[ad_1]

A suspected Chinese hacking marketing campaign has been focusing on unpatched SonicWall Secure Mobile Access (SMA) home equipment to put in customized malware that establishes long-term persistence for cyber espionage campaigns.
The deployed malware is personalized for SonicWall gadgets and is used to steal person credentials, present shell entry to the attackers, and even persist by firmware upgrades.
The marketing campaign was found by Mandiant and SonicWall’s PSIRT crew, who observe the actor behind it as UNC4540, prone to be of Chinese origin.
New malware targets SonicWall gadgets
The malware used on SonicWall gadgets consists of an ELF binary, the TinyShell backdoor, and several other bash scripts that present a deep understanding of the focused community gadgets.
“The total habits of the suite of malicious bash scripts exhibits an in depth understanding of the equipment and is effectively tailor-made to the system to supply stability and persistence,” explains Mandiant.
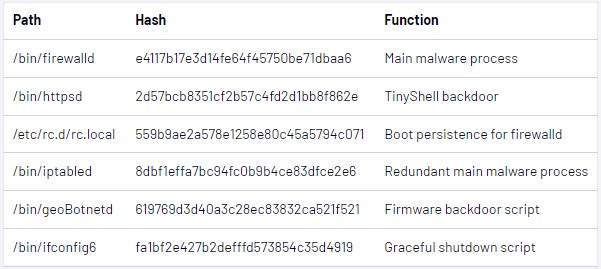
The primary module, named ‘firewalld,’ executes SQL instructions towards the equipment’s database to steal the hashed credentials of all logged-in customers.
The stolen credentials are copied on a textual content file created by the attacker at ‘tmp/syslog.db’ and are later retrieved to be cracked offline.
Additionally, firewalld launches different malware parts, like TinyShell, to ascertain a reverse shell on the equipment for straightforward distant entry.
Finally, the principle malware module additionally provides a small patch to the professional SonicWall binary ‘firebased,’ however Mandiant’s researchers could not decide its actual objective.
The analysts hypothesize that this modification helps the malware’s stability when the shutdown command is entered on the gadget.
While it’s unclear what vulnerability was used to compromise gadgets, Mandiant says that the focused gadgets had been unpatched, making them doubtless susceptible to older flaws.
Recent flaws disclosed by SonicWall [1, 2, 3] that impacted SMA gadgets allowed unauthenticated entry to gadgets, which might then be utilized in campaigns like this one.
Persistence and resilience
Mandiant says there are indicators that the malware was put in on the examined methods all the best way again in 2021 and endured by a number of subsequent firmware updates on the equipment.
The menace actors achieved this through the use of scripts that supply redundancy and guarantee long-term entry to breached gadgets.
For instance, there is a script named “iptabled” that’s primarily the identical module as firewalld however will likely be solely referred to as by the startup script (“rc.native”) if the first malware course of exits, crashes, or cannot be launched.
Additionally, the attackers applied a course of the place a bash script (“geoBotnetd”) checks for brand spanking new firmware updates at “/cf/FIRMWARE/NEW/INITRD.GZ” each 10 seconds. If one is discovered, the malware injects itself into the improve bundle to outlive even after firmware upgrades.
The script additionally provides a backdoor person named “acme” on the improve file to allow them to keep entry after the firmware replace is utilized to the breached equipment.
System directors are suggested to use the most recent safety updates supplied by SonicWall for SMA100 home equipment.
The beneficial goal model proper now’s 10.2.1.7 or greater, which incorporates File Integrity Monitoring (FIM) and anomalous course of identification, which ought to detect and cease this menace.
This marketing campaign shares many similarities with current assaults that focused a zero-day vulnerability in Fortinet SSL-VPN gadgets utilized by authorities organizations and government-related targets.
Similar to the SonicWall marketing campaign, the menace actors behind the Fortinet assaults confirmed intimate data concerning the gadgets and the way they operated to inject customized malware for persistence and knowledge theft.
“In current years Chinese attackers have deployed a number of zero-day exploits and malware for a wide range of web going through community home equipment as a path to full enterprise intrusion, and the occasion reported right here is a part of a current sample that Mandiant expects to proceed within the close to time period,” warns Mandiant within the report.
