[ad_1]

Ransomware actors have had a tough begin this 12 months, as stats from cybersecurity agency Coveware present corporations are more and more refusing to pay extortion calls for, resulting in a document low of 28% of corporations paying ransom within the first quarter of 2024.
This determine was 29% in This fall 2023, and Coveware’s stats present that diminishing funds have remained regular since early 2019.
This lower is because of organizations implementing extra superior protecting measures, mounting authorized strain to not meet the crooks’ monetary calls for, and cybercriminals repeatedly breaching guarantees to not publish or resale stolen knowledge if a ransom is paid.
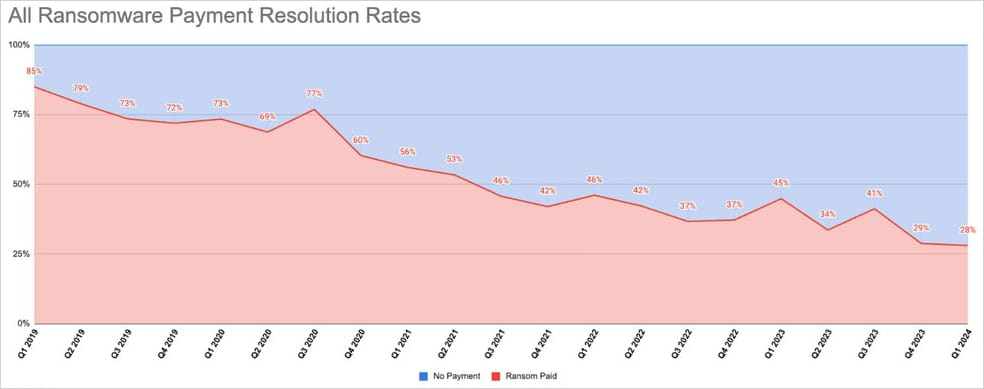
Source: Coveware
However, it’s important to notice that regardless of the drop within the cost price, the quantity paid to ransomware actors is increased than ever earlier than, reaching $1.1 billion final 12 months, in response to a Chainalysis report.
This is because of ransomware gangs hitting extra organizations by escalating their assault frequency and demanding extra substantial figures for not exposing stolen secrets and techniques and offering victims with a decryption key.
Concerning Q1 2024, Coveware reviews a 32% quarter-over-quarter (QoQ) drop within the common ransom cost, now at $381,980, and a 25% QoQ enhance within the median ransom cost, which stands at $250,000.
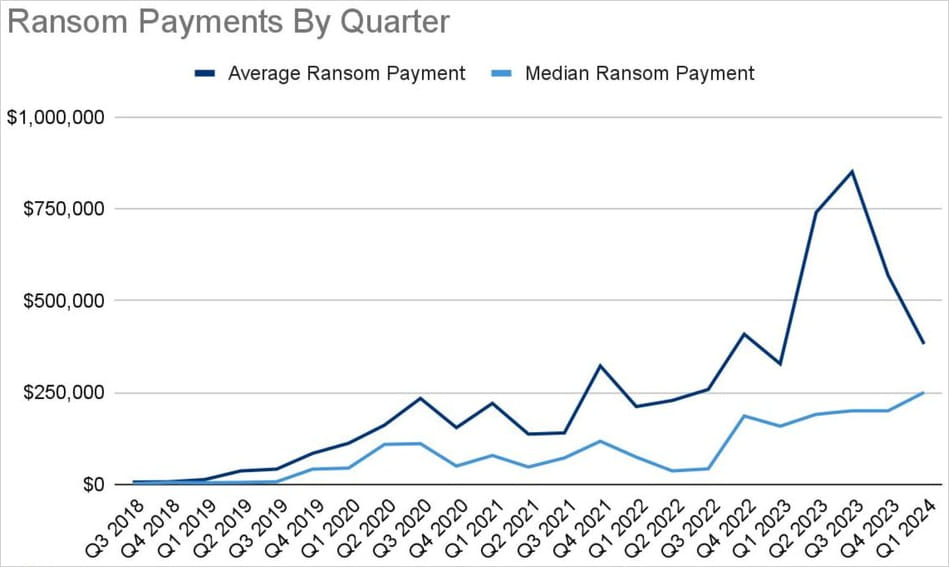
Source: Coveware
This simultaneous drop in common and rise in median ransom funds signifies a lower in high-figure funds and a rise in reasonable quantities. This might be attributable to ransom calls for changing into extra modest and/or fewer high-value targets succumbing to extortion.
