[ad_1]
A brand new phishing marketing campaign abuses OneNote paperwork to contaminate computer systems with the notorious AsyncRAT malware, concentrating on customers within the U.Ok., Canada and the U.S.

As Microsoft determined to change the default of its Office merchandise to dam macros on recordsdata downloaded from the web, cybercriminals noticed one in all their favourite an infection strategies vanish.
Some cybercriminals have already discovered a workaround to maintain utilizing some Microsoft Office merchandise, like abusing the XLL recordsdata from Excel. Some different cybercriminals have discovered a special technique to hold abusing Microsoft merchandise for infecting computer systems with malware: contaminated OneNote paperwork.
SEE: Mobile system safety coverage (TechRepublic Premium)
Phishing assaults ship AsyncRAT malware
A brand new Bitdefender research exposes a phishing marketing campaign abusing OneNote to contaminate computer systems with malware. In that assault marketing campaign, cybercriminals impersonated Ultramar, a Canadian gasoline and residential gasoline retailer, sending phishing emails supposedly coming from the corporate (Figure A).
Figure A
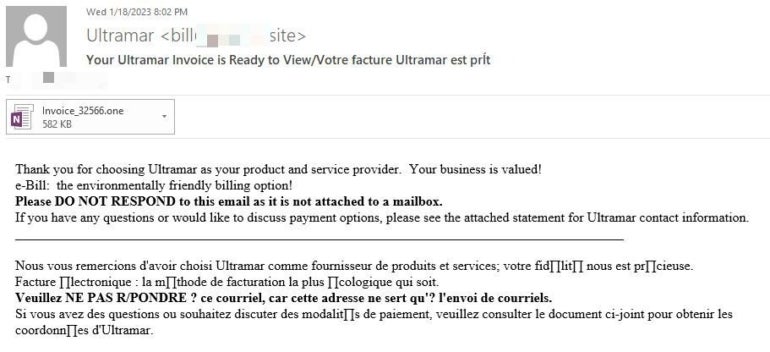
As will be seen in Figure A, the e-mail accommodates textual content in each English and French language, however most significantly an hooked up file named Invoice_32566.one — the .one file extension indicating a OneNote file.
A second comparable phishing marketing campaign hit Canada, the U.Ok. and the U.S. with one other filename for the attachment, Invoice_76562.one.
The payloads triggered by these OneNote paperwork, as soon as opened, have been downloaded from a Catholic Church in Canada and a Digital Service Provider in India. Both have been compromised by the attackers or presumably delivered to some preliminary entry dealer (IAB) on-line and used for internet hosting the malwares. This is a typical approach utilized by cybercriminals to keep away from detection for an extended time period through the use of a reputable web site to host their malicious code.
In the tip, customers opening the OneNote paperwork have been contaminated with AsyncRAT, which Bitdefender describes as “a nifty remote access tool designed to stealthily let an attacker infiltrate the devices of the target victim’s device.”
What is AsyncRAT?
AsyncRAT supply code has been out there totally free on the web since 2019, which suggests the unique model is detected by most safety options, if not all. Yet, it additionally means builders can use the supply code of AsyncRAT and modify it so as to add or take away options or to render it much less detectable.
Currently, that malware is able to recording screens, capturing keystrokes, manipulating recordsdata on the system, executing code or launching distributed denial-of-service assaults. This means it may be used for a wide range of functions.
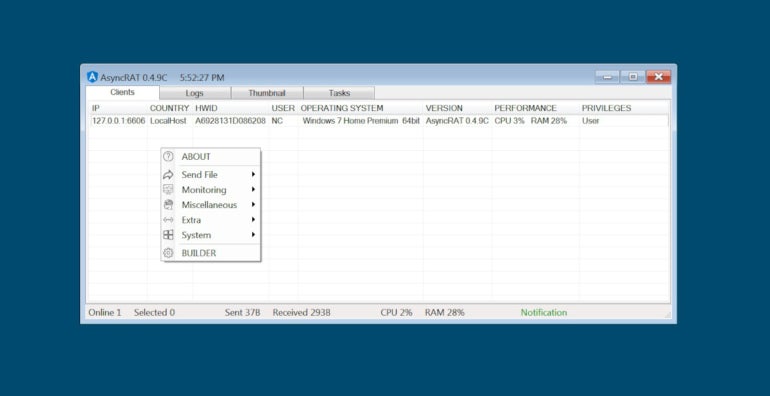
It has already been utilized by cyberespionage menace actors or for financially-oriented targets. Once a pc is contaminated with AsyncRAT, the attacker can see the machine within the instruments administration panel and act on the machine as wanted (Figure B). Several contaminated machines will be dealt with in the identical interface.
Figure B
More assaults within the wild
Bitdefender researchers are usually not the one ones who’ve investigated the brand new menace AsyncRAT poses. December 2022, Trustwave additionally reported phishing assault campaigns, this time delivering the Formbook malware, a ramification data stealer able to stealing passwords, taking display screen captures, executing code and extra.
“It’s clear to see how cybercriminals leverage new attack vectors or less-detected means to compromise user devices,” declared Adrian Miron, supervisor at Bitdefender’s Cyber Threat Intelligence Lab. “These campaigns are likely to proliferate in coming months, with cybercrooks testing out better or improved angles to compromise victims.”
How to guard from this menace?
Companies that don’t use OneNote ought to block .one extensions of their electronic mail servers. This would stop any inner customers from by chance opening contaminated recordsdata on firm instruments. Instead, staff ought to request recordsdata in one other format like .doc or .xlsx to keep away from potential publicity. As a extra excessive step, these firms may stop staff from downloading or utilizing OneNote on firm instruments and programs, however this isn’t really helpful as some staff would possibly at the moment use the instrument.
Malicious OneNote recordsdata principally make use of hooked up recordsdata contained in the doc. When accessing these attachments, a warning is raised by the software program to inform the person it would hurt the pc and knowledge. Yet, expertise has proven that customers usually neglect these warnings and simply click on the validation button. Companies can work to forestall these threats by:
- Raising consciousness on doubtlessly dangerous recordsdata and hyperlinks to all staff.
- Building protocols and coaching on how to answer warnings of malicious recordsdata or hyperlinks.
- Deploying safety options that detect malicious code when it’s triggered from a OneNote file or different threats.
- Updating and patching all programs and software program to keep away from being compromised by a typical vulnerability.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
