[ad_1]
Authored by Oliver Devane
Technical Support Scams have been focusing on pc customers for a few years. Their objective is to make victims consider they’ve points needing to be fastened, after which cost exorbitant charges, which sadly some victims pay. This weblog publish covers quite a few instance actions, that scammers will undergo when they’re performing their scams. Our objective is to coach shoppers on the indicators to look out for, and what to do in the event that they consider they’re being scammed.
Advertising – The Lure
For a tech help scammer to achieve their victims, they should first discover them (or be discovered by them). One method we see contains scammers creating Twitter or different social media accounts that publish messages claiming to be from the official technical help web site. For instance, a Twitter account will publish a tweet with the hashtags #McAfee and #McAfeeLogin to drive site visitors to the tweet and make victims consider the hyperlinks are reputable and secure to click on.
Scammers behind tech help scams can create very convincing web sites which mimic the official ones.
Some fraudulent web sites use the McAfee emblem or different firm logos to strive trick people. They usually invite clicking on a ‘LOGIN’ or ‘ACTIVATE’ hyperlink with the same colour scheme to official websites to look reputable.
These websites might then ask the sufferer to enter their actual username, password, and telephone quantity. Upon getting into these particulars, web sites will normally present an error message to make the sufferer consider there is a matter with their account.
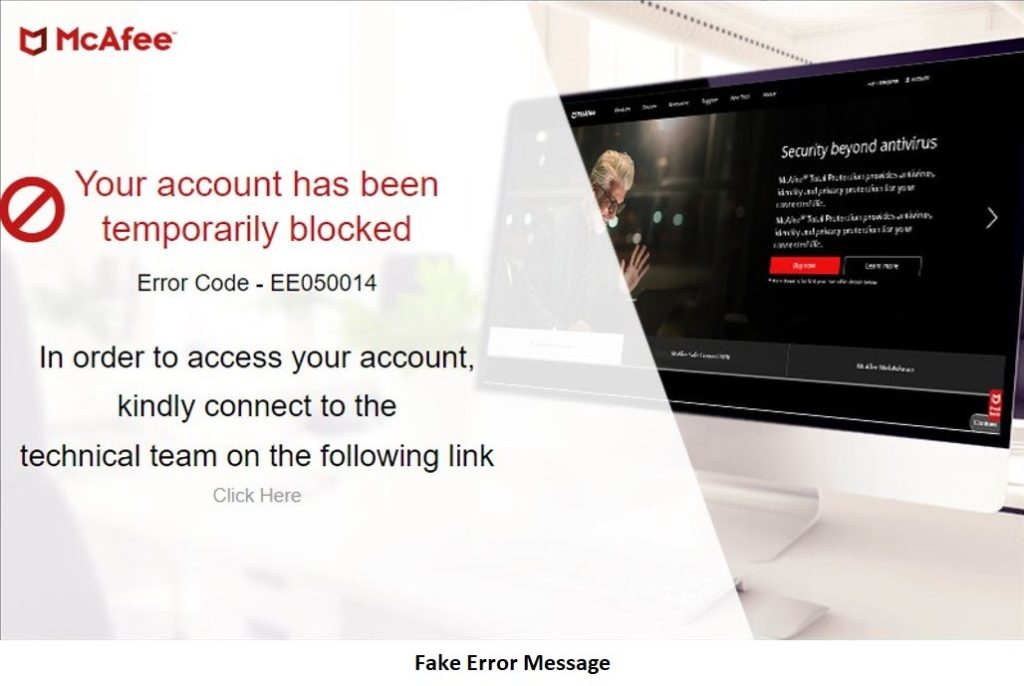
The error message will normally include a hyperlink that upon clicking will load a chat field the place the scammers will provoke a dialog with the sufferer. At this level, the scammers may have the telephone quantity and e mail handle related to the sufferer. They will use this to contact them and make them consider they’re an official technical help worker.
Gaining Access
The scammer’s subsequent goal is usually to achieve entry to the sufferer’s pc. They do that in order that they will trick the sufferer into believing there is a matter with their pc and that they want their help providers to repair it.
The scammers will do that by both asking the sufferer to enter a URL that may end result within the obtain of a distant entry device or by offering them with a hyperlink within the chat window if they’re nonetheless chatting with them on the faux help web site.