Regarding preliminary infiltration strategies, there is a rising variety of instances the place that is unknown, reaching practically half of all reported instances within the first quarter of 2024.
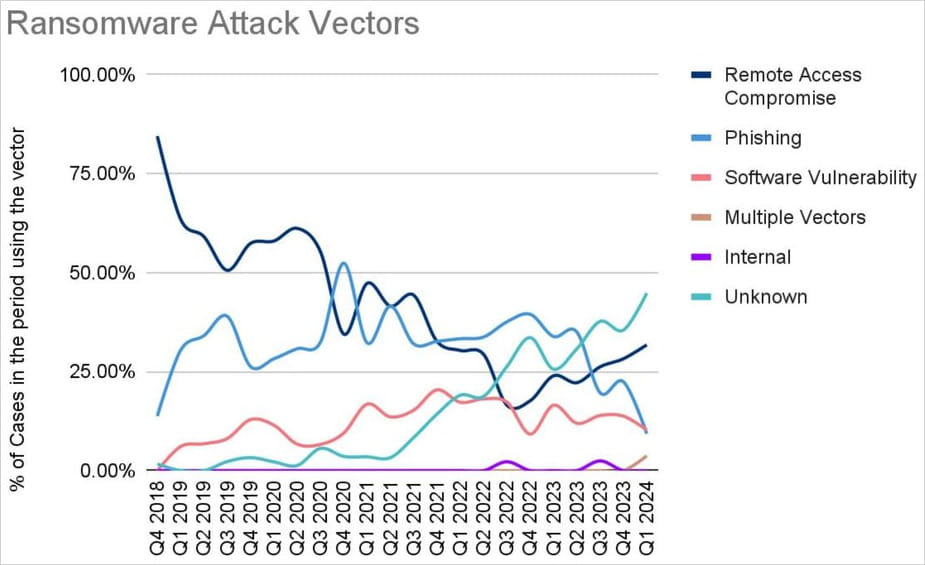
Coveware
From these which were decided, distant entry and vulnerability exploitation play the most important position, with the CVE-2023-20269, CVE-2023-4966, and CVE-2024-1708-9 flaws being the extra broadly exploited in Q1 by ransomware operators.
Law enforcement impact
Coveware reviews that the FBI’s LockBit disruption has had a large affect on the once-leading operation, as mirrored of their assault statistics. The operation additionally introduced turbulence to different main gangs, resulting in cost disputes and exit scams, equivalent to we noticed with BlackCat/ALPHV.
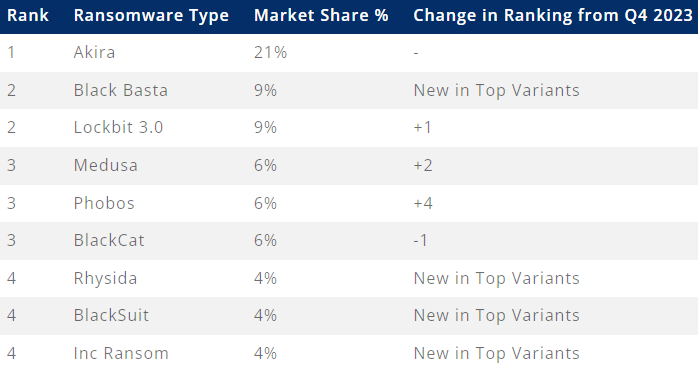
Source: Coveware
Moreover, these regulation enforcement operations have weakened the arrogance of different ransomware associates towards RaaS operators, with many deciding to function independently.
“We have already seen a rise in Babuk forks in current assaults, and a number of other former RaaS associates utilizing the ever-present, and nearly free, Dharma / Phobos companies,” explains Coveware within the report.
According to the safety agency, associates, in lots of instances, determined to give up cybercrime altogether.
“Most contributors within the cyber extortion ecosystems aren’t hardened criminals, somewhat they’re people with STEM expertise that stay in jurisdictions missing each extradition treaties, and ample professional financial alternatives to place their expertise to make use of,” continued Coveware.
“Some of those folks will view the elevated threat of getting in bother together with the danger of getting reduce out of their revenue as sufficient motive to give up.”
In this risky house, Akira tops the record with probably the most lively ransomware by way of assaults launched within the first quarter of the 12 months, remaining in place #1 for 9 months now.
The FBI reported this week that Akira is liable for breaches in at the least 250 organizations, pocketing $42 million in ransom funds.
