[ad_1]
A shellcode-based packer dubbed TrickGate has been efficiently working with out attracting discover for over six years, whereas enabling risk actors to deploy a variety of malware akin to TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil over time.
“TrickGate managed to remain beneath the radar for years as a result of it’s transformative – it undergoes adjustments periodically,” Check Point Research’s Arie Olshtein mentioned, calling it a “grasp of disguises.”
Offered as a service to different risk actors since no less than late 2016, TrickGate helps conceal payloads behind a layer of wrapper code in an try and get previous safety options put in on a bunch. Packers also can operate as crypters by encrypting the malware as an obfuscation mechanism.
“Packers have totally different options that enable them to bypass detection mechanisms by showing as benign information, being tough to reverse engineer, or incorporating sandbox evasion methods,” Proofpoint famous in December 2020.
But the frequent updates to the industrial packer-as-a-service meant TrickGate has been tracked beneath varied names akin to new loader, Loncom, and NSIS-based crypter since 2019.
Telemetry information gathered by Check Point signifies that the risk actors leveraging TrickGate have primarily singled out the manufacturing sector, and to a lesser extent, schooling, healthcare, authorities, and finance verticals.
The hottest malware households used within the assaults prior to now two months embody FormBook, LokiBot, Agent Tesla, Remcos, and Nanocore, with important concentrations reported in Taiwan, Turkey, Germany, Russia, and China.
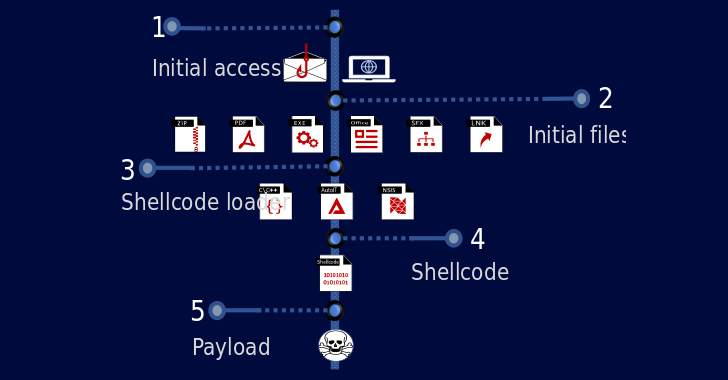
The an infection chain entails sending phishing emails with malicious attachments or booby-trapped hyperlinks that result in the obtain of a shellcode loader that is accountable for decrypting and launching the precise payload into reminiscence.
The Israeli cybersecurity agency’s evaluation of the shellcode exhibits that it “has been continually up to date, however the principle functionalities exist on all of the samples since 2016.” Olshtein famous “the injection module has been probably the most constant half over time and has been noticed in all TrickGate shellcodes.”