[ad_1]
Evilginx, a software primarily based on the professional (and broadly used) open-source nginx net server, can be utilized to steal usernames, passwords, and session tokens, permitting an attacker to probably bypass multifactor authentication (MFA). In this publish, we’ll show how evilginx works and what info it is ready to purchase; we even have recommendation for detecting this software in use, in addition to potential mitigations in opposition to its use.
How it really works
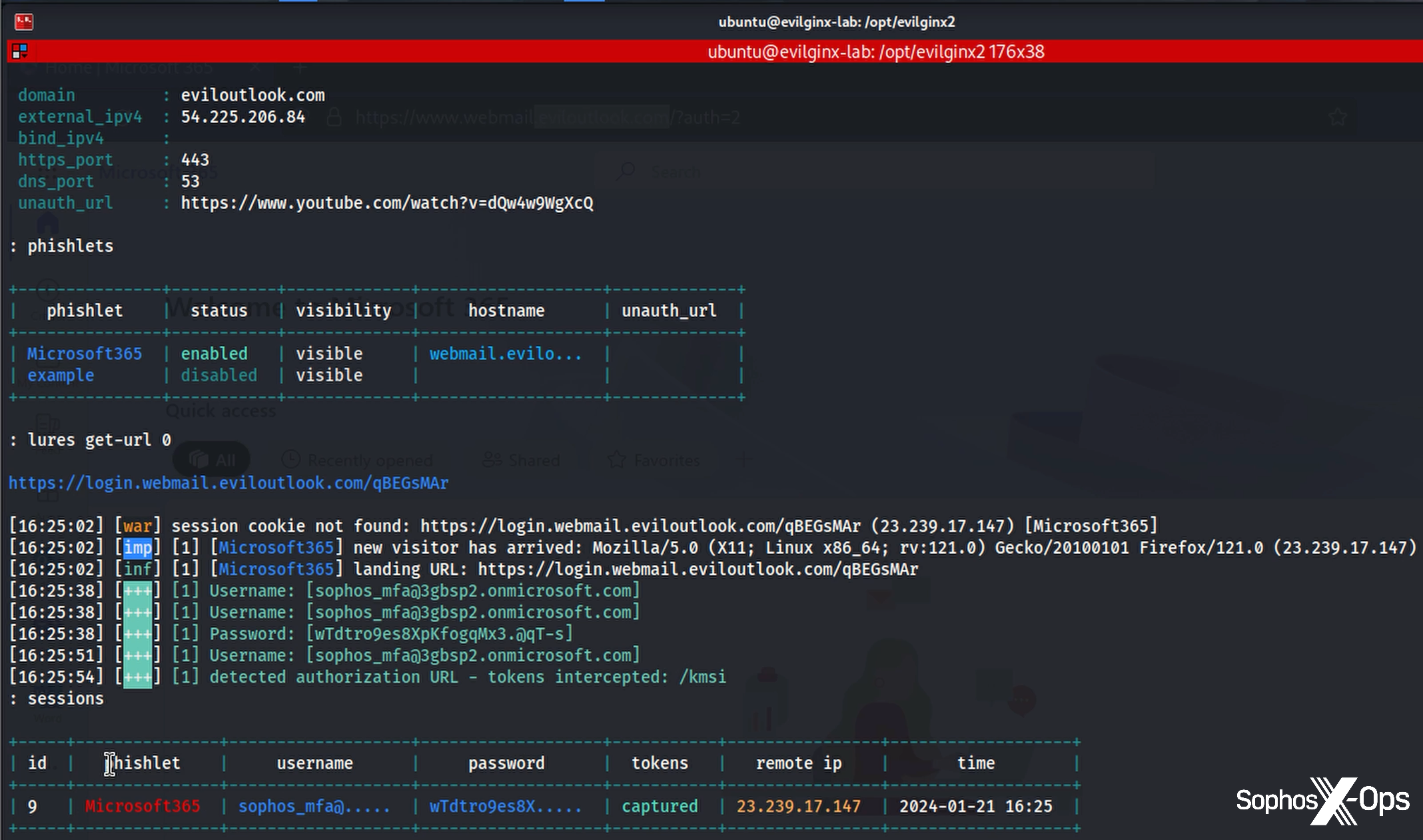
Evilginx at its core makes use of the professional and widespread net server nginx to proxy net site visitors by malicious websites, created by the risk actor to imitate actual companies resembling Microsoft 365 — an Adversary-in-the-Middle (AitM) assault. To show, we configured a malicious area; as proven in Figure 1, now we have a Microsoft phishlet in place with its personal subdomain of that area. (All related IP addresses, usernames, passwords, and domains used on this publish have been decommissioned previous to publication.) The phishlet features a lure, and that lure is what the focused person sees because the attacker makes an attempt to seize their username and password.
