[ad_1]
Back in August 2022, Sophos X-Ops printed a white paper on a number of attackers – that’s, adversaries focusing on the identical organizations a number of instances. One of our key suggestions in that analysis was to stop repeated assaults by ‘prioritizing the worst bugs first’: patching vital or high-profile vulnerabilities that might have an effect on customers’ particular software program stacks. While we expect that is nonetheless good recommendation, prioritization is a posh challenge. How have you learnt what the worst bugs are? And how do you truly prioritize remediation, provided that sources are kind of the identical however the variety of printed CVEs per yr continues to extend, from 18,325 in 2020, to 25,277 in 2022, to 29,065 in 2023? And in accordance with current analysis, the median remediation capability throughout organizations is 15% of open vulnerabilities in any given month.
A typical strategy is to prioritize patching by severity (or by danger, a distinction we’ll make clear later) utilizing CVSS scores. FIRST’s Common Vulnerabilities Scoring System has been round for a very long time, supplies a numerical rating of vulnerability severity between 0.0 and 10.0, and isn’t solely broadly used for prioritization however mandated in some industries and governments, together with the Payment Card Industry (PCI) and components of the US federal authorities.
As for the way it works, it’s deceptively easy. You plug in particulars a couple of vulnerability, and out comes a quantity which tells you whether or not the bug is Low, Medium, High, or Critical. So far, so simple; you weed out the bugs that don’t apply to you, give attention to patching the Critical and High vulnerabilities out of what’s left, and both patch the Mediums and Lows afterwards or settle for the chance. Everything is on that 0-10 scale, so in idea that is straightforward to do.
But there’s extra nuance to it than that. In this text, the primary of a two-part sequence, we’ll check out what goes on below the hood of CVSS, and clarify why it isn’t essentially all that helpful for prioritization by itself. In the second half, we’ll focus on some different schemes which may present a extra full image of danger to tell prioritization.
Before we begin, an vital notice. While we’ll focus on some points with CVSS on this article, we’re very acutely aware that creating and sustaining a framework of this kind is difficult work, and to some extent a thankless process. CVSS is available in for lots of criticism, some pertaining to inherent points with the idea, and a few to the methods by which organizations use the framework. But we must always level out that CVSS is just not a business, paywalled software. It is made free for organizations to make use of as they see match, with the intent of offering a helpful and sensible information to vulnerability severity and due to this fact serving to organizations to enhance their response to printed vulnerabilities. It continues to endure enhancements, typically in response to exterior suggestions. Our motivation in writing these articles is just not in any technique to disparage the CVSS program or its builders and maintainers, however to supply further context and steering round CVSS and its makes use of, particularly close to remediation prioritization, and to contribute to a wider dialogue round vulnerability administration.
CVSS is “a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity,” in accordance with FIRST. That numerical rating, as talked about earlier, is between 0.0 and 10.0, giving 101 attainable values; it could then be become a qualitative measure utilizing the next scale:
- None: 0.0
- Low: 0.1 – 3.9
- Medium: 4.0 – 6.9
- High: 7.0 – 8.9
- Critical: 9.0 – 10.0
The system has been round since February 2005, when model 1 was launched; v2 got here out in June 2007, adopted by v3 in June 2015. v3.1, launched in June 2019, has some minor amendments from v3, and v4 was printed on October 31, 2023. Because CVSS v4 has not but been broadly adopted as of this writing (e.g., the National Vulnerability Database (NVD) and lots of distributors together with Microsoft are nonetheless predominantly utilizing v3.1), we’ll take a look at each variations on this article.
CVSS is the de facto normal for representing vulnerability severity. It seems on CVE entries within the NVD in addition to in varied different vulnerability databases and feeds. The thought is that it produces a single, standardized, platform-agnostic rating.
