[ad_1]
The software program business is making headway towards a bunch of pernicious vulnerabilities which might be liable for the overwhelming majority of crucial, remotely exploitable, and in-the-wild assaults, software-security consultants stated this week.
The class of vulnerabilities — so-called memory-safety points — embody buffer overflows and use-after-free errors and have accounted for almost all of utility safety points disclosed by software program firms. Now, the most recent information present that the growing use of memory-safe languages — comparable to Java, C#, and extra lately, Rust — has resulted in a fast decline of all the class of vulnerabilities.
Last week, for instance, Google revealed that the most recent model of the Android working system has extra new code written in memory-safe programing languages — comparable to Java, Rust, and Kotlin — than memory-unsafe languages comparable to C and C++, leading to a drop in memory-safety vulnerabilities from 223 to 85 over the previous three years.
“We are persevering with to give attention to eliminating whole lessons of vulnerabilities, specializing in essentially the most extreme first,” says Jeffrey Vander Stoep, a software program engineer at Google. “As reminiscence security vulnerabilities turn into extra scarce, we anticipate the analysis neighborhood to focus their vulnerability-findings efforts on different lessons of vulnerabilities.”
For a long time, C and C++ have been the workhorse programming languages of the software program business. Yet they lack the reminiscence protections of extra fashionable languages, comparable to C#, Go, Java, Python, Ruby, Rust, and Swift. The outcome? Fifty-nine % of functions written in C++ have high-severity or critical-severity flaws, in comparison with 9% for JavaScript and 10% for Python, in line with application-security agency Veracode’s State of Software Security Vol. 11 report.
Buffer Overflows and Wormable Flaws
The ease with which programmers can create flawed code has turn into a serious drawback for big software program firms. Microsoft, for instance, discovered that, up till 2018, memory-safety points accounted for 70% of the vulnerabilities found within the firm’s software program. Overall, reminiscence issues of safety have accounted for 60% to 70% of all vulnerabilities throughout all kinds of ecosystems, in line with 2020 analysis by software program resilience engineer Alex Gaynor.
And as a result of the issues can simply be exploited to assault functions, they’re the foundation causes behind a big variety of compromises, says Chris Wysopal, chief expertise officer of Veracode.
“Memory corruption points are amongst the best severity flaws as they typically enable attackers to use with code execution which permits them to take full management of the appliance,” he says. “In the worst case state of affairs this enables the creation of a worm exploit which may go on to assault different cases of the vulnerability.”
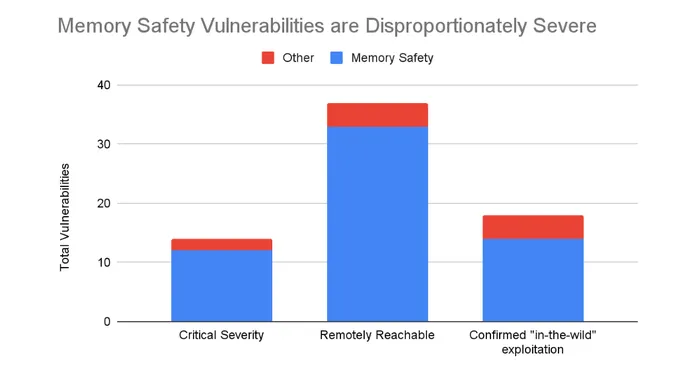
In its current weblog publish on its shift to memory-safe languages for Android improvement, Google famous that whereas memory-safety vulnerabilities now solely account for 36% of points disclosed in Android, they account for 86% of the crucial safety vulnerabilities and 89% of remotely exploitable points.
Making the Switch to Safe Languages
For that motive, Google and others have urged builders to undertake memory-safe languages.
In Google’s case, C and C++ now account for simply lower than half of all new code. In truth, Android 13, the most recent model, is the primary the place the vast majority of code has been written in memory-safe languages, with Rust changing C and C++ for a lot of builders. Rust is an environment friendly programming language centered on creating safe code.
Even the National Security Agency is urging firms to undertake memory-safe programming languages.
Switching to a memory-safe language just isn’t ample, nevertheless. While the languages do make it more durable for programmers to write down insecure code, each language has a distinct degree of safety. For that motive, the NSA has additionally beneficial that builders use a wide range of application-security instruments — from compiler choices to static scanners to runtime evaluation — to harden functions as a lot as potential.
“Software evaluation instruments can detect many cases of reminiscence administration points and working atmosphere choices can even present some safety, however inherent protections supplied by reminiscence secure software program languages can forestall or mitigate most reminiscence administration points,” the NSA’s report acknowledged.
In the tip, whereas memory-safe programming languages should not a standalone resolution to the issue of software program vulnerabilities, they offer steerage to builders who can then keep away from a number of the most extreme programming errors, says Veracode’s Wysopal.
“It’s exhausting to generalize and say that there’s a decrease quantity of vulnerabilities in reminiscence secure languages because the manner they’re used is completely different,” he says. “But for those who had been utilizing two completely different languages to perform the very same activity, and one was reminiscence secure, you’d count on fewer vulnerabilities in that one and usually much less crucial vulnerabilities.”
[ad_2]
