[ad_1]
A important safety flaw has been disclosed in Amazon Elastic Container Registry (ECR) Public Gallery that would have been doubtlessly exploited to stage a large number of assaults, in response to cloud safety agency Lightspin.
“By exploiting this vulnerability, a malicious actor may delete all photos within the Amazon ECR Public Gallery or replace the picture contents to inject malicious code,” Gafnit Amiga, director of safety analysis at Lightspin, mentioned in a report shared with The Hacker News.
“This malicious code is executed on any machine that pulls and runs the picture, whether or not on person’s native machines, Kubernetes clusters or cloud environments.”
ECR is a container picture registry service managed by Amazon Web Services, enabling customers to bundle code as Docker photos and deploy the artifacts in a scalable method. Public repositories hosted on ECR are displayed in what’s referred to as the ECR Public Gallery.
“By default, your account has learn and write entry to the repositories in your public registry,” Amazon notes in its documentation. “However, IAM customers require permissions to make calls to the Amazon ECR APIs and to push photos to your repositories.”
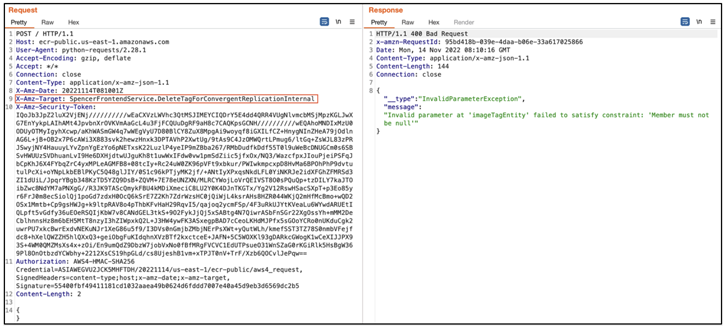
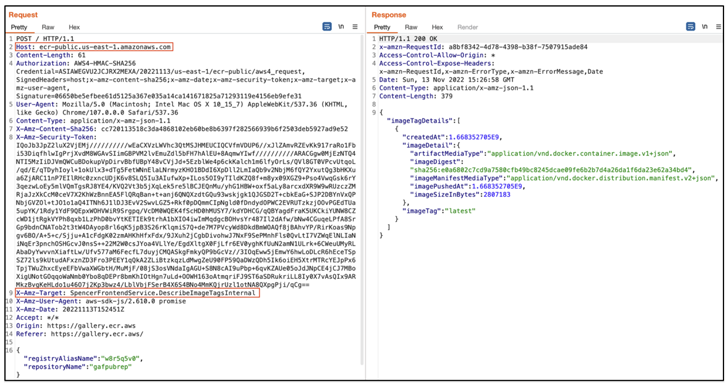
But the difficulty recognized by Lightspin meant that it may very well be weaponized by exterior actors to delete, replace, and create poisoned variations of reliable photos in registries and repositories that belong to different AWS accounts by profiting from undocumented inner ECR Public APIs.
This is achieved by buying momentary credentials utilizing Amazon Cognito to authorize requests to the interior APIs and activate the motion to delete photos utilizing “DeleteImageForConvergentReplicationInternal,” or alternatively push a brand new picture through the “PutImageForConvergentReplicationInternal” motion.
Lightspin characterised the flaw for instance of “deep software program provide chain assault.”
Amazon has since deployed a repair to resolve the weak point as of November 16, 2022, lower than 24 hours after it was reported, indicative of the severity of the issue. No buyer motion is required.
“This vulnerability may doubtlessly result in denial-of-service, information exfiltration, lateral motion, privilege escalation, information destruction, and different multivariate assault paths which can be solely restricted by the craftiness and objectives of the adversary,” Amiga famous.
“A malicious actor may poison fashionable photos, all whereas abusing the belief mannequin of ECR Public as these photos would masquerade as being verified and thus undermine the ECR Public provide chain.”
[ad_2]