[ad_1]
Proof-of-concept (Poc) code has been launched for a now-patched high-severity safety flaw within the Windows CryptoAPI that the U.S. National Security Agency (NSA) and the U.Okay. National Cyber Security Centre (NCSC) reported to Microsoft final 12 months.
Tracked as CVE-2022-34689 (CVSS rating: 7.5), the spoofing vulnerability was addressed by the tech large as a part of Patch Tuesday updates launched in August 2022, however was solely publicly disclosed two months in a while October 11, 2022.
“An attacker might manipulate an current public x.509 certificates to spoof their id and carry out actions similar to authentication or code signing because the focused certificates,” Microsoft mentioned in an advisory launched on the time.
The Windows CryptoAPI gives an interface for builders so as to add cryptographic companies similar to encryption/decryption of information and authentication utilizing digital certificates to their functions.
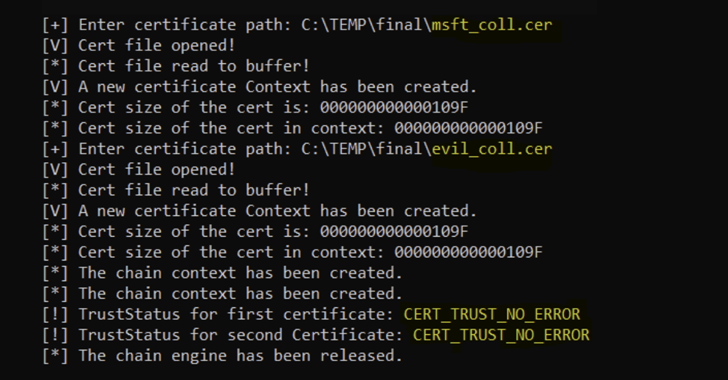
Web safety firm Akamai, which launched the PoC, mentioned CVE-2022-34689 is rooted in the truth that the susceptible piece of code that is designed to just accept an x.509 certificates carried out a examine that solely relied on the certificates’s MD5 fingerprint.
MD5, a message-digest algorithm used for hashing, is basically cryptographically damaged as of December 2008 owing to the danger of birthday assaults, a cryptanalytic methodology used to search out collisions in a hash perform.
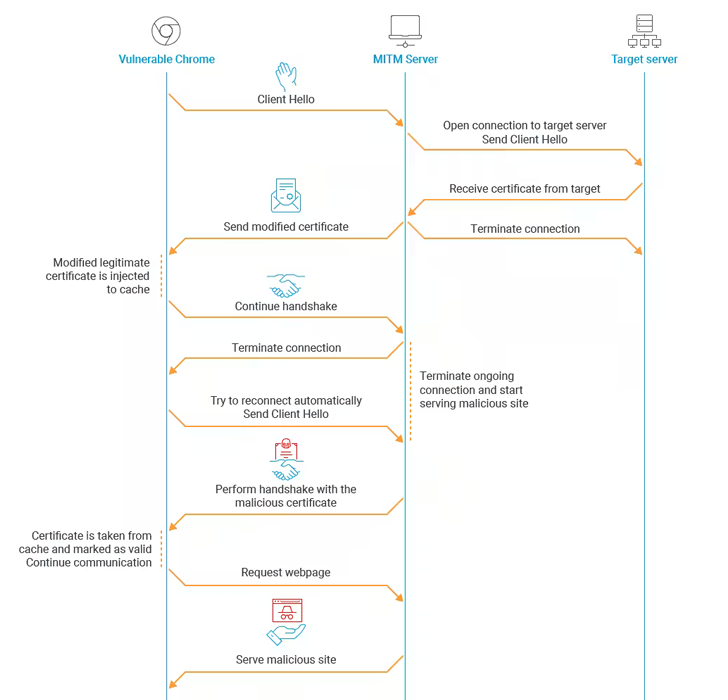
The web impact of this shortcoming is that it opens the door for a foul actor to serve a modified model of a professional certificates to a sufferer app, after which create a brand new certificates whose MD5 hash collides with the rigged certificates and use it to masquerade as the unique entity.
In different phrases, the flaw might be weaponized by a rogue interloper to stage a mallory-in-the-middle (MitM) assault and redirect customers counting on an outdated model of Google Chrome (model 48 and earlier) to an arbitrary web site of the actor’s selecting just because the inclined model of the online browser trusts the malicious certificates.
“Certificates play a significant position in id verification on-line, making this vulnerability profitable for attackers,” Akamai mentioned.
Although the flaw has a restricted scope, the Massachusetts-headquartered agency identified “there may be nonetheless numerous code that makes use of this API and is likely to be uncovered to this vulnerability, warranting a patch even for discontinued variations of Windows, like Windows 7.”