[ad_1]
Vulnerability evaluation leads to Orange Cyberdefenses’ Security Navigator present that some vulnerabilities first found in 1999 are nonetheless present in networks at present. This is regarding.
Age of VOC findings
Our Vulnerability Scans are carried out on a recurring foundation, which supplies us the chance to look at the distinction between when a scan was carried out on an Asset, and when a given discovering on that Asset was reported. We can name that the discovering ‘Age’. If the findings first reported usually are not addressed, they may happen in additional scans over time with rising Age, and so we will observe how the Age of reported findings modifications over time.
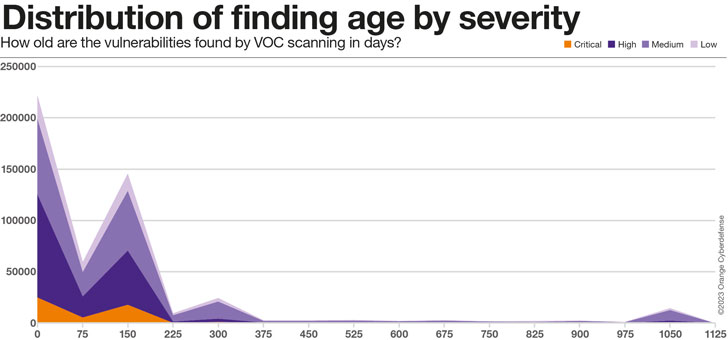
As the chart under clearly illustrates, the vast majority of actual findings in our dataset, throughout all Severity ranges, are between 75 and 225 days outdated. There is a second ‘peak’ at round 300 days, which we suspect has extra to do with the age of the info within the dataset and may subsequently be ignored. Finally, there’s a fascinating ‘bump’ at round 1,000 days, which we consider represents the ‘lengthy tail’ of findings within the dataset that can merely by no means be addressed.
75% of the findings within the 1000-days ‘bump’ are Medium Severity, however 16% are categorised as High or Critical Severity.
The Average Age of findings in our dataset is impacted as a lot by modifications in our Customer and Assets set as any exterior issue, as could be seen within the excessive diploma of variation. Yet, there’s a clear enhance within the Average Age of findings of 241% from 63 to 215 days over the 24 months since we have been onboarding purchasers onto this platform.
Roughly grouping confirmed findings from our Vulnerability Scan knowledge by ‘Age Group’ reveals the next:
- Only 20% of all findings are addressed in underneath 30 days
- 80% all findings take 30 days or extra to patch
- 57% of all findings take 90 days or extra to patch.
- 215 days Average
Average/max age of findings by severity
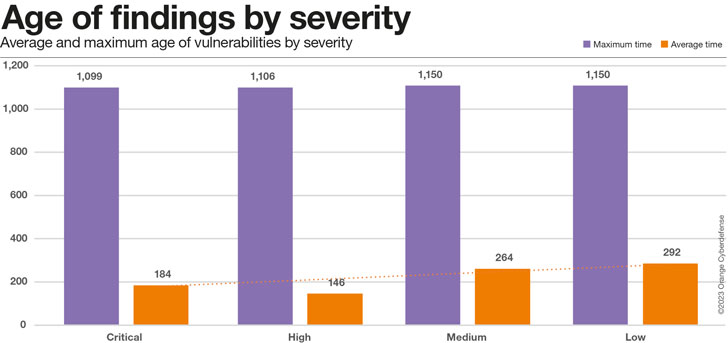
The chart under means that even Critical Vulnerabilities are taking round 6 months on common to resolve, however that’s encouragingly a minimum of 36% sooner than the time for low-severity points.
Taking a better take a look at the readings of common vs. most time for various scores of criticality we find yourself with the chart under.
While our conclusion of important points being resolved sooner stands for the typical mitigation time, the utmost time is persistently excessive no matter criticality.
We must watch this metric extra because the dataset grows sooner or later.
