity or different potential hurt to the Sophos-client relationship, have been put aside. We then examined every remaining case’s timeline to achieve additional readability on such issues as preliminary entry, dwell time, exfiltration, and so forth.