A distant entry device will allow the scammer to take full management of the sufferer’s machine. With this, they are going to be capable of take away or set up software program, entry private information equivalent to paperwork and cryptocurrency wallets in addition to dump passwords from the net browsers to allow them to then entry all of the sufferer’s accounts.
It is significant to not present distant entry to your pc to unknown and unverified people, as there might be an enormous danger to your private information. Some examples of distant entry instruments which have reputable makes use of however are sometimes used to perpetrate fraud are:
- TeamViewer
- LogMeIn
- AnyDesk
- Aweray (Awesun)
Activity as soon as the connection is established
If the scammers are given entry to the sufferer’s machine, they are going to usually make use of the command filename cmd.exe to carry out some visible exercise on the pc display which is finished to aim to trick the person into believing that some malicious exercise is happening on their pc or community. Most folks will likely be unaware of the filename cmd.exe and the actions getting used,and thus will likely be none the wiser to the scammer’s actions.
Here are some examples we’ve got seen scammers use:
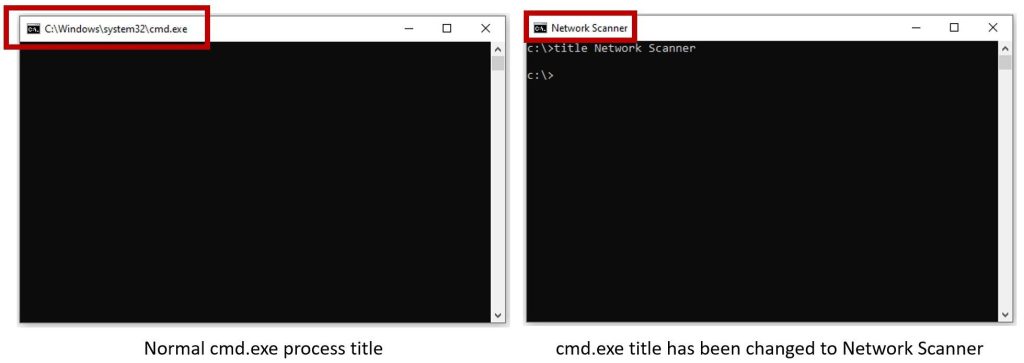
Title
Changing the title of cmd.exe to ‘network scanner’ or ‘file scanner’ to make the sufferer consider they’re operating a safety device on their machine.
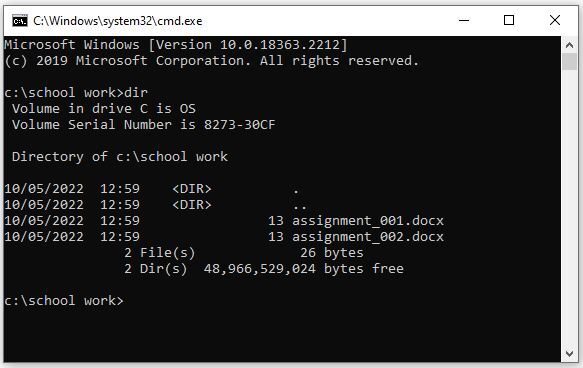
Directory enumeration
Scammers will make use of normal features throughout the cmd.exe file, to make their victims consider they’re performing numerous exercise. One of those features is ‘dir’ which can show all of the recordsdata for a selected listing. For instance, when you’ve got a folder referred to as ‘school work’ and have 2 phrase paperwork in there, a ‘dir’ question of that folder will appear as if this:
What the scammers will do is make use of ‘dir’ and the title operate to make you consider they’re scanning your machine. Here is an instance of operating ‘dir’ on the all of the recordsdata on a machine with the cmd.exe title set to ‘File Scanner’:
Tree
An identical operate to ‘dir’ referred to as ‘tree’ may additionally be used. The ‘tree’ operate will show listing paths and can generate numerous occasions on the display:
Tech Support Phone Number
Some scammers may even add their telephone quantity to the taskbar of the sufferer’s machine. They do that by creating a brand new folder with the telephone quantity because the identify and including it as a toolbar. This is proven within the picture beneath
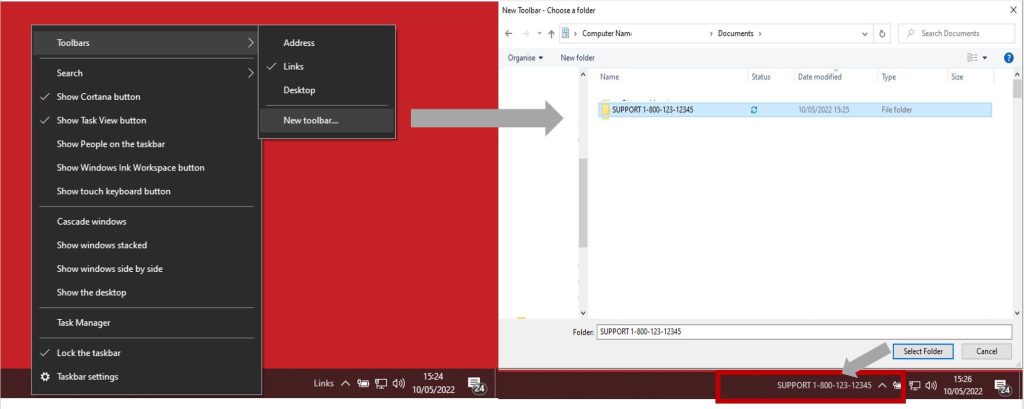
Software Installation
Scammers might set up different software program on the sufferer’s machine or make them consider that they’ve put in extra software program which they are going to then be charged for.
For instance, some scammers might add packages to the desktop of victims which don’t have any objective, however the scammers insist they’re reputable safety instruments equivalent to firewalls or community scanners.
