[ad_1]
An enormous marketing campaign has contaminated over 4,500 WordPress web sites as a part of a long-running operation that is been believed to be energetic since at the least 2017.
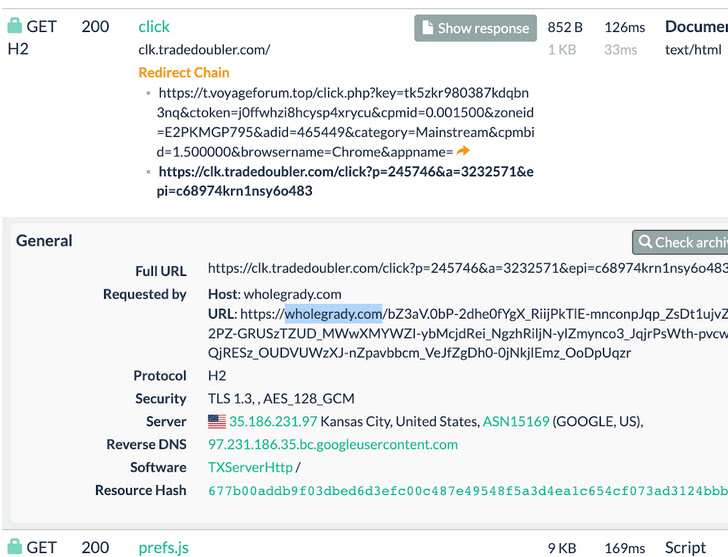
According to GoDaddy-owned Sucuri, the infections contain the injection of obfuscated JavaScript hosted on a malicious area named “monitor[.]violetlovelines[.]com” that is designed to redirect guests to undesirable websites.
The newest operation is claimed to have been energetic since December 26, 2022, in line with knowledge from urlscan.io. A previous wave seen in early December 2022 impacted greater than 3,600 websites, whereas one other set of assaults recorded in September 2022 ensnared greater than 7,000 websites.
The rogue code is inserted within the WordPress index.php file, with Sucuri noting that it has eliminated such modifications from greater than 33,000 recordsdata on the compromised websites previously 60 days.
“In latest months, this malware marketing campaign has step by step switched from the infamous pretend CAPTCHA push notification rip-off pages to black hat ‘advert networks’ that alternate between redirects to authentic, sketchy, and purely malicious web sites,” Sucuri researcher Denis Sinegubko mentioned.
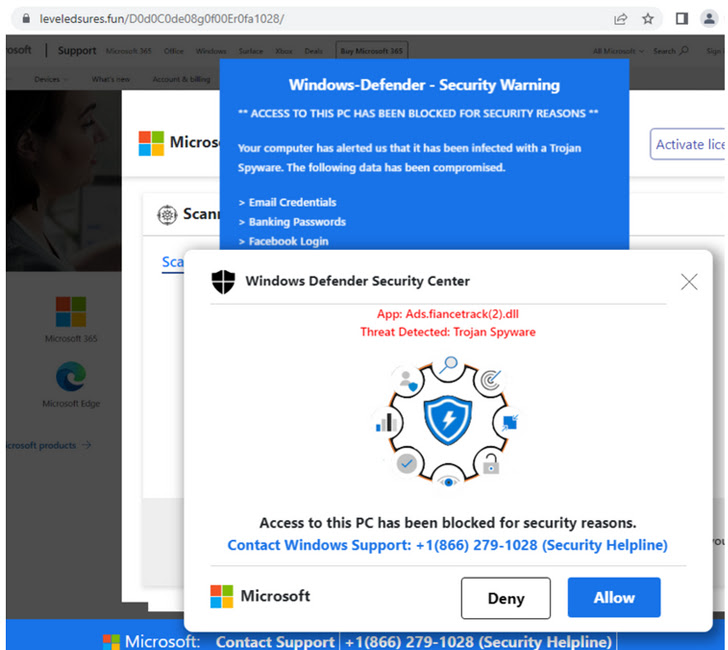
Thus when unsuspecting customers land on one of many hacked WordPress websites, a redirect chain is triggered by the use of a site visitors route system, touchdown the victims on pages serving sketchy adverts about merchandise that sarcastically block undesirable adverts.
Even extra troublingly, the web site for one such advert blocker named Crystal Blocker is engineered to show deceptive browser replace alerts to trick the customers into putting in its extension relying on the internet browser used.
The browser extension is utilized by almost 110,000 customers spanning Google Chrome (60,000+), Microsoft Edge (40,000+), and Mozilla Firefox (8,635).
“And whereas the extensions certainly have advert blocking performance, there isn’t any assure that they’re secure to make use of — and should comprise undisclosed capabilities within the present model or in future updates,” Sinegubko defined.
Some of the redirects additionally fall into the outright nefarious class, with the contaminated web sites appearing as a conduit for initiating drive-by downloads.
This additionally contains retrieving from Discord CDN an information-stealing malware generally known as Raccoon Stealer, which is able to plundering delicate knowledge comparable to passwords, cookies, autofill knowledge from browsers, and crypto wallets.
The findings come as risk actors are establishing lookalike web sites for a wide range of authentic software program to distribute stealers and trojans by way of malicious adverts in Google search outcomes.
Google has since stepped in to dam one of many rogue domains concerned within the redirect scheme, classifying it as an unsafe website that installs “undesirable or malicious software program on guests’ computer systems.”
To mitigate such threats, WordPress website homeowners are suggested to vary passwords and replace put in themes and plugins in addition to take away these which can be unused or deserted by their builders.