[ad_1]
A beforehand unknown menace actor dubbed NewsPenguin has been linked to a phishing marketing campaign focusing on Pakistani entities by leveraging the upcoming worldwide maritime expo as a lure.
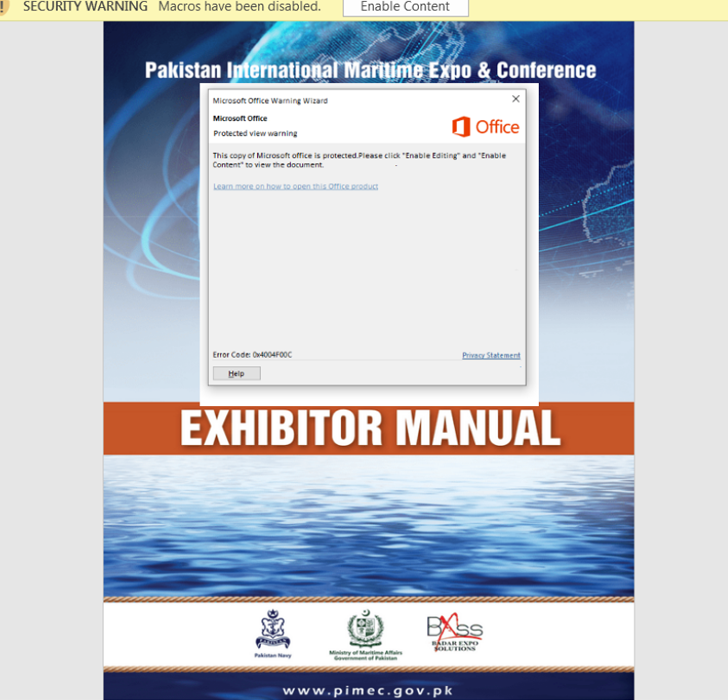
“The attacker despatched out focused phishing emails with a weaponized doc hooked up that purports to be an exhibitor handbook for PIMEC-23,” the BlackBerry Research and Intelligence Team mentioned.
PIMEC, brief for Pakistan International Maritime Expo and Conference, is an initiative of the Pakistan Navy and is organized by the Ministry of Maritime Affairs with an intention to “soar begin growth within the maritime sector.” It’s scheduled to be held from February 10-12, 2023.
The Canadian cybersecurity firm mentioned the assaults are designed to focus on marine-related entities and the occasion’s guests by tricking the message recipients into opening the seemingly innocent Microsoft Word doc.
Once the doc is launched and macros are enabled, a way known as distant template injection is employed to fetch the next-stage payload from an actor-controlled server that is configured to return the artifact provided that the request is shipped from an IP tackle situated in Pakistan.
BlackBerry mentioned it discovered the server to be internet hosting two ZIP archive recordsdata sans any password protections, considered one of which features a Windows executable (updates.exe) that capabilities as a covert spying instrument able to bypassing sandboxes and digital machines.
Dmitry Bestuzhev, a menace researcher at BlackBerry, advised The Hacker News that the backdoor has been written from scratch in a way that is tailor-made to this marketing campaign.
“The menace actor behind it made a particular effort to fly beneath the radar by being undetected,” Bestuzhev mentioned. “For instance, between every request, there’s a 5 minute delay. That’s to minimize the danger of being uncovered.”
“The implant consists of self-deletion instructions in case of publicity or when the op is finalized. It additionally incorporates instructions for knowledge switch, deleting different recordsdata, and executing/working different apps within the sufferer’s system. It appears to be like for recordsdata within the system, gathers details about them, and uploads them to the distant server if the recordsdata are attention-grabbing. It’s designed to steal delicate recordsdata on the sufferer’s disk.”
What’s extra, the contents of the binary are encrypted with the XOR encryption algorithm, the place the XOR key’s “penguin.” The HTTP response containing the backdoor additionally comes with the identify parameter within the Content-Disposition response header set to “getlatestnews.”
The identify NewsPenguin is a reference to the unusual XOR key and the identify parameter, with BlackBerry discovering no tactical overlaps that join the malware to any currently-known menace actor or group.
An evaluation of the area internet hosting the payloads reveals that it has been registered since June 30, 2022, indicating some degree of advance planning for the marketing campaign whereas concurrently taking steps to iterate its toolset.
“As the goal is an occasion run by the Pakistan Navy, it implies that the menace actor is actively focusing on authorities organizations, somewhat than this being a financially motivated assault,” BlackBerry mentioned.
“It seems that the objective of this marketing campaign is to seek out and steal essentially the most attention-grabbing recordsdata containing details about the theme of the convention, individuals’s networking, and applied sciences introduced there,” Bestuzhev added.