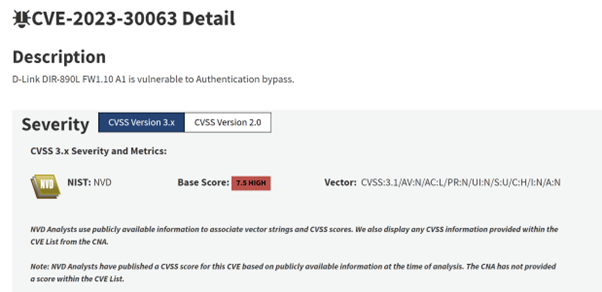
Figure 1: The entry for CVE-2023-30063 on the NVD. Note the v3.1 Base Score (7.5, High) and the vector string, which we’ll cowl in additional element shortly. Also notice that as of March 2024, the NVD doesn’t incorporate CVSS v4 scores
The determine most suppliers use is the Base Score, which displays a vulnerability’s intrinsic properties and its potential impacts. Calculating a rating entails assessing a vulnerability through two sub-categories, every with its personal vectors which feed into the general equation.
The first subcategory is Exploitability, which accommodates the next vectors (attainable values are in brackets) in CVSS v4:
- Attack Vector (Network, Adjacent, Local, Physical)
- Attack Complexity (Low, High)
- Attack Requirements (None, Present)
- Privileges Required (None, Low, High)
- User Interaction (None, Passive, Active)
The second class is Impact. Each of the vectors beneath have the identical three attainable values (High, Low, and None):
- Vulnerable System Confidentiality
- Subsequent System Confidentiality
- Vulnerable System Integrity
- Subsequent System Integrity
- Vulnerable System Availability
- Subsequent System Availability
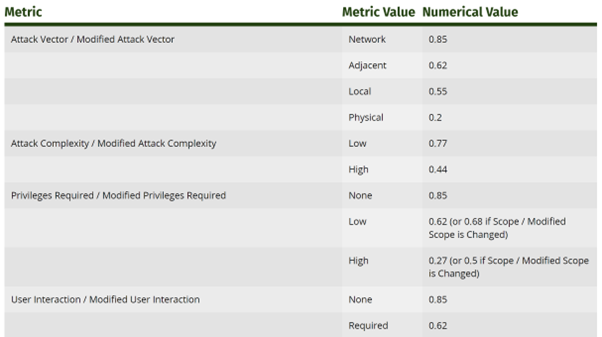
So how will we get to an precise quantity after supplying these values? In v3.1, as proven in FIRST’s CVSS specification doc, the metrics (barely completely different to the v4 metrics listed above) have an related numerical worth:
Figure 2: An excerpt from FIRST’s CVSS v3.1 documentation, exhibiting the numerical values of assorted metrics
To calculate the v3.1 Base rating, we first calculate three sub-scores: an Impact Sub-Score (ISS), an Impact Score (which makes use of the ISS), and an Exploitability Score.
Impact Sub-Score
1 – [(1 – Confidentiality) * (1 – Integrity) * (1 – Availability)]
Impact Score
- If scope is unchanged, 42 * ISS
- If scope is modified, 52 * (ISS – 0.029) – 3.25 * (ISS – 0.02)15
Exploitability Score
8.22 * AttackVector * AttackComplexity * PrivilegesRequired * UserInteraction
Base Score
Assuming the Impact Score is bigger than 0:
- If scope is unchanged: (Roundup (Minimum [(Impact + Exploitability), 10])
- If scope is modified: Roundup (Minimum [1.08 * (Impact + Exploitability), 10])
Here, the equation makes use of two customized features, Roundup and Minimum. Roundup “returns the smallest number, specified to one decimal place, that is equal to or higher than its input,” and Minimum “returns the smaller of its two arguments.”
Given that CVSS is an open-source specification, we will work by means of an instance of this manually, utilizing the v3.1 vector string for CVE-2023-30063 proven in Figure 1:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
We’ll search for the vector outcomes and their related numerical values, so we all know what numbers to plug into the equations:
- Attack Vector = Network = 0.85
- Attack Complexity = Low = 0.77
- Privileges Required = None = 0.85
- User Interaction = None = 0.85
- Scope = Unchanged (no related worth in itself; as an alternative, Scope can modify different vectors)
- Confidentiality = High = 0.56
- Integrity = None = 0
- Availability = None = 0
First, we calculate the ISS:
1 – [(1 – 0.56) * (1 – 0) * (1 – 0] = 0.56
The Scope is unchanged, so for the Impact rating we multiply the ISS by 6.42, which supplies us 3.595.
