[ad_1]
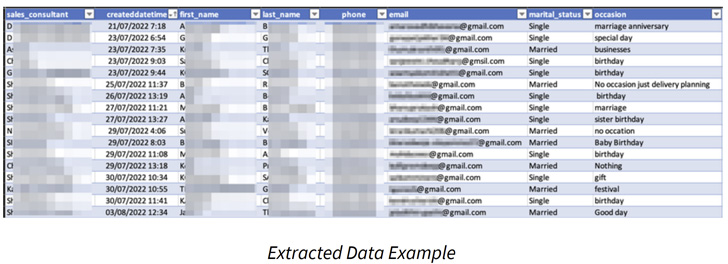
Hundreds of databases on Amazon Relational Database Service (Amazon RDS) are exposing private identifiable info (PII), new findings from Mitiga, a cloud incident response firm, present.
“Leaking PII on this method supplies a possible treasure trove for risk actors – both throughout the reconnaissance section of the cyber kill chain or extortionware/ransomware campaigns,” researchers Ariel Szarf, Doron Karmi, and Lionel Saposnik stated in a report shared with The Hacker News.
This contains names, e-mail addresses, telephone numbers, dates of delivery, marital standing, automobile rental info, and even firm logins.
Amazon RDS is a internet service that makes it attainable to arrange relational databases within the Amazon Web Services (AWS) cloud. It provides assist for various database engines akin to MariaDB, MySQL, Oracle, PostgreSQL, and SQL Server.
The root explanation for the leaks stems from a characteristic referred to as public RDS snapshots, which permits for making a backup of the complete database surroundings operating within the cloud and may be accessed by all AWS accounts.
“Make certain when sharing a snapshot as public that none of your non-public info is included within the public snapshot,” Amazon cautions in its documentation. “When a snapshot is shared publicly, it offers all AWS accounts permission each to repeat the snapshot and to create DB situations from it.”
The Israeli firm, which carried out the analysis from September 21, 2022, to October 20, 2022, stated it discovered 810 snapshots that had been publicly shared for various length, ranging from a number of hours to weeks, making them ripe for abuse by malicious actors.
Of the 810 snapshots, over 250 of the backups had been uncovered for 30 days, suggesting that they had been doubtless forgotten.
Based on the character of the knowledge uncovered, adversaries might both steal the info for monetary achieve or leverage it to get a greater grasp of an organization’s IT surroundings, which might then act as a stepping stone for covert intelligence gathering efforts.
It’s extremely really useful that RDS snapshots usually are not publicly accessible so as to forestall potential leak or misuse of delicate knowledge or some other form of safety risk. It’s additionally suggested to encrypt snapshots the place relevant.