[ad_1]

Getty Images
A market-leading storage door controller is so riddled with extreme safety and privateness vulnerabilities that the researcher who found them is advising anybody utilizing one to right away disconnect it till they’re fastened.
Each $80 system used to open and shut storage doorways and management residence safety alarms and good energy plugs employs the identical easy-to-find common password to speak with Nexx servers. The controllers additionally broadcast the unencrypted electronic mail deal with, system ID, first identify, and final preliminary corresponding to every one, together with the message required to open or shut a door or activate or off a sensible plug or schedule such a command for a later time.
Immediately unplug all Nexx units
The consequence: Anyone with a reasonable technical background can search Nexx servers for a given electronic mail deal with, system ID, or identify after which subject instructions to the related controller. (Nexx controllers for residence safety alarms are vulnerable to the same class of vulnerabilities.) Commands enable the opening of a door, turning off a tool related to a sensible plug, or disarming an alarm. Worse nonetheless, over the previous three months, personnel for Texas-based Nexx haven’t responded to a number of personal messages warning of the vulnerabilities.
“Nexx has consistently ignored communication attempts from myself, the Department of Homeland Security, and the media,” the researcher who found the vulnerabilities wrote in a submit revealed on Tuesday. “Device owners should immediately unplug all Nexx devices and create support tickets with the company requesting them to remediate the issue.”
The researcher estimates that greater than 40,000 units, positioned in residential and industrial properties, are impacted and greater than 20,000 people have energetic Nexx accounts.
Nexx controllers enable individuals to make use of their telephones or voice assistants to open and shut their storage doorways, both on command or at scheduled instances of the day. The units can be used to manage residence safety alarms and good plugs used to remotely activate or off home equipment. The hub of this technique are servers operated by Nexx, which each the telephone or voice assistant and storage door opener hook up with. The five-step course of for enrolling a brand new system appears like this:
- The consumer makes use of the Nexx Home cell app to register their new Nexx system with the Nexx Cloud.
- Behind the scenes, the Nexx Cloud returns a password for the system to make use of for safe communications with the Nexx Cloud.
- The password is transmitted to the consumer’s telephone and despatched to the Nexx system utilizing Bluetooth or Wi-Fi.