The Exploitability rating is 8.22 * 0.85 * 0.77 * 0.85 * 0.85, which supplies us 3.887.
Finally, we put this all into the Base Score equation, which successfully provides these two scores collectively, giving us 7.482. To one decimal place that is 7.5, as per the CVSS v3.1 rating on NVD, which implies this vulnerability is taken into account to be High severity.
v4 takes a really completely different strategy. Among different modifications, the Scope metric has been retired; there’s a new Base metric (Attack Requirements); and the User Interaction now has extra granular choices. But essentially the most radical change is the scoring system. Now, the calculation technique not depends on ‘magic numbers’ or a system. Instead, ‘equivalence sets’ of various mixtures of values have been ranked by specialists, compressed, and put into bins representing scores. When calculating a CVSS v4 rating, the vector is computed and the related rating returned, utilizing a lookup desk. So, for instance, a vector of 202001 has an related rating of 6.4 (Medium).
Regardless of the calculation technique, the Base Score isn’t supposed to vary over time, because it depends on traits inherent to the vulnerability. However, the v4 specification additionally presents three different metric teams: Threat (the traits of a vulnerability that change over time); Environmental (traits which are distinctive to a consumer’s setting); and Supplemental (further extrinsic attributes).
The Threat Metric Group contains just one metric (Exploit Maturity); this replaces the Temporal Metric Group from v3.1, which included metrics for Exploit Code Maturity, Remediation Level, and Report Confidence. The Exploit Maturity metric is designed to mirror the probability of exploitation, and has 4 attainable values:
- Not Defined
- Attacked
- Proof-of-Concept
- Unreported
Whereas the Threat Metric Group is designed so as to add further context to a Base rating primarily based on risk intelligence, the Environmental Metric Group is extra of a variation of the Base rating, permitting a company to customise the rating “depending on the importance of the affected IT asset to a user’s organization.” This metric accommodates three sub-categories (Confidentiality Requirement, Integrity Requirement, and Availability Requirement), plus the modified Base metrics. The values and definitions are the identical because the Base metrics, however the modified metrics enable customers to mirror mitigations and configurations which can improve or lower severity. For instance, the default configuration of a software program element may not implement authentication, so a vulnerability in that element would have a Base metric of None for the Privileges Required measure. However, a company might need protected that element with a password of their setting, by which case the Modified Privileges Required could be both Low or High, and the general Environmental rating for that group would due to this fact be decrease than the Base rating.
Finally, the Supplemental Metric Group contains the next optionally available metrics, which don’t have an effect on the rating.
- Automatable
- Recovery
- Safety
- Value Density
- Vulnerability Response Effort
- Provider Urgency
It stays to be seen how broadly used the Threat and Supplemental Metric Groups might be in v4. With v3.1, Temporal metrics hardly ever seem on vulnerability databases and feeds, and Environmental metrics are meant for use on a per-infrastructure foundation, so it’s not clear how broadly adopted they’re.
However, Base scores are ubiquitous, and at first look it’s not laborious to see why. Even although lots has modified in v4, the basic nature of the end result – a determine between 0.0 and 10.0, which purportedly displays a vulnerability’s severity – is identical.
The system has, nevertheless, are available in for some criticism.
What does a CVSS rating imply?
This isn’t an issue inherent to the CVSS specification, however there will be some confusion as to what a CVSS rating truly means, and what it ought to be used for. As Howland factors out, the specification for CVSS v2 is evident that the framework’s objective is danger administration:
“Currently, IT management must identify and assess vulnerabilities across many disparate hardware and software platforms. They need to prioritize these vulnerabilities and remediate those that pose the greatest risk. But when there are so many to fix, with each being scored using different scales, how can IT managers convert this mountain of vulnerability data into actionable information? The Common Vulnerability Scoring System (CVSS) is an open framework that addresses this issue.”
