[ad_1]
As the digital age evolves and continues to form the enterprise panorama, company networks have grow to be more and more complicated and distributed. The quantity of information an organization collects to detect malicious behaviour continually will increase, making it difficult to detect misleading and unknown assault patterns and the so-called “needle within the haystack”. With a rising variety of cybersecurity threats, corresponding to knowledge breaches, ransomware assaults, and malicious insiders, organizations are dealing with vital challenges in efficiently monitoring and securing their networks. Furthermore, the expertise scarcity within the area of cybersecurity makes handbook risk looking and log correlation a cumbersome and tough activity. To handle these challenges, organizations are turning to predictive analytics and Machine Learning (ML) pushed community safety options as important instruments for securing their networks in opposition to cyber threats and the unknown dangerous.
The Role of ML-Driven Network Security Solutions
ML-driven community safety options in cybersecurity confer with using self-learning algorithms and different predictive applied sciences (statistics, time evaluation, correlations and many others.) to automate varied elements of risk detection. The use of ML algorithms is changing into more and more well-liked for scalable applied sciences because of the limitations current in conventional rule-based safety options. This leads to the processing of information by way of superior algorithms that may determine patterns, anomalies, and different refined indicators of malicious exercise, together with new and evolving threats that will not have identified dangerous indicators or present signatures.
Detecting identified risk indicators and blocking established assault patterns continues to be a vital a part of total cyber hygiene. However, conventional approaches utilizing risk feeds and static guidelines can grow to be time-consuming in terms of sustaining and masking all of the completely different log sources. In addition, Indicators of Attack (IoA) or Indicators of Compromise (IoC) is probably not out there on the time of an assault or are shortly outdated. Consequently, corporations require different approaches to fill this hole of their cybersecurity posture.
In abstract, the talked about drawbacks of rule-based safety options spotlight the importance of taking a extra holistic method to community safety, which ought to these days embody ML-powered Network Detection and Response (NDR) options to enrich conventional detection capabilities and preventive safety measures.
The Benefits of ML for Network Security
So, how is Machine Learning (ML) shaping the way forward for community safety? The fact is ML-powered safety options are bringing a few vital transformation in community safety by offering safety groups with quite a few advantages and enhancing the general risk detection capabilities of organizations:
- Big knowledge analytics:With the ever-increasing quantity of information and completely different log sources, organisations should be capable to course of huge quantities of data in real-time, together with community site visitors logs, endpoints, and different sources of data associated to cyber threats. In this regard, ML algorithms can support within the detection of safety threats by figuring out patterns and anomalies that will in any other case go unnoticed. Consequently, the flexibility and adaptability of an answer to include completely different log sources must be a key requirement for risk detection capabilities.
- Automated evaluation of anomalous habits: AI permits a much-required well being monitoring of community exercise by utilising the evaluation of regular community site visitors as a baseline. With the assistance of automated correlation and clustering, outliers and strange habits might be detected, decreasing the necessity for handbook detection engineering and risk looking. Key inquiries to be answered embody “what’s the exercise of different shoppers within the community?” and “is a shopper’s habits consistent with its personal earlier actions?” These approaches permit for the detection of bizarre behaviors like domain-generated algorithms (DGA) domains, volume-based irregularities in community connections, and strange communication patterns (e.g., lateral motion) within the community. Therefore, evaluating a shopper’s present habits with that of its friends serves as an appropriate baseline for figuring out refined anomalies.
- Detect unknown assaults in real-time: Whileit is comparatively simple to immediately detect identified dangerous indicators (particular IP addresses, domains and many others.), many assaults can go undetected when these indicators are usually not current. If that’s the case, statistics, time and correlation-based detections are of monumental worth to detect unknown assault patterns in an automatic method. By incorporating algorithmic approaches, conventional safety options primarily based on signatures and indicators of compromise (IoC) might be enhanced to grow to be extra self-sufficient and fewer reliant on identified malware indicators.
- Self-learning detection capabilities: ML-driven options be taught from previous occasions with a view to repeatedly enhance their risk detection capabilities, risk scoring, clustering and community visualisations. This might contain coaching the algorithms themselves or adjusting how data is introduced primarily based on suggestions from analysts.
- Enhance Incident Response:By studying from an analyst’s previous incident response actions, ML can automate sure elements of the incident response course of, minimizing the time and assets required to deal with a safety breach. This can contain utilizing algorithms to research textual content and proof, figuring out root causes and assault patterns.
Example of an ML-driven Network Security Solution
When it involves ML-driven Network Detection & Response (NDR) options that incorporate the outlined advantages, ExeonTrace stands out as a number one community safety answer in Europe. Based on award-winning ML algorithms, which incorporate a decade of educational analysis, ExeonTrace supplies organizations with superior ML risk detection capabilities, full community visibility, versatile log supply integration and massive knowledge analytics. In addition, the algorithms depend on metadata evaluation as a substitute of precise payloads which makes them unaffected by encryption, fully hardware-free and suitable with most cybersecurity infrastructures. As a end result, ExeonTrace is ready to course of uncooked log knowledge into highly effective graph databases, that are then analyzed by supervised and unsupervised ML-models. Through correlation and occasion fusion, the algorithms can precisely pinpoint high-fidelity anomalies and refined cues of malicious habits, even when coping with novel or rising cyber threats that will lack established signatures or identified malicious indicators.
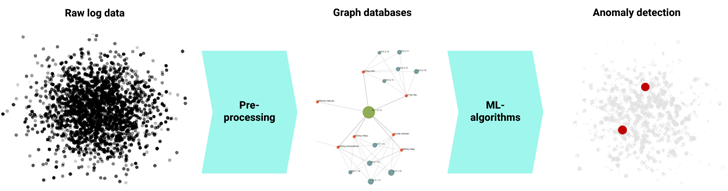 |
| Security Analytics Pipeline: Detection of community anomalies by way of ML |
Conclusion
As the specter of cyber assaults turns into more and more complicated, organizations should transcend conventional safety measures to guard their networks. As a end result, many corporations at the moment are turning to Machine Learning (ML) and predictive analytics to strengthen their safety defenses. In this regard, ML-driven Network Detection & Response (NDR) options, corresponding to ExeonTrace, are designed to assist organizations keep forward of the ever-evolving risk panorama. By using superior ML algorithms that analyze community site visitors and software logs, ExeonTrace affords organizations fast detection and response to even probably the most refined cyberattacks.
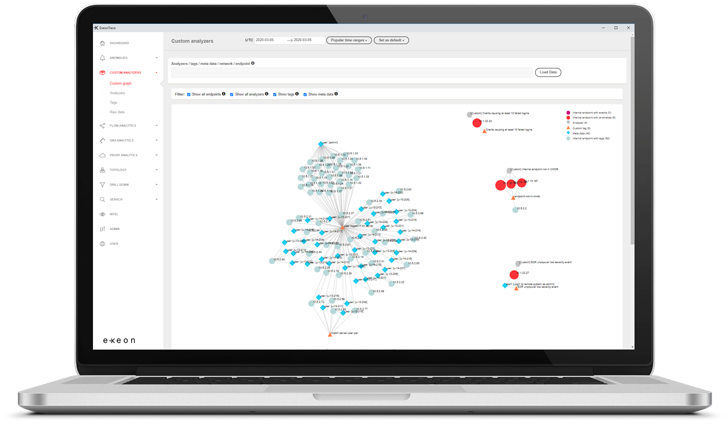 |
| ExeonTrace Platform: Network visibility |
Book a free demo to find how ExeonTrace leverages ML algorithms to make your organisation extra cyber resilient – shortly, dependable and fully hardware-free.