- The Nexx system establishes an unbiased reference to the Nexx Cloud utilizing the offered password.
- The consumer can now function their storage door remotely utilizing the Nexx Mobile App.
This is an illustration of the method:
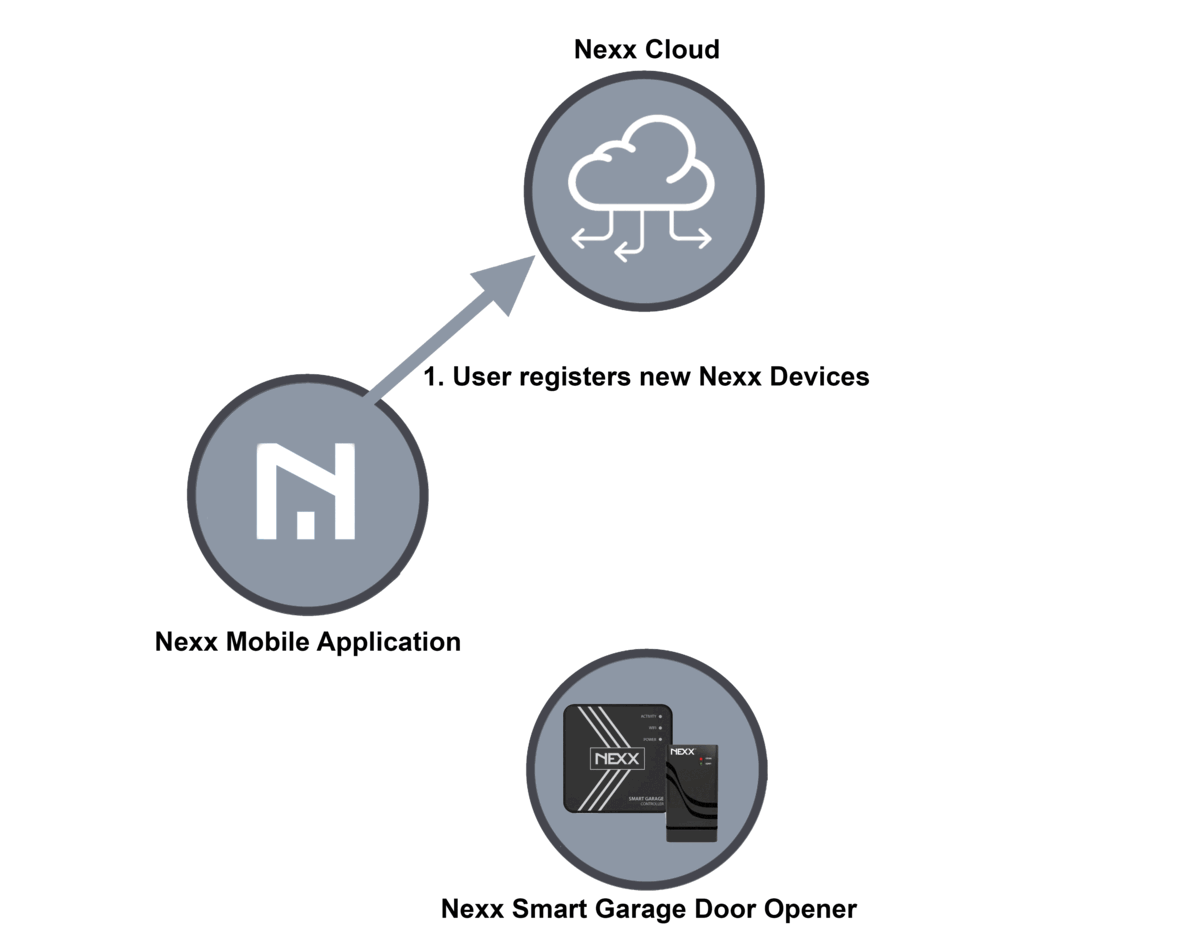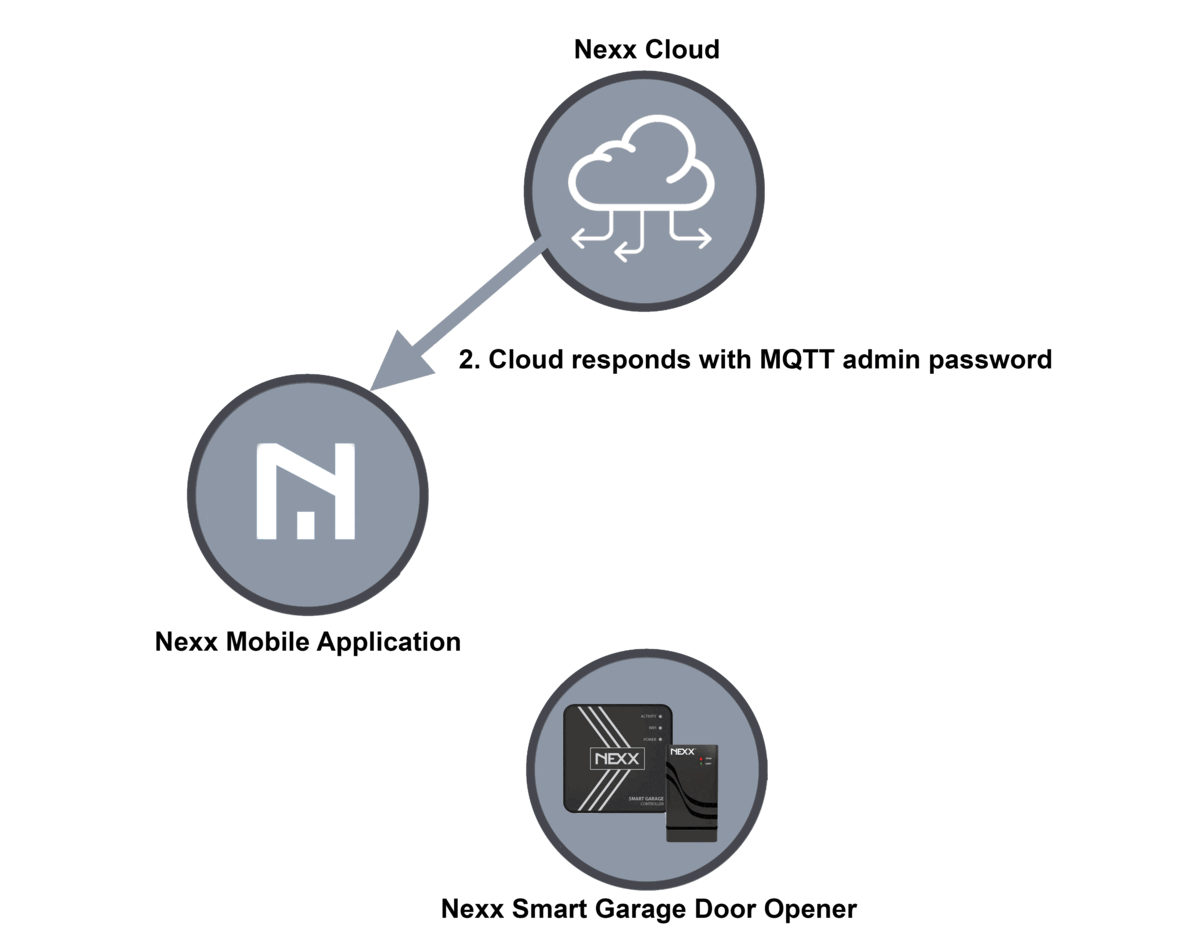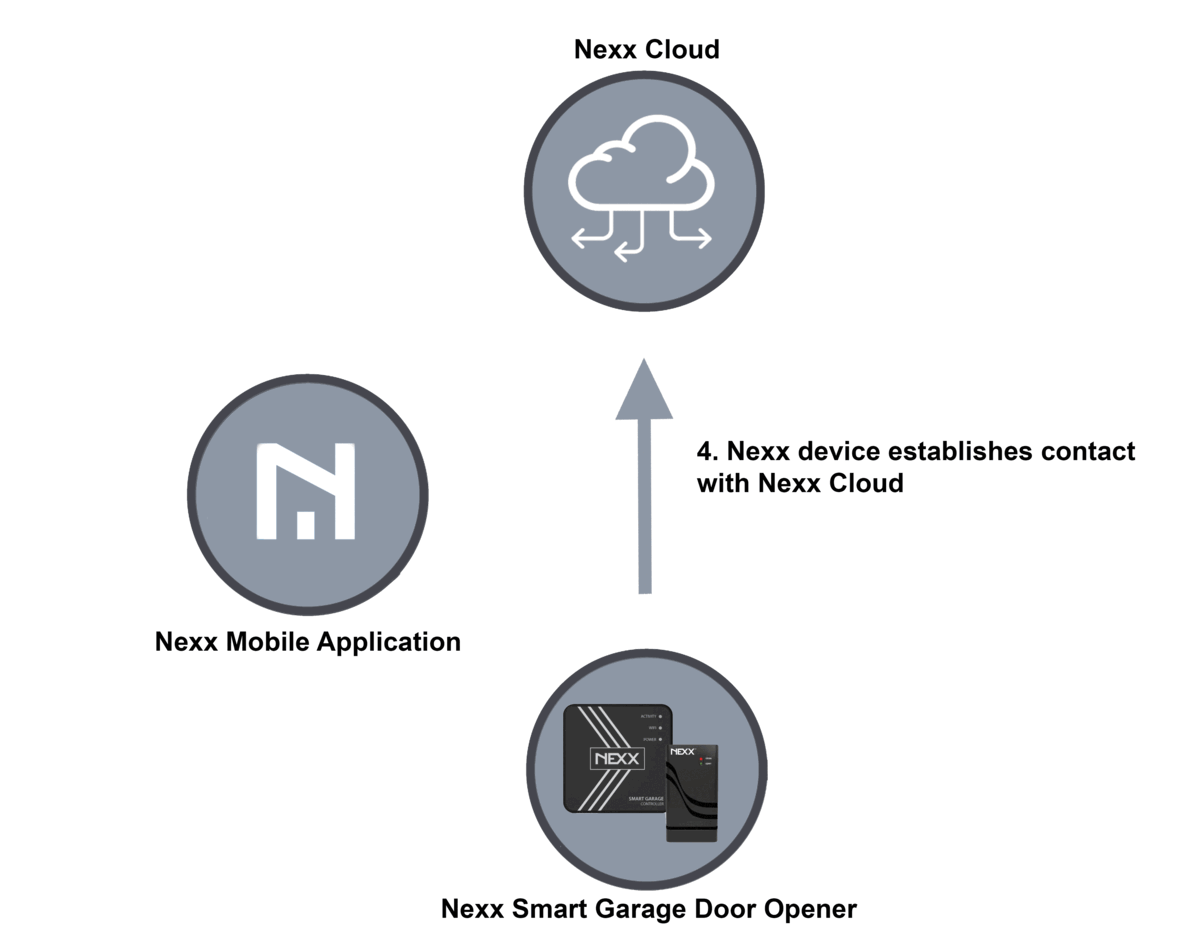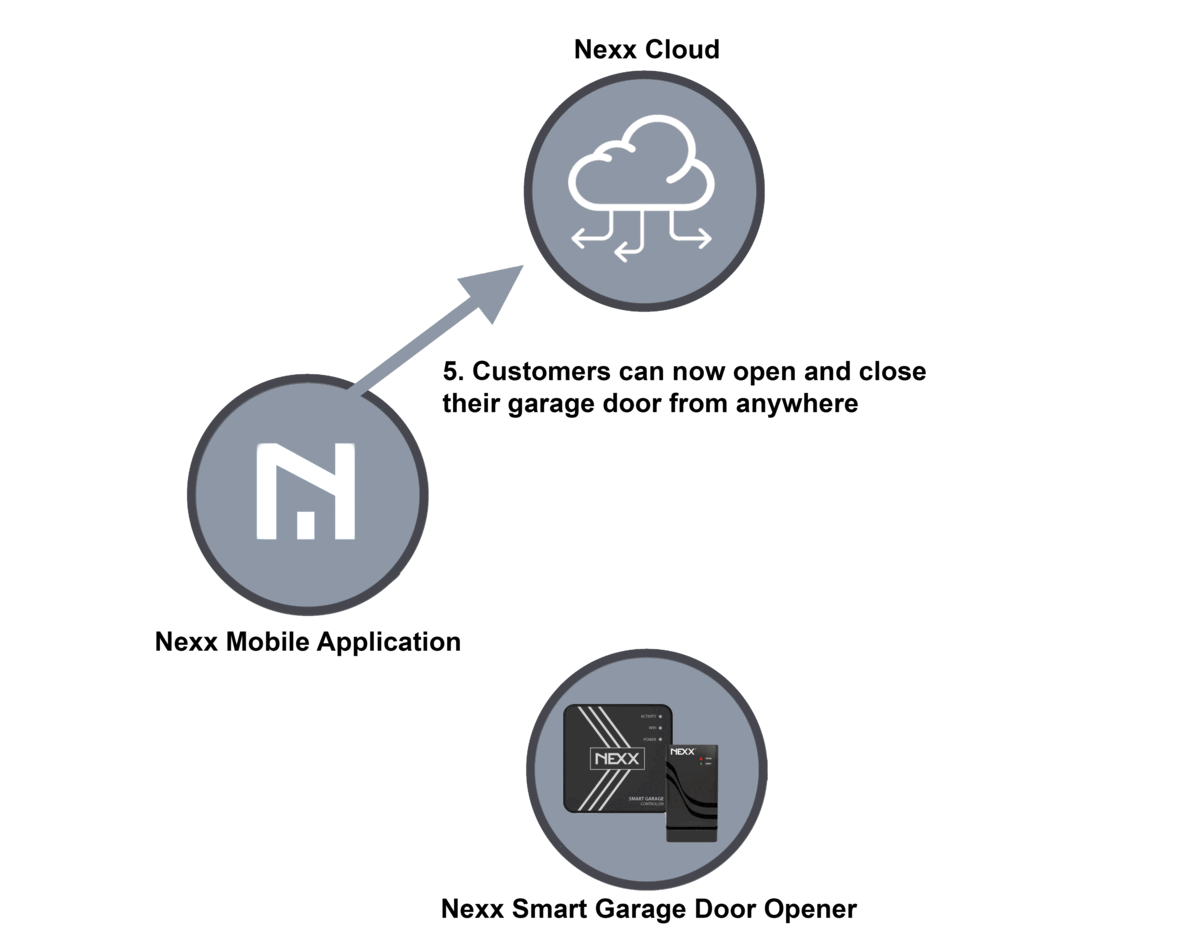
Sam Sabetan
A common password that is simple to seek out
To make all of this work, the controllers use a light-weight protocol often called MQTT. Short for Message Queuing Telemetry Transport, it’s utilized in low-bandwidth, high-latency, or in any other case unstable networks to foster environment friendly and dependable communication between units and cloud providers. To do that, Nexx makes use of a publish-to-subscribe mannequin, during which a single message is shipped between subscribed units (the telephone, voice assistant, and storage door opener) and a central dealer (the Nexx cloud).
Researcher Sam Sabetan discovered that units use the identical password to speak with the Nexx cloud. What’s extra, this password is well attainable just by analyzing the firmware shipped with the system or the back-and-forth communication between a tool and the Nexx cloud.