The phrase ‘risk’ seems 21 instances within the v2 specification; ‘severity’ solely three. By the v4 specification, these numbers have successfully reversed; ‘risk’ seems 3 times, and ‘severity’ 41 instances. The first sentence of the v4 specification states that the aim of the framework is “communicating the characteristics and severity of software vulnerabilities.” So, sooner or later, the said objective of CVSS has modified, from a measure of danger to a measure of severity.
That’s not a ‘gotcha’ in any approach; the authors could have merely determined to make clear precisely what CVSS is for, to stop or handle misunderstandings. The actual challenge right here doesn’t lie within the framework itself, however in the way in which it’s typically carried out. Despite the clarifications in current specs, CVSS scores should typically be (mis)used as a measure of danger (i.e., “the combination of the probability of an event and its consequences,” or, as per the oft-cited system, Threat * Vulnerability * Consequence), however they don’t truly measure danger in any respect. They measure one side of danger, in assuming that an attacker “has already located and identified the vulnerability,” and in assessing the traits and potential affect of that vulnerability if an exploit is developed, and if that exploit is efficient, and if the affordable worst-case situation happens because of this.
A CVSS rating generally is a piece of the puzzle, however under no circumstances the finished jigsaw. While it might be good to have a single quantity on which to base choices, danger is a much more complicated sport.
But I can nonetheless use it for prioritization, proper?
Yes and no. Despite the growing numbers of printed CVEs (and it’s price declaring that not all vulnerabilities obtain CVE IDs, in order that’s not a accomplished jigsaw both), solely a small fraction – between 2% and 5% – are ever detected as being exploited in-the-wild, in accordance with analysis. So, if a vulnerability intelligence feed tells you that 2,000 CVEs have been printed this month, and 1,000 of them have an effect on property in your group, solely round 20-50 of these will probably ever be exploited (that we’ll learn about).
That’s the excellent news. But, leaving apart any exploitation that happens earlier than a CVE’s publication, we don’t know which CVEs risk actors will exploit sooner or later, or when – so how can we all know which vulnerabilities to patch first? One would possibly assume that risk actors use an identical thought course of to CVSS, albeit much less formalized, to develop, promote, and use exploits: emphasizing high-impact vulnerabilities with low complexity. In which case, prioritizing excessive CVSS scores for remediation makes good sense.
But researchers have proven that CVSS (not less than, as much as v3) is an unreliable predictor of exploitability. Back in 2014, researchers on the University of Trento claimed that “fixing a vulnerability just because it was assigned a high CVSS score is equivalent to randomly picking vulnerabilities to fix,” primarily based on an evaluation of publicly accessible knowledge on vulnerabilities and exploits. More not too long ago (March 2023), Howland’s analysis on CVSS exhibits that bugs with a CVSS v3 rating of seven are the most certainly to be weaponized, in a pattern of over 28,000 vulnerabilities. Vulnerabilities with scores of 5 had been extra prone to be weaponized than these with scores of 6, and 10-rated vulnerabilities – Critical flaws – had been much less prone to have exploits developed for them than vulnerabilities ranked as 9 or 8.
In different phrases, there doesn’t look like a correlation between CVSS rating and the probability of exploitation, and, in accordance with Howland, that’s nonetheless the case even when we weight related vectors – like Attack Complexity or Attack Vector – extra closely (though it stays to be seen if this can nonetheless maintain true with CVSS v4).
This is a counterintuitive discovering. As the authors of the Exploit Prediction Scoring System (EPSS) level out (extra on EPSS in our follow-up article), after plotting CVSS scores towards EPSS scores and discovering much less correlation than anticipated:
“this…provides suggestive evidence that attackers are not only targeting vulnerabilities that produce the greatest impact, or are necessarily easier to exploit (such as for example, an unauthenticated remote code execution).”
