[ad_1]
A brand new model of the Prilex POS malware has discovered a novel technique to steal your bank card data.

According to Kaspersky, Prilex is a Brazilian risk actor that originally started in 2014 as an ATM-related malware and later switched to modular point-of-service malware. The risk actor was accountable for one of many largest assaults on ATMs in Brazil, infecting and jackpotting greater than 1,000 machines and cloning greater than 28,000 bank cards used within the ATMs.
SEE: Mobile gadget safety coverage (TechRepublic Premium)
Prilex is especially skilled with fee markets, digital funds switch software program and protocols, and the risk actor has just lately up to date its POS malware to dam contactless transactions to steal your bank card data.
Jump to:
What’s new within the newest Prilex malware
Contactless fee strategies have develop into extremely in style, particularly for the reason that COVID-19 pandemic when individuals wished to the touch as public surfaces as attainable. Such funds require the bank card to be actually near the fee gadget, which is usually a POS terminal.
As contactless funds aren’t dealt with by the POS terminal in the identical method as traditional funds, it’s not attainable for cybercriminals to abuse and make fraudulent use of the system. This resulted in cybercriminals’ POS malware seeing an enormous lower within the variety of transactions it might abuse.
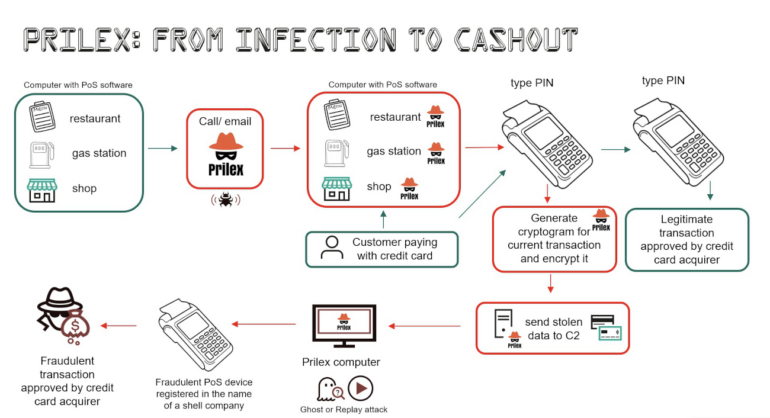
Prilex malware builders have discovered a technique to cope with this downside: The malware, as soon as it sees a contactless transaction occur, blocks it. The PIN pad then tells the consumer that there’s a contactless error and that the fee must be accomplished by inserting the bank card. Once the sufferer pays by card, a GHOST transaction fraud could be operated by Prilex.
In GHOST transactions, the malware sits on the gadget, intercepting all communications between the POS software program and the PIN pad. Once a transaction is ongoing, the malware intercepts the transaction content material and modifies it so as to seize the bank card data and request new EMV cryptograms to the victims card. The new EMV cryptogram permits the attacker to provoke a brand new fraudulent transaction from a POS gadget they personal (Figure A).
Figure A
How do POS malware infections work?
POS malware just isn’t your common malware. Developing it requires a deep understanding of the entire fee market in addition to its protocols, instruments and deployment. As such malware is ineffective on traditional endpoints, it must be executed on the computer systems who truly run the POS software program and cope with funds.
The cybercriminals behind superior POS malware can not simply ship phishing emails to contaminate computer systems; they should goal particular individuals and use social engineering schemes to entice the sufferer to put in a official distant desktop utility earlier than infecting it. This explains why the fraudsters usually faux to be technicians who have to replace the official POS software program.
How to guard your group from this risk
The finish buyer can’t do something in opposition to the risk, because it occurs on contaminated units that they will’t management. All safety should come from directors of POS software program.
As an organization utilizing POS programs, set up an in depth course of with the POS supplier so as to keep away from any social engineering scams. All contacts between the POS software program buyer and the POS software program supplier have to observe particular guidelines that ought to be mentioned over a safe channel and identified by anybody who might entry the units working the POS software program. Should any cybercriminal name and faux to be an worker of the POS software program provider, this is able to assist to right away uncover them.
Security options ought to be deployed on all units working POS software program to attempt to detect malware an infection. As data is shipped from an contaminated POS gadget to an attacker owned C2, community communications must also be monitored so as to detect any suspicious exercise that could possibly be a communication between a malware and a C2 server.
Finally, all software program and working programs ought to all the time be updated and patched so as to keep away from compromise by widespread vulnerabilities.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