“Using a universal password for all devices presents a significant vulnerability, as unauthorized users can access the entire ecosystem by obtaining the shared password,” the researcher wrote. “In doing so, they could compromise not only the privacy but also the safety of Nexx’s customers by controlling their garage doors without their consent.”
When Sabetan used this password to entry the server, he rapidly discovered not solely communications between his system and the cloud however communications for different Nexx units and the cloud. That meant he may sift by way of the e-mail addresses, final names, first initials, and system IDs of different customers to establish clients primarily based on distinctive data shared in these messages.
But it will get worse nonetheless. Sabetan may copy messages different customers issued to open their doorways and replay them at will—from wherever on this planet. That meant a easy cut-and-paste operation was sufficient to manage any Nexx system regardless of the place he or it was positioned.
A proof-of-concept video demonstrating the hack follows:
NexxHome Smart Garage Vulnerability – CVE-2023-1748.
This occasion brings to thoughts the worn-out cliché that the S in IoT—quick for the umbrella time period Internet of Things—stands for safety. While many IoT units present comfort, a daunting variety of them are designed with minimal safety protections. Outdated firmware with identified vulnerabilities and the lack to replace are typical, as are myriad flaws reminiscent of hardcoded credentials, authorization bypasses, and defective authentication verification.
Anyone utilizing a Nexx system ought to severely think about disabling it and changing it with one thing else, though the usefulness of this recommendation is restricted since there’s no assure that the alternate options might be any safer.
With so many units in danger, the US Cybersecurity and Infrastructure Security Agency issued an advisory that implies customers take defensive measures, together with:
- Minimizing community publicity for all management system units and/or techniques, and guarantee they’re not accessible from the Internet.
- Locating management system networks and distant units behind firewalls and isolating them from enterprise networks.
- When distant entry is required, use safe strategies, reminiscent of digital personal networks (VPNs), recognizing VPNs could have vulnerabilities and needs to be up to date to probably the most present model out there. Also acknowledge VPN is simply as safe as its related units.
Of course, these measures are unattainable to deploy when utilizing Nexx controllers, which brings us again to the general insecurity of IoT and Sabetan’s recommendation to easily ditch the product except or till a repair arrives.