There are varied the explanation why the idea that attackers are most serious about exploiting exploits for extreme, low-effort vulnerabilities doesn’t maintain up. As with danger, the legal ecosystem can’t be decreased to a single side. Other elements which could have an effect on the probability of weaponization embody the set up base of the affected product; prioritizing sure impacts or product households over others; variations by crime sort and motivation; geography, and so forth. This is a posh, and separate, dialogue, and out of scope for this text – however, as Jacques Chester argues in an intensive and thought-provoking weblog put up on CVSS, the primary takeaway is: “Attackers do not appear to use CVSSv3.1 to prioritize their efforts. Why should defenders?” Note, nevertheless, that Chester doesn’t go as far as to argue that CVSS shouldn’t be used in any respect. But it in all probability shouldn’t be the only real think about prioritization.
Reproducibility
One of the litmus checks for a scoring framework is that, given the identical info, two folks ought to be capable of work by means of the method and are available out with roughly the identical rating. In a area as complicated as vulnerability administration, the place subjectivity, interpretation, and technical understanding typically come into play, we would fairly count on a level of deviation – however a 2018 examine confirmed vital discrepancies in assessing the severity of vulnerabilities utilizing CVSS metrics, even amongst safety professionals, which might end in a vulnerability being finally categorized as High by one analyst and Critical or Medium by one other.
However, as FIRST factors out in its specification doc, its intention is that CVSS Base scores ought to be calculated by distributors or vulnerability analysts. In the true world, Base scores usually seem on public feeds or databases which organizations then ingest – they’re not meant to be recalculated by plenty of particular person analysts. That’s reassuring, though the truth that skilled safety professionals made, in some instances not less than, fairly completely different assessments could possibly be a trigger for concern. It’s not clear whether or not that was a consequence of ambiguity in CVSS definitions, or a scarcity of CVSS scoring expertise among the many examine’s individuals, or a wider challenge regarding divergent understanding of safety ideas, or some or the entire above. Further analysis might be wanted on this level, and on the extent to which this challenge nonetheless applies in 2024, and to CVSS v4.
Harm
CVSS v3.1’s affect metrics are restricted to these related to conventional vulnerabilities in conventional environments: the acquainted CIA triad. What v3.1 doesn’t take note of are more moderen developments in safety, the place assaults towards techniques, gadgets, and infrastructure may cause vital bodily hurt to folks and property.
However, v4 does handle this challenge. It features a devoted Safety metric, with the next attainable values:
- Not Defined
- Present
- Negligible
With the latter two values, the framework makes use of the IEC 61508 normal definitions of “negligible” (minor accidents at worst), “marginal” (main accidents to a number of individuals), “critical” (lack of a single life), or “catastrophic” (a number of lack of life). The Safety metric will also be utilized to the modified Base metrics throughout the Environmental Metric Group, for the Subsequent System Impact set.
Context is the whole lot
CVSS does its finest to maintain the whole lot so simple as attainable, which may typically imply lowering complexity. Take v4’s Attack Complexity, for instance; the one two attainable values are Low and High.
Low: “The attacker must take no measurable action to exploit the vulnerability. The attack requires no target-specific circumvention to exploit the vulnerability. An attacker can expect repeatable success against the vulnerable system.”
High: “The successful attack depends on the evasion or circumvention of security-enhancing techniques in place that would otherwise hinder the attack […].”
Some risk actors, vulnerability analysts, and distributors would probably disagree with the view {that a} vulnerability is both of ‘low’ or ‘high’ complexity. However, members of the FIRST Special Interest Group (SIG) declare that this has been addressed in v4 with the brand new Attack Requirements metric, which provides some granularity to the combo by capturing whether or not exploitation requires sure circumstances.
