[ad_1]

Cybersecurity researchers and IT admins have raised issues over Google’s new ZIP and MOV Internet domains, warning that menace actors might use them for phishing assaults and malware supply.
Earlier this month, Google launched eight new top-level domains (TLD) that may very well be bought for internet hosting web sites or electronic mail addresses.
The new domains are .dad, .esq, .prof, .phd, .nexus, .foo, and for the subject of our article, the .zip and .mov area TLDs.
While the ZIP and MOV TLDs have been accessible since 2014, it wasn’t till this month that they grew to become typically accessible, permitting anybody to buy a site, like bleepingcomputer.zip, for an internet site.
However, these domains may very well be perceived as dangerous because the TLDs are additionally extensions of recordsdata generally shared in discussion board posts, messages, and on-line discussions, which can now be robotically transformed into URLs by some on-line platforms or functions.
The concern
Two frequent file varieties seen on-line are ZIP archives and MPEG 4 movies, whose file names finish in .zip (ZIP archive) or .mov (video file).
Therefore, it is quite common for individuals to submit directions containing filenames with the .zip and .mov extensions.
However, now that they’re TLDs, some messaging platforms and social media websites will robotically convert file names with .zip and .mov extensions into URLs.
For instance, on Twitter, in the event you ship somebody directions on opening a zipper file and accessing a MOV file, the innocuous filenames are transformed into an URL, as proven under.
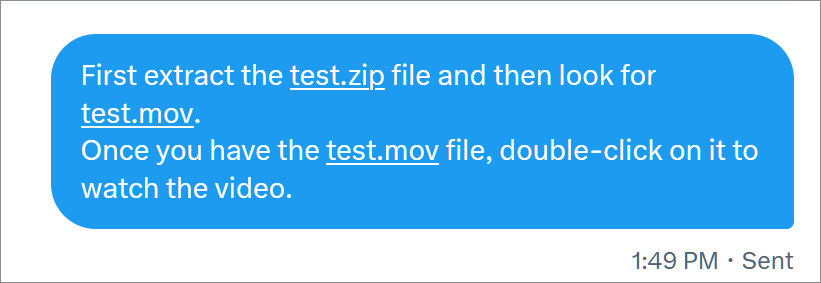
Source: BleepingComputer
When individuals see URLs in directions, they generally assume that the URL can be utilized to obtain the related file and will click on on the hyperlink. For instance, linking filenames to downloads is how we normally present directions on BleepingComputer in our articles, tutorials, and dialogue boards.
However, if a menace actor owned a .zip area with the identical title as a linkified filename, an individual could mistakenly go to the location and fall for a phishing rip-off or obtain malware, considering the URL is protected as a result of it got here from a trusted supply.
While it is impossible that menace actors will register 1000’s of domains to seize a couple of victims, you solely want one company worker to mistakenly set up malware for a complete community to be affected.
Abuse of those domains just isn’t theoretical, with cyber intel agency Silent Push Labs already discovering what seems to be a phishing web page at microsoft-office[.]zip trying to steal Microsoft Account credentials.
Cybersecurity researchers have additionally began to play with the domains, with Bobby Rauch publishing analysis on creating convincing phishing hyperlinks utilizing Unicode characters and the userinfo delimiter (@) in URLs.
Rauch’s analysis exhibits how menace actors could make phishing URLs that appear like reliable file obtain URLs at GitHub however truly take you to an internet site at v1.27.1[.]zip when clicked, as illustrated under.
https://github.com/kubernetes/kubernetes/archive/refs/tags/@v1.27.1.zipConflicting opinions
These developments have sparked a debate amongst builders, safety researchers, and IT admins, with some feeling the fears usually are not warranted and others feeling that the ZIP and MOV TLDs add pointless danger to an already dangerous on-line atmosphere.
People have