[ad_1]
The infamous Emotet malware has returned with renewed vigor as a part of a high-volume malspam marketing campaign designed to drop payloads like IcedID and Bumblebee.
“Hundreds of 1000’s of emails per day” have been despatched since early November 2022, enterprise safety firm Proofpoint mentioned final week, including, “the brand new exercise suggests Emotet is returning to its full performance appearing as a supply community for main malware households.”
Among the first nations focused are the U.S., the U.Okay., Japan, Germany, Italy, France, Spain, Mexico, and Brazil.
The Emotet-related exercise was final noticed in July 2022, though sporadic infections have been reported since then. In mid-October, ESET revealed that Emotet could also be readying for a brand new wave of assaults, declaring updates to its “systeminfo” module.
The malware, which is attributed to a risk actor referred to as Mummy Spider (aka Gold Crestwood or TA542), staged a revival of types late final 12 months after its infrastructure was dismantled throughout a coordinated legislation enforcement operation in January 2021.
Europol known as Emotet the “world’s most harmful malware” for its capability to behave as a “main door opener for laptop techniques” to deploy next-stage binaries that facilitate knowledge theft and ransomware. It began off in 2014 as a banking trojan earlier than evolving right into a botnet.
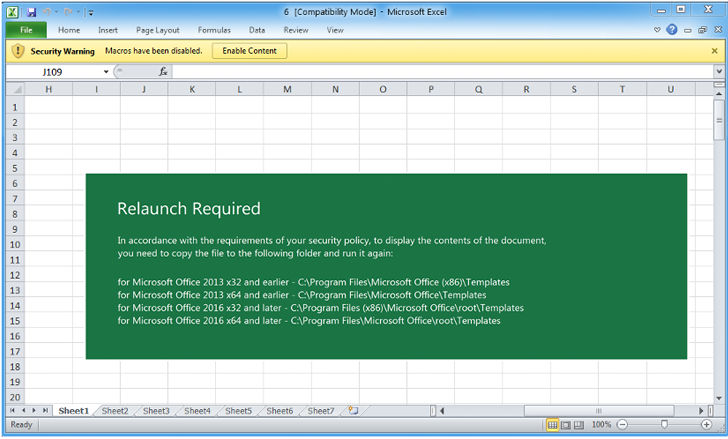
Infection chains involving the malware are identified to make use of generic lures in addition to the strategy of e mail thread hijacking to lure recipients into opening macro-enabled Excel attachments.
“Following Microsoft’s current announcement that it might start disabling macros by default in Office paperwork downloaded from the web, many malware households have begun migrating away from Office macros to different supply mechanisms like ISO and LNK information,” Cisco Talos mentioned earlier this month.
“Therefore, it’s attention-grabbing to notice that this new marketing campaign of Emotet is utilizing its outdated technique of distributing malicious Microsoft Office paperwork (maldocs) by way of email-based phishing.
An different technique urges potential victims to repeat the file to a Microsoft Office Template location – a trusted location – and launch the lure doc from there as an alternative of getting to explicitly allow macros to activate the kill-chain.
The renewed exercise has additionally been accompanied by modifications to the Emotet loader part, and addition of recent instructions, and updates to the packer to withstand reverse engineering.
One of the follow-on payloads distributed by means of Emotet is a model new variant of the IcedID loader, which receives instructions to learn and ship file contents to a distant server, along with executing different backdoor directions that permit it to extract net browser knowledge.
The use of IcedID is regarding because it’s seemingly a precursor for ransomware, the researchers identified. Another malware dropped by way of Emotet is Bumblebee, in keeping with Palo Alto Networks Unit 42.
“Overall, these modifications made to the shopper point out the builders try to discourage researchers and scale back the variety of faux or captive bots that exist throughout the botnet,” researchers Pim Trouerbach and Axel F mentioned.
“Emotet has not demonstrated full performance and constant follow-on payload supply (that is not Cobalt Strike) since 2021, when it was noticed distributing The Trick and Qbot.”