User Interaction is one other instance. While the attainable values for this metric are extra granular in v4 than v3.1 (which has solely None or Required), the excellence between Passive (restricted and involuntary interplay) and Active (particular and acutely aware interplay) arguably fails to mirror the wide selection of social engineering which happens in the true world, to not point out the complexity added by safety controls. For occasion, persuading a consumer to open a doc (or simply view it within the Preview Pane) is most often simpler than persuading them to open a doc, then disable Protected View, then ignore a safety warning.
In equity, CVSS should stroll a line between being overly granular (i.e., together with so many attainable values and variables that it might take an inordinate period of time to calculate scores) and overly simplistic. Making the CVSS mannequin extra granular would complicate what’s meant to be a fast, sensible, one-size-fits-all information to severity. That being mentioned, it’s nonetheless the case that vital nuance could also be missed – and the vulnerability panorama is, by nature, typically a nuanced one.
Some of the definitions in each the v3.1 and v4 specs may be complicated to some customers. For occasion, take into account the next, which is offered as a attainable situation below the Attack Vector (Local) definition:
“the attacker exploits the vulnerability by accessing the target system locally (e.g., keyboard, console), or through terminal emulation (e.g., SSH)” [emphasis added; in the v3.1 specification, this reads “or remotely (e.g., SSH)”]
Note that using SSH right here seems to be distinct from accessing a number on an area community through SSH, as per the Adjacent definition:
“This can mean an attack must be launched from the same shared proximity (e.g., Bluetooth, NFC, or IEEE 802.11) or logical (e.g., local IP subnet) network, or from within a secure or otherwise limited administrative domain…” [emphasis added]
While the specification does make a distinction between a susceptible element being “bound to the network stack” (Network) or not (Local), this could possibly be counterintuitive or complicated to some customers, both when calculating CVSS scores or trying to interpret a vector string. That’s to not say these definitions are incorrect, solely that they is perhaps opaque and unintuitive to some customers.
Finally, Howland supplies a real-world case examine of, of their view, CVSS scores not taking context under consideration. CVE-2014-3566 (the POODLE vulnerability) has a CVSS v3 rating of three.4 (Low). But it affected virtually 1,000,000 web sites on the time of disclosure, precipitated a major quantity of alarm, and impacted completely different organizations in several methods – which, Howland argues, CVSS doesn’t take note of. There’s additionally a separate context-related query – out of scope for this sequence – on whether or not media protection and hype a couple of vulnerability disproportionately affect prioritization. Conversely, some researchers have argued that vulnerability rankings will be overly excessive as a result of they don’t all the time take context under consideration, when the real-world danger is definitely comparatively low.
‘We’re simply ordinally folks…’
In v3.1, CVSS typically makes use of ordinal knowledge as enter into equations. Ordinal knowledge is knowledge on a ranked scale, with no recognized distance between gadgets (e.g., None, Low, High), and, as researchers from Carnegie Mellon University level out, it doesn’t make sense so as to add or multiply ordinal knowledge gadgets. If, as an example, you’re finishing a survey the place the responses are on a Likert scale, it’s meaningless to multiply or add these responses. To give a non-CVSS instance, in the event you reply Happy [4.0] to a query about your wage, and Somewhat Happy [2.5] to a query about your work-life stability, you may’t multiply these collectively and conclude that the general survey consequence = 10.0 [‘Very happy with my job’].
The use of ordinal knowledge additionally implies that CVSS scores shouldn’t be averaged. If an athlete wins a gold medal in a single occasion, for instance, and a bronze medal in one other, it doesn’t make sense to say that on common they gained silver.
In v3.1, it’s additionally not clear how the metrics’ hardcoded numerical values had been chosen, which can be one of many causes for FIRST opting to eschew a system in v4. Instead, v4’s scoring system depends on grouping and rating attainable mixtures of values, calculating a vector, and utilizing a lookup perform to assign a rating. So, as an alternative of a system, specialists chosen by FIRST have decided the severity of various mixtures of vectors throughout a session interval. On the face of it, this looks like an affordable strategy, because it negates the difficulty of a system altogether.
A black field?
