[ad_1]
New findings from cybersecurity agency JFrog present that malware concentrating on the npm ecosystem can evade safety checks by making the most of an “sudden conduct” within the npm command line interface (CLI) instrument.
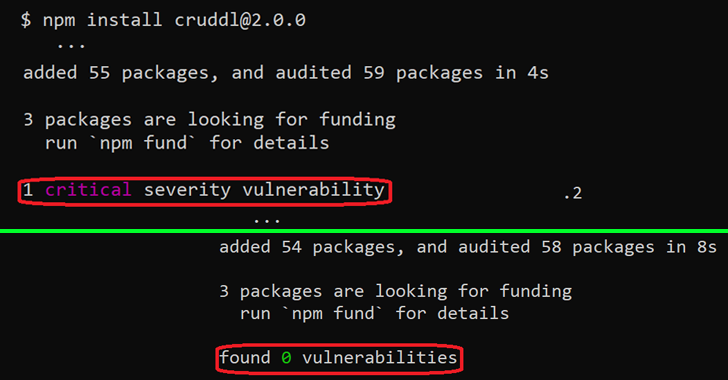
npm CLI’s set up and audit instructions have built-in capabilities to verify a package deal and all of its dependencies for recognized vulnerabilities, successfully appearing as a warning mechanism for builders by highlighting the failings.
But as JFrog established, the safety advisories are usually not displayed when the packages comply with sure model codecs, making a state of affairs the place crucial flaws could possibly be launched into their methods both straight or by way of the package deal’s dependencies.
Specifically, the issue arises solely when the put in package deal model comprises a hyphen (e.g., 1.2.3-a), which is included to indicate a pre-release model of an npm module.
While the mission maintainers deal with the discrepancy between common npm package deal variations and pre-release variations as an meant performance, this additionally makes it ripe for abuse by attackers seeking to poison the open supply ecosystem.
“Threat actors might exploit this conduct by deliberately planting susceptible or malicious code of their innocent-looking packages which might be included by different builders attributable to beneficial performance or as a mistake attributable to an infection methods comparable to typosquatting or dependency confusion,” Or Peles mentioned.
In different phrases, an adversary might publish a seemingly benign package deal that is within the pre-release model format, which might then be probably picked up by different builders and never be alerted to the truth that the package deal is malicious regardless of proof on the contrary.
The improvement as soon as once more reiterates how the software program provide chain is constructed as a series of belief between varied events, and the way a compromise of 1 hyperlink can have an effect on all downstream functions that eat the rogue third-party dependency.
To counter such threats, it is really helpful that builders keep away from putting in npm packages with a pre-release model, except the supply is thought to be utterly dependable.
[ad_2]