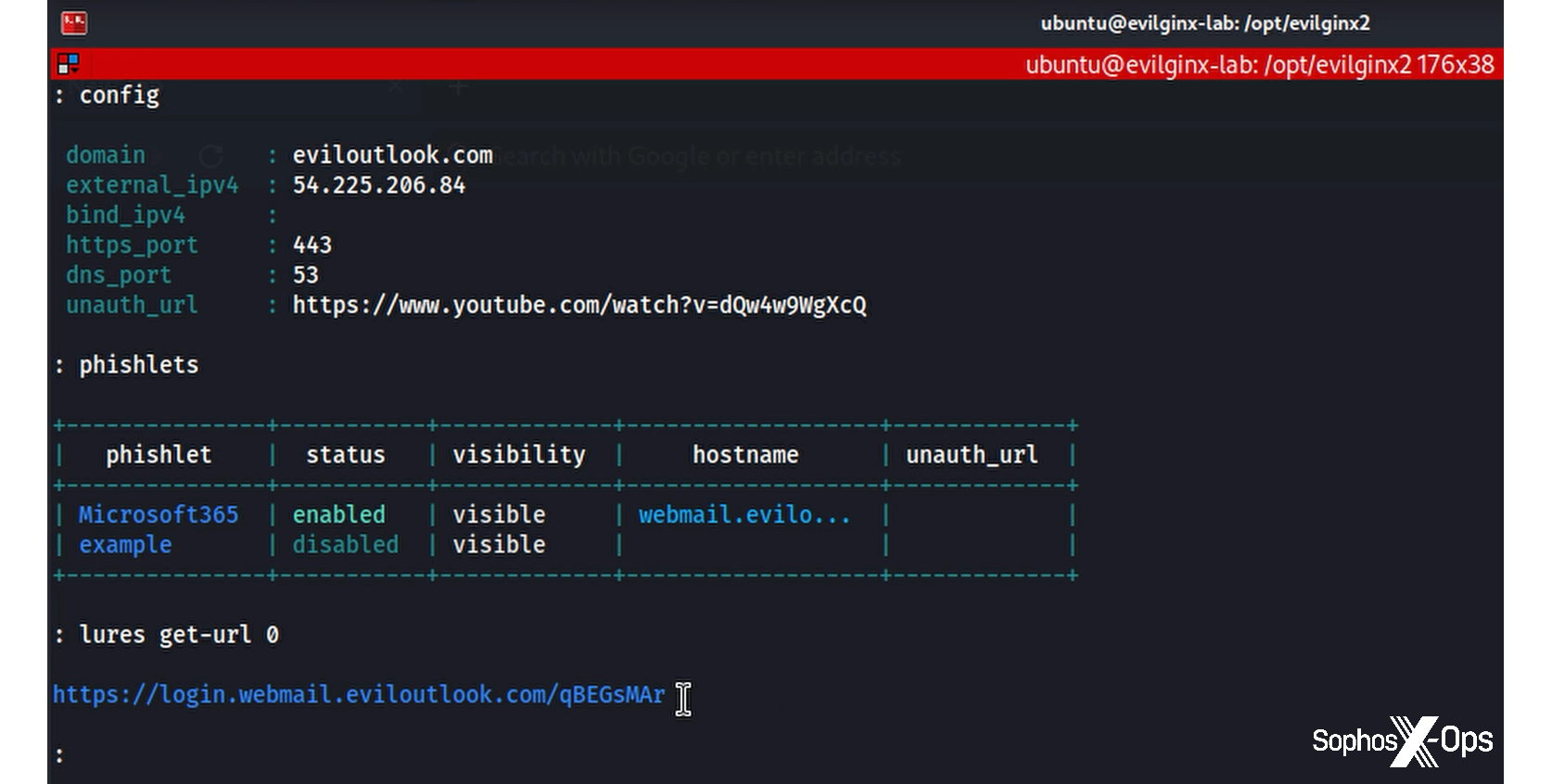
Figure 1: Evilginx in motion, displaying the malicious area, the phishlet, and the lure for use in opposition to the goal
It’s helpful to notice that the kinds and pictures the person sees actually do come from Microsoft itself; they’re relayed from the professional firm by the evilginx server and onward to the person. On the again finish, evilginx provides the attacker choices for configuring the expertise. In our testing, we mimicked a person account protected by MFA… and promptly received round it. The person is introduced with a “normal” login expertise; it’s solely after they click on on one of many apps alongside the left-hand aspect of the display screen {that a} canny person would possibly discover one thing is odd, as they are going to be requested to login once more.
A have a look at our evilginx server exhibits what’s taking place.