While the specification, equations, and definitions for v3.1 and v4 are publicly accessible, some researchers have argued that CVSS suffers from a scarcity of transparency. In v4, for instance, somewhat than plugging numbers right into a system, analysts can now search for a vector utilizing a predetermined checklist. However, it’s not clear how these specialists had been chosen, how they in contrast “vectors representing each equivalence set,” or how the “expert comparison data” was used “to calculate the order of vectors from least severe to most severe.” To our information, this info has not been made public. As we’ll see in Part 2 of this sequence, this challenge is just not distinctive to CVSS.
As with something in safety, any outcomes produced by a system by which the underlying mechanics usually are not absolutely recognized or understood ought to be handled with a level of skepticism commensurate with the significance and nature of the aim for which they’re used – and with the extent of related danger if these outcomes ought to show to be fallacious or deceptive.
Capping it off
Finally, it might be price questioning why CVSS scores are between 0 and 10 in any respect. The apparent reply is that it is a easy scale which is simple to know, but it surely’s additionally arbitrary, particularly because the inputs to the equations are qualitative and CVSS is just not a likelihood measure. In v3.1, the Minimum perform ensures that scores are capped at 10 (with out it, it’s attainable for a Base rating to succeed in 10.73, not less than by our calculations) – and in v4, the vectoring mechanism caps scores at 10 by design, as a result of it’s the best ‘bin.’
But is there a most extent to which a vulnerability will be extreme? Are all vulnerabilities which rating 10.0 equally dangerous? Likely this selection was made for human readability – however is it at the price of an correct and real looking illustration of severity?
A fast, if imperfect, thought experiment: Imagine a scoring system that claims to measure the severity of organic viruses. The scores can inform you concerning the attainable affect a virus might need on folks, even perhaps one thing concerning the potential risk of the virus primarily based on a few of its traits (e.g., an airborne virus is prone to be a extra widespread risk than a virus that may solely be transmitted through ingestion or bodily contact, albeit not essentially a extra extreme one).
After inputting details about the virus into an equation, the system generates a really easy-to-understand numerical rating between 0 and 10. Parts of the healthcare sector use these scores to prioritize their responses to viruses, and a few of the normal public depend on them as an indicator of danger – despite the fact that that’s not what the system’s builders advise.
But what the scores can’t inform you is how a virus will affect you personally, primarily based in your age, well being, immune system effectivity, co-morbidities, immunity through earlier an infection, and so forth. They can’t inform you how probably you’re to get contaminated, or how lengthy it should take you to get well. They don’t take into account the entire viruses’ properties (replication price and talent to mutate, as an example, or geographic distribution of reservoirs and infections) or take wider context under consideration, akin to whether or not there are vaccines or preventative measures accessible. As a consequence, a few of the scores appear to make sense (HIV ranks greater than a standard rhinovirus, for instance), however others don’t (poliovirus scores extremely due to its attainable impacts, regardless of being nearly eradicated in many of the world). And unbiased empirical analysis has proven that the system’s scores usually are not useful in predicting morbidity charges.
So, do you have to rely solely on this method for conducting private danger assessments – say, when deciding to attend a celebration, or go on vacation, or go to somebody in hospital? Should the medical neighborhood depend on it to prioritize scientific analysis and epidemiological efforts?
Intuitively, most individuals would probably have some doubts; it’s clear that the system has some flaws. However, it’s actually not redundant. It’s useful for categorization, and for highlighting attainable threats primarily based on a virus’s intrinsic properties, as a result of its scores inform you one thing concerning the potential penalties of an infection. It’s helpful, for instance, to know that rabies is inherently extra extreme than chickenpox, even in the event you’re unlikely to contract rabies in your subsequent night time out. You might actually take this method’s scores under consideration when conducting a danger evaluation, along with different info. But you’d additionally need extra info.
And, in equity, FIRST makes this level in its FAQ doc for v4. In discussing different scoring techniques, it notes that they “can be used in concert to better assess, predict, and make informed decisions on vulnerability response priority.” In the subsequent article, we’ll focus on a few of these different techniques.
[ad_2]