Some instance filenames are:
- Firewall safety.exe
- Network firewall.exe
- Network safety.exe
- Email safety.exe
- Banking safety.exe
Payment
The scammers will normally carry out some exercise in your machine earlier than asking for cost. This is finished to construct confidence of their work and make you consider they’ve accomplished some exercise and subsequently deserve some form of cost. Do not be fooled by scammers who haven’t carried out any helpful exercise. As detailed within the earlier sections, watch out to not fall sufferer to faux social media accounts or web sites.
Signs to look out for
This part incorporates just a few indicators to look out for which can point out that you’re interacting with a scammer.
Rude/Short
Some scammers will turn into impolite and really brief with you in case you begin questioning what they’re doing. They might say that you’re not technical and don’t perceive what is happening. This wouldn’t be the habits of a reputable technical help operative.
Leave the pc on
Scammers will encourage you to depart the machine and distant connection on even when that you must exit and depart it unattended. Do not below any circumstances do that as they might then be free to do any exercise they want in your machine and community.
Created recordsdata being detected
Some recordsdata added to your machine by the scammer could also be detected by the AV safety software program. They might act like that is an error and the file is harmless. If you have got initiated a distant connection and the controller creates a file in your machine which is detected by the safety software program, we suggest ceasing the interplay as detailed beneath.
What to do
The following steps needs to be carried out in case you consider you’re being scammed as a part of a tech help rip-off.
Disconnect the machine from the web
If the machine is related through a community cable, the simplest approach is to unplug it. If the machine is related through Wi-Fi, there could also be a bodily change that can be utilized to disconnect it. If there isn’t a bodily change, flip off Wi-Fi by the settings or the pc. It will be powered down by urgent the ability button.
Hang up
Hang up the telephone (or finish the chat) and don’t reply any extra calls from that quantity. The scammer will attempt to make you consider that the decision is reputable and ask you to reconnect the remote-control software program.
Remove the remote-control software program
If the scammer was controlling your machine, the remote-control software program will should be eliminated. If the pc was powered down, it may be powered again up, but when a popup is proven asking for permission to permit distant entry, don’t grant it.
The distant software program can normally be eliminated through the use of the management panel and add/take away packages. To do that, press the Windows key after which carry out a seek for ‘remove’ and click on on ‘Add or remove programs’.