Figure 2: An evilginx server shows captured info and provides it to its database for later abuse
In addition to intercepting the person’s username and password, the session token was additionally gathered because it was handed from the Keep Me Signed In performance chosen by the attacker when the Microsoft immediate appeared. Evilginx stashes this information in a database that collects the knowledge on every session, additionally together with the general public IP tackle used to entry the server, the person agent in play – and, crucially, the cookie. With this in hand, the attacker want solely open a window to the professional login web page and import the cookie to be signed in because the professional person.
From right here, the risk actor has full entry to the person’s mailbox account. Typical actions can embrace including mailbox guidelines. If entry is out there, the risk actor may reset MFA units, change passwords, and carry out various different actions to present themselves extra persistence to the account.
Detection avenues
There are numerous methods defenders would possibly uncover exercise of this kind. First, in Azure and Microsoft 365, there are two foremost places that maintain monitor of logs and occasions that may be reviewed for uncommon exercise. The first are the Entra ID (beforehand referred to as Azure AD) register and Audit logs. The two examples in Figure 3 present our customers’ authentications originating from our evilginx server (54.225.206.84), after which from the Tor exit node that we used for our demonstration (45.80.158.27). The audit logs present that after this login, our attacker added a brand new authenticator app to “their” account.
Figure 3: There is unquestionably nothing suspicious about an inbox rule named Completely Legitimate Forwarder
Second, the Microsoft 365 logs, additionally referred to as the unified audit log or UAL, present that in the course of the session our illegitimate person added a brand new inbox rule referred to as Completely Legit Forwarder. (To help with reviewing these logs, Microsoft 365 additionally provides a sophisticated looking space within the safety middle that permits you to use the Kusto question language to filter and discover suspicious exercise utilizing totally different standards.)
Security alerts and incidents are additionally generated when suspicious exercise is detected. As an instance, we are able to see in Figure 4 that the sophos_mfa account tried to register from a suspicious IP tackle, and that an anomalous token was used throughout a type of periods.
Figure 4: The anomalous token, the nameless IP tackle, and the suspicious redirect rule are all flagged
For Sophos prospects, integrations exist for importing occasions and alerts from Azure and Microsoft 365 into Sophos Central. Depending on the precise XDR integration pack, customized identity-related detections are a part of the package deal; for MDR prospects, these detections are triaged by the MDR staff as a part of the service.
Potential mitigations and issues
Potential mitigations will be sorted into two classes, preemptive and reactive. A full listing of potential mitigations is nicely past the scope of this text, however as ever, a thought-out and layered strategy is finest with regards to defending any type of functions or companies which can be publicly obtainable and of excessive worth in your setting.
Still, it’s time we as an trade look to stronger measures, migrating off token-based or push MFA and towards strong, phishing-resistant, FIDO2-based authentication strategies.
The excellent news is that good choices can be found in lots of kinds – Yubikey-type {hardware} keys, Apple Touch ID on trendy {hardware}, Windows Hello for enterprise, even choices that incorporate iPhone and Android. (For additional ideas on higher instructions in MFA, please see Chester Wisniewski’s current essay on passkeys.)
Conditional entry insurance policies are one other potential step for securing your Azure and Microsoft 365 environments. In concept after all one may take the old style, hand-crafted whitelist route – blocking any IP tackle that’s not trusted – however virtually talking it’s the units one would handle, permitting solely enterprise-trusted units to log into enterprise methods. (Sophos and different distributors after all do maintain fixed look ahead to, and block, known-malicious websites as a part of our companies — a endless activity, and blocklisting is arguably simpler to handle than whitelisting.)
That mentioned, we can not in the end depend on person consciousness. Humans are fallible, and actually everybody will eventually be phished. The path ahead lies with architectures which can be resilient when people fail.
For reactive mitigations, step one needs to be to shut the door on the risk actor. In this case, there are a selection of steps that needs to be taken to verify the door is absolutely closed. To begin, revoke all periods and tokens by way of Entra ID and Microsoft 365, to take away entry that has been gained. These actions will be carried out within the person’s account in each Entra ID and Microsoft 365 utilizing the “Revoke sessions” and “Sign out of all sessions” buttons.
Next, reset the person’s passwords and MFA units. As we noticed within the logs, our risk actor added a brand new MFA gadget to the person’s account. Depending on the kind of MFA gadget added, this will enable passwordless entry to the account, eradicating the efficacy of fixing passwords and eradicating periods. Use Microsoft 365’s logs to look at all exercise undertaken by the attacker. Spotting stealth modifications, such because the addition of latest inbox guidelines, is necessary to verify no extra info is ready to depart the person’s account. Administrators could discover it helpful to refer additionally to Microsoft’s personal investigation steerage regarding token theft.
Conclusion
Evilginx is a formidable methodology of MFA-bypassing credential compromise — and it makes a fancy assault approach workable, which in flip can result in widespread use of the approach. The excellent news is that the mitigations and practices it’s best to already be following are highly effective deterrents to the success of attackers making an attempt to deploy this software in opposition to your infrastructure.
[ad_2]