[ad_1]
The Russian cyberespionage group often known as Turla has been noticed piggybacking on assault infrastructure utilized by a decade-old malware to ship its personal reconnaissance and backdoor instruments to targets in Ukraine.
Google-owned Mandiant, which is monitoring the operation underneath the uncategorized cluster moniker UNC4210, stated the hijacked servers correspond to a variant of a commodity malware referred to as ANDROMEDA (aka Gamarue) that was uploaded to VirusTotal in 2013.
“UNC4210 re-registered at the very least three expired ANDROMEDA command-and-control (C2) domains and commenced profiling victims to selectively deploy KOPILUWAK and QUIETCANARY in September 2022,” Mandiant researchers stated in an evaluation printed final week.
Turla, additionally recognized by the names Iron Hunter, Krypton, Uroburos, Venomous Bear, and Waterbug, is an elite nation-state outfit that primarily targets authorities, diplomatic, and navy organizations utilizing a big set of customized malware.
Since the onset of Russia’s navy invasion of Ukraine in February 2022, the adversarial collective has been linked to a string of credential phishing and reconnaissance efforts aimed toward entities situated within the nation.
In July 2022, Google’s Threat Analysis Group (TAG) revealed that Turla created a malicious Android app to supposedly “assist” pro-Ukrainian hacktivists launch distributed denial-of-service (DDoS) assaults in opposition to Russian websites.
The newest discovery from Mandiant exhibits that Turla has been stealthily co-opting older infections as a malware distribution mechanism, to not point out benefiting from the truth that ANDROMEDA spreads through contaminated USB keys.
“USB spreading malware continues to be a helpful vector to realize preliminary entry into organizations,” the risk intelligence agency stated.
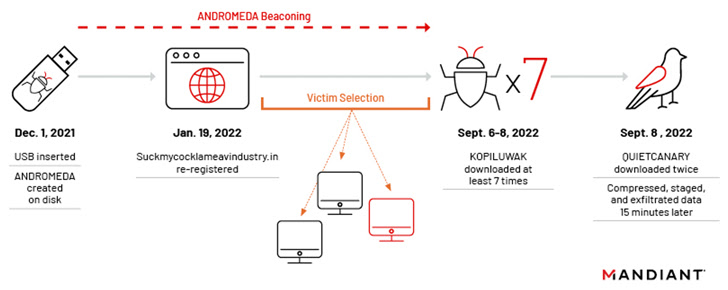
In the incident analyzed by Mandiant, an contaminated USB stick is alleged to have been inserted at an unnamed Ukrainian group in December 2021, finally resulting in the deployment of a legacy ANDROMEDA artifact on the host upon launching a malicious hyperlink (.LNK) file masquerading as a folder inside the USB drive.
The risk actor then repurposed one of many dormant domains that had been a part of ANDROMEDA’s defunct C2 infrastructure – which it re-registered in January 2022 – to profile the sufferer by delivering the first-stage KOPILUWAK dropper, a JavaScript-based community reconnaissance utility.
Two days later, on September 8, 2022, the assault proceeded to the ultimate part with the execution of a .NET-based implant dubbed QUIETCANARY (aka Tunnus), ensuing within the exfiltration of recordsdata created after January 1, 2021.
The tradecraft employed by Turla dovetails with prior experiences of the group’s intensive sufferer profiling efforts coinciding with the Russo-Ukrainian battle, probably serving to it tailor its follow-on exploitation efforts to reap the data of curiosity to Russia.
It’s additionally one of many uncommon cases the place a hacking unit has been recognized focusing on victims of a special malware marketing campaign to satisfy its personal strategic targets, whereas additionally obscuring its position.
“As older ANDROMEDA malware continues to unfold from compromised USB units, these re-registered domains pose a threat as new risk actors can take management and ship new malware to victims,” the researchers stated.
“This novel strategy of claiming expired domains utilized by extensively distributed, financially motivated malware can allow follow-on compromises at a big selection of entities. Further, older malware and infrastructure could also be extra prone to be ignored by defenders triaging all kinds of alerts.”
COLDRIVER Targets U.S. Nuclear Research Labs
The findings additionally come as Reuters reported that one other Russian state-sponsored risk group codenamed COLDRIVER (aka Callisto or SEABORGIUM) focused three nuclear analysis labs within the U.S. in early 2022.
To that finish, the digital assaults entailed creating pretend login pages for Brookhaven, Argonne, and Lawrence Livermore National Laboratories in an try and trick nuclear scientists into revealing their passwords.
The ways are in line with recognized COLDRIVER exercise, which not too long ago was unmasked spoofing the login pages of protection and intelligence consulting corporations in addition to NGOs, suppose tanks, and better training entities within the U.Ok. and the U.S.
[ad_2]