[ad_1]
State-backed hackers from North Korea are conducting ransomware assaults in opposition to healthcare and significant infrastructure services to fund illicit actions, U.S. and South Korean cybersecurity and intelligence businesses warned in a joint advisory.
The assaults, which demand cryptocurrency ransoms in alternate for recovering entry to encrypted recordsdata, are designed to assist North Korea’s national-level priorities and goals.
This contains “cyber operations focusing on the United States and South Korea governments — particular targets embrace Department of Defense Information Networks and Defense Industrial Base member networks,” the authorities stated.
Threat actors with North Korea have been linked to espionage, monetary theft, and cryptojacking operations for years, together with the notorious WannaCry ransomware assaults of 2017 that contaminated lots of of hundreds of machines positioned in over 150 nations.
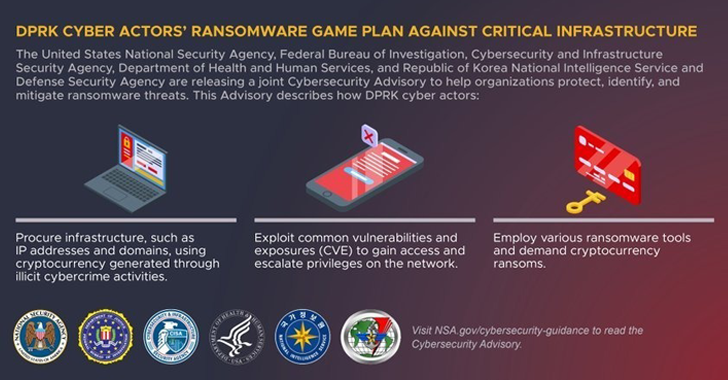
Since then, North Korean nation-state crews have dabbled in a number of ransomware strains similar to VHD, Maui, and H0lyGh0st to generate a gradual stream of unlawful revenues for the sanctions-hit regime.
Besides procuring its infrastructure via cryptocurrency generated via its legal actions, the adversary is thought to operate beneath third-party international affiliate identities to hide their involvement.
Attack chains mounted by the hacking crew entail the exploitation of recognized safety flaws in Apache Log4j, SonicWall, and TerraMaster NAS home equipment (e.g., CVE 2021-44228, CVE-2021-20038, and CVE-2022-24990) to realize preliminary entry, following it up by reconnaissance, lateral motion, and ransomware deployment.
In addition to utilizing privately developed ransomware, the actors have been noticed leveraging off-the-shelf instruments like BitLocker, DeadBolt, ech0raix, Jigsaw, and YourRansom for encrypting recordsdata, to not point out even impersonating different ransomware teams similar to REvil.
As mitigations, the businesses suggest organizations to implement the precept of least privilege, disable pointless community machine administration interfaces, implement multi-layer community segmentation, require phishing-resistant authentication controls, and preserve periodic information backups.
The alert comes as a brand new report from the United Nations discovered that North Korean hackers stole record-breaking digital property estimated to be value between $630 million and greater than $1 billion in 2022.
The report, seen by the Associated Press, stated the risk actors used more and more refined methods to realize entry to digital networks concerned in cyberfinance, and to steal info from governments, firms, and people that might be helpful in North Korea’s nuclear and ballistic missile packages.
It additional known as out Kimsuky, Lazarus Group, and Andariel, that are all a part of the Reconnaissance General Bureau (RGB), for persevering with to focus on victims with the aim of making income and soliciting info of worth to the hermit kingdom.