[ad_1]
Microsoft’s Digital Crimes Unit (DCU), cybersecurity software program firm Fortra™ and Health Information Sharing and Analysis Center (Health-ISAC) are taking technical and authorized motion to disrupt cracked, legacy copies of Cobalt Strike and abused Microsoft software program, which have been utilized by cybercriminals to distribute malware, together with ransomware. This is a change in the best way DCU has labored previously – the scope is larger, and the operation is extra complicated. Instead of disrupting the command and management of a malware household, this time, we’re working with Fortra to take away unlawful, legacy copies of Cobalt Strike to allow them to not be utilized by cybercriminals.
We will must be persistent as we work to take down the cracked, legacy copies of Cobalt Strike hosted around the globe. This is a vital motion by Fortra to guard the official use of its safety instruments. Microsoft is equally dedicated to the official use of its services. We additionally consider that Fortra selecting to companion with us for this motion is recognition of DCU’s work preventing cybercrime during the last decade. Together, we’re dedicated to going after the cybercriminal’s unlawful distribution strategies.
Cobalt Strike is a official and well-liked post-exploitation device used for adversary simulation offered by Fortra. Sometimes, older variations of the software program have been abused and altered by criminals. These unlawful copies are known as “cracked” and have been used to launch damaging assaults, similar to these in opposition to the Government of Costa Rica and the Irish Health Service Executive. Microsoft software program growth kits and APIs are abused as a part of the coding of the malware in addition to the legal malware distribution infrastructure to focus on and mislead victims.
The ransomware households related to or deployed by cracked copies of Cobalt Strike have been linked to greater than 68 ransomware assaults impacting healthcare organizations in additional than 19 international locations around the globe. These assaults have price hospital techniques hundreds of thousands of {dollars} in restoration and restore prices, plus interruptions to vital affected person care providers together with delayed diagnostic, imaging and laboratory outcomes, canceled medical procedures and delays in supply of chemotherapy therapies, simply to call just a few.
Disruption parts and technique
On March 31, 2023, the U.S. District Court for the Eastern District of New York issued a court docket order permitting Microsoft, Fortra, and Health-ISAC to disrupt the malicious infrastructure utilized by criminals to facilitate their assaults. Doing so allows us to inform related web service suppliers (ISPs) and laptop emergency readiness groups (CERTs) who help in taking the infrastructure offline, successfully severing the connection between legal operators and contaminated sufferer computer systems.
Fortra and Microsoft’s investigation efforts included detection, evaluation, telemetry, and reverse engineering, with further knowledge and insights to strengthen our authorized case from a worldwide community of companions, together with Health-ISAC, the Fortra Cyber Intelligence Team, and Microsoft Threat Intelligence workforce knowledge and insights. Our motion focuses solely on disrupting cracked, legacy copies of Cobalt Strike and compromised Microsoft software program.
Microsoft can also be increasing a authorized technique used efficiently to disrupt malware and nation state operations to focus on the abuse of safety instruments utilized by a broad spectrum of cybercriminals. Disrupting cracked legacy copies of Cobalt Strike will considerably hinder the monetization of those unlawful copies and gradual their use in cyberattacks, forcing criminals to re-evaluate and alter their techniques. Today’s motion additionally consists of copyright claims in opposition to the malicious use of Microsoft and Fortra’s software program code that are altered and abused for hurt.
Abuse by cybercriminals
Fortra has taken appreciable steps to forestall the misuse of its software program, together with stringent buyer vetting practices. However, criminals are identified to steal older variations of safety software program, together with Cobalt Strike, creating cracked copies to realize backdoor entry to machines and deploy malware. We have noticed ransomware operators utilizing cracked copies of Cobalt Strike and abused Microsoft software program to deploy Conti, LockBit, and different ransomware as a part of the ransomware as a service enterprise mannequin.
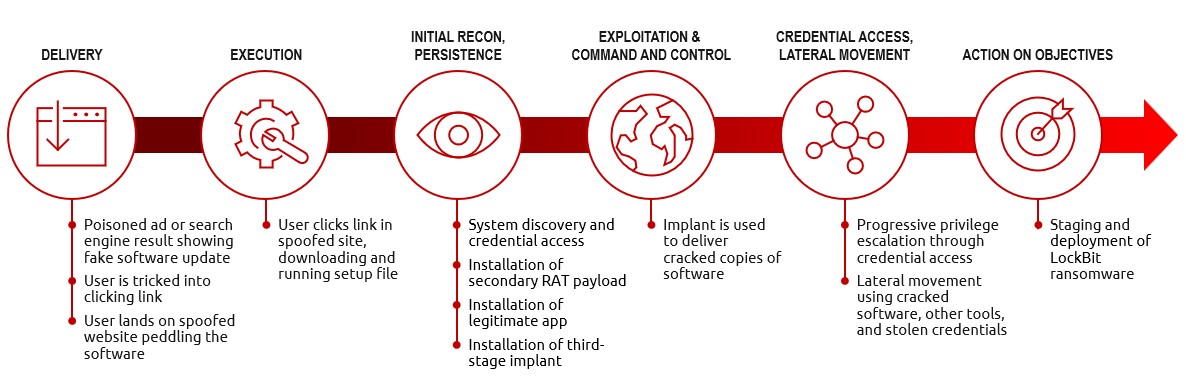
Threat actors use cracked copies of software program to hurry up their ransomware deployment on compromised networks. The under diagram reveals an assault movement, highlighting contributing elements, together with spear phishing and malicious spam emails to realize preliminary entry, in addition to the abuse of code stolen from firms like Microsoft and Fortra.
While the precise identities of these conducting the legal operations are at present unknown, now we have detected malicious infrastructure throughout the globe, together with in China, the United States and Russia. In addition to financially motivated cybercriminals, now we have noticed risk actors appearing within the pursuits of international governments, together with from Russia, China, Vietnam and Iran, utilizing cracked copies.
Continuing the struggle in opposition to risk actors
Microsoft, Fortra and Health-ISAC stay relentless in our efforts to enhance the safety of the ecosystem, and we’re collaborating with the FBI Cyber Division, National Cyber Investigative Joint Task Force (NCIJTF) and Europol’s European Cybercrime Centre (EC3) on this case. While this motion will impression the criminals’ quick operations, we absolutely anticipate they may try and revive their efforts. Our motion is subsequently not one and achieved. Through ongoing authorized and technical motion, Microsoft, Fortra and Health-ISAC, together with our companions, will proceed to observe and take motion to disrupt additional legal operations, together with using cracked copies of Cobalt Strike.
Fortra devotes important computing and human assets to fight the unlawful use of its software program and cracked copies of Cobalt Strike, serving to prospects decide if their software program licenses have been compromised. Legitimate safety practitioners who buy Cobalt Strike licenses are vetted by Fortra and are required to adjust to utilization restrictions and export controls. Fortra actively works with social media and file sharing websites to take away cracked copies of Cobalt Strike after they seem on these internet properties. As criminals have tailored their methods, Fortra has tailored the safety controls within the Cobalt Strike software program to remove the strategies used to crack older variations of Cobalt Strike.
As now we have since 2008, Microsoft’s DCU will proceed its efforts to cease the unfold of malware by submitting civil litigation to guard prospects within the massive variety of international locations around the globe the place these legal guidelines are in place. We will even proceed to work with ISPs and CERTs to determine and remediate victims.