Industry Comparison
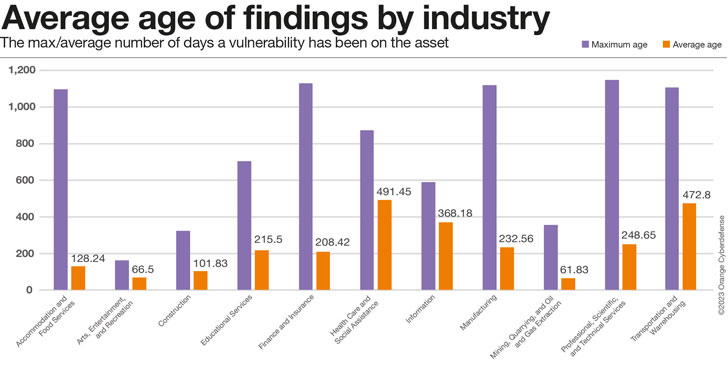
The most age of findings within the view under serves as a lot as a sign of how lengthy prospects from that Industry have been current in our dataset as anything, whereas the typical age is a greater proxy for the way effectively prospects are doing at addressing the problems we report. Industries with excessive maximums and low averages would subsequently be doing the very best, excessive most and excessive common… the ‘worst.’ Industries with very low most ages have most likely not been within the dataset for very lengthy and will, subsequently, maybe not be included in comparisons on this metric.
However these Industries are in contrast, the discovering Age is a regarding metric.
How outdated are these vulnerabilities actually?
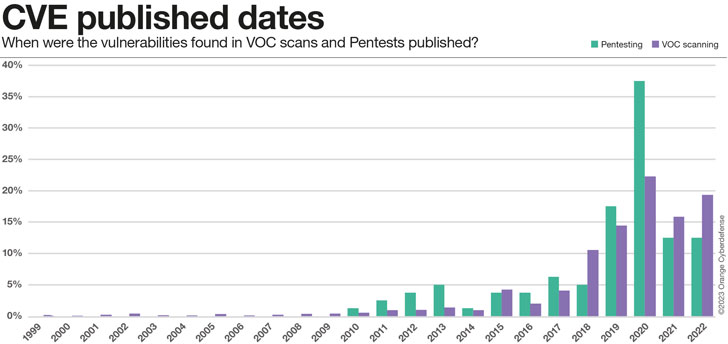
So far we’ve got solely regarded on the relative time, from after we first discovered a vulnerability in an asset up till now (if nonetheless current). However, that doesn’t give us any info on how outdated these vulnerabilities actually are. Taking a better take a look at the discovered CVEs we will analyze their publishing dates. The outcomes are considerably baffling, however appear to suit the image that emerges: for one purpose or one other, some vulnerabilities are simply not fastened, ever. They develop into a part of the safety debt that companies accumulate.
- 0.5% of CVEs reported are 20 years outdated or extra
- 13% of CVEs stories are 10 years outdated or extra
- 47% of CVEs are 5 years outdated or extra
Conclusion
More than 22 vulnerabilities with assigned CVEs are printed every day. With a mean CVSS rating above 7 (High Severity), every of those disclosed vulnerabilities is a big datapoint that impacts our danger equations and our actual publicity to threats.
Vulnerability Scanning and Penetration Testing are mechanisms we use to make sense of the vulnerabilities that will impression our safety posture, perceive their potential impression, prioritize and take applicable motion. These two evaluation workout routines are totally different in method, however use comparable language and serve an analogous goal.
This yr we’re together with an evaluation of datasets from each companies within the Navigator. This is the primary time we try this, and our knowledge remains to be removed from excellent.
What we will clearly see is the we’re struggling to handle the vulnerabilities we find out about. On common, it’s taking our prospects 215 days to patch a vulnerability we report back to them. This is slightly decrease for Critical Vulnerabilities – it seems these are patched 36% sooner than ‘Low’ severity points. But the image remains to be grim: 80% of all Findings take 30 days or extra to patch, 57% take 90 days or extra.
Our pentesting groups are nonetheless discovering vulnerabilities that have been first recognized in 2010, and our scanning groups encounter points that date again to 1999! Indeed 47% of CVEs are 5 years outdated or extra. 13% are as outdated as 10 years or extra. This is a regarding outcome.
This is simply an excerpt of the evaluation. More particulars, just like the criticality of vulnerabilities and the modifications in Pentesting and VOC scanning outcomes over time (in addition to a ton of different fascinating analysis subjects), could be discovered within the Security Navigator. It’s freed from cost, so take a look. It’s price it!
Note: This informative piece has been expertly crafted and generously shared by Charl van der Walt, Head of Security Research at Orange Cyberdefense.