[ad_1]
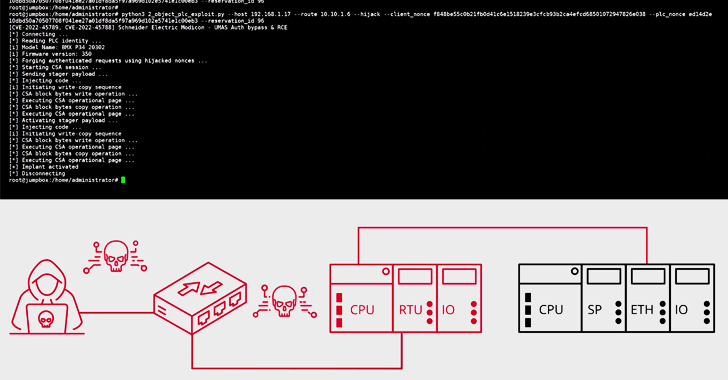
Security researchers have disclosed two new vulnerabilities affecting Schneider Electric Modicon programmable logic controllers (PLCs) that would enable for authentication bypass and distant code execution.
The flaws, tracked as CVE-2022-45788 (CVSS rating: 7.5) and CVE-2022-45789 (CVSS rating: 8.1), are a part of a broader assortment of safety defects tracked by Forescout as OT:ICEFALL.
Successful exploitation of the bugs might allow an adversary to execute unauthorized code, denial-of-service, or disclosure of delicate data.
The cybersecurity firm mentioned the shortcomings may be chained by a risk actor with recognized flaws from different distributors (e.g., CVE-2021-31886) to realize deep lateral motion in operational expertise (OT) networks.
“Deep lateral motion lets attackers acquire deep entry to industrial management programs and cross typically missed safety perimeters, permitting them to carry out extremely granular and stealthy manipulations in addition to override purposeful and security limitations,” Forescout mentioned.
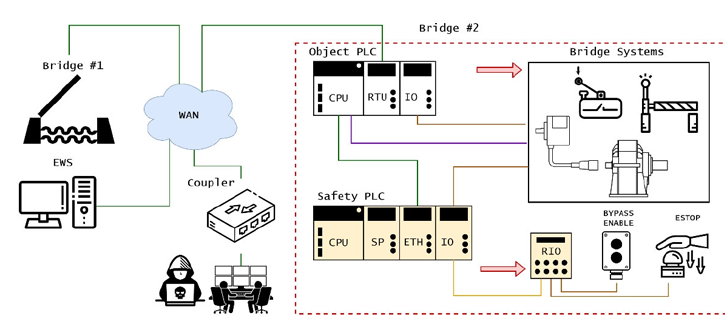
A extremely intricate proof-of-concept (PoC) cyber-physical assault devised by the San Jose-based agency discovered that the failings could possibly be weaponized to bypass security guardrails and inflict injury upon a movable bridge infrastructure.
With risk actors concocting refined malware to disrupt industrial management programs, the deep lateral motion afforded by these flaws might allow adversaries to make use of an “uninteresting gadget as a staging level for transferring in the direction of extra attention-grabbing targets.”
The findings come shut on the heels of 38 safety flaws that have been revealed in wi-fi industrial web of issues (IIoT) gadgets and which might grant an attacker a direct line of entry to OT networks, in response to cybersecurity firm Otorio.
Taken collectively, the weaknesses additionally underscore the true threats to bodily operations from IoT gadgets, cloud-based administration platforms, and nested OT networks.