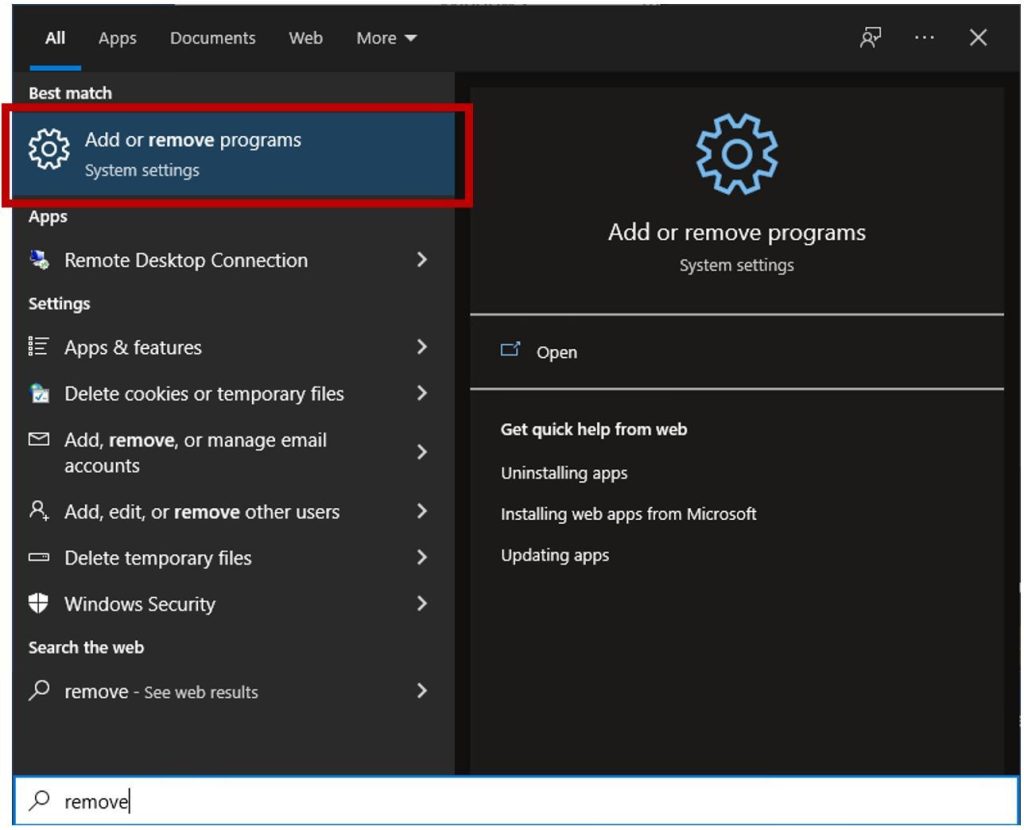
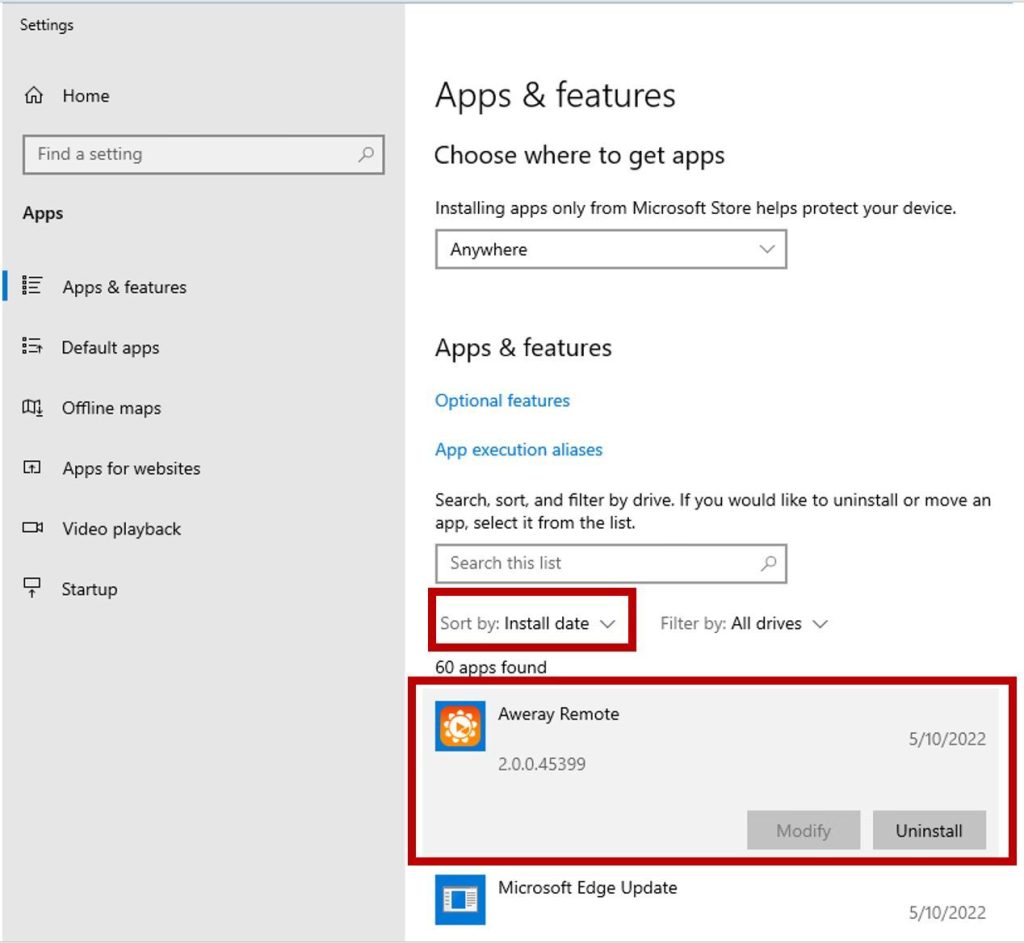
Sort the packages by set up date as proven beneath after which take away the distant software program by clicking on the ‘Uninstall’ button. Keep in thoughts that the software program put in in your pc might seem by a special identify, however in case you take a look at what was put in on the identical day because the scammer initiated the distant management session, you must be capable of establish it.
Check the Antivirus Software for any exclusions
Some scammers might add exclusions for the recordsdata they create in your pc in order that they aren’t detected by the safety software program. We suggest checking the exclusions and if any are current which weren’t added by your self to take away them.
A information for McAfee clients is obtainable right here
Update Antivirus Software and carry out a full scan
After eradicating any software program which was put in, we suggest updating your safety software program and performing a full scan. This will establish any malicious recordsdata created by the scammer equivalent to password stealers and keyloggers.
Change passwords
After performing a full scan, we suggest altering your entire passwords because the scammer might have gathered your credentials whereas they’d entry to your pc. It is beneficial to do that after performing a full scan because the scammers might have positioned a password stealer on the pc and any new passwords you enter may additionally be stolen.
Conclusion
This weblog publish incorporates quite a few examples that scammers might use to trick shoppers into believing that they might have points with their gadgets. If you’re experiencing points together with your pc and need to communicate to official McAfee help, please attain out through the official channel which is https://service.mcafee.com/.
The McAfee help pages can be accessed instantly through the McAfee Total Protection display as proven beneath:
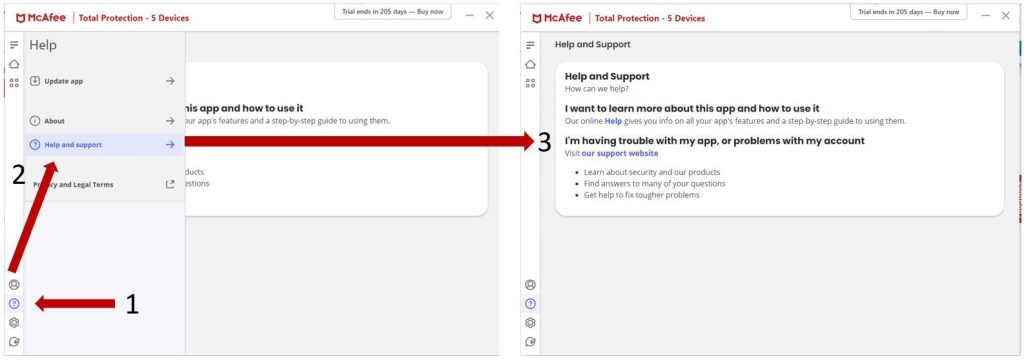
McAfee clients using internet safety (together with McAfee Web Advisor) are shielded from identified malicious websites.
[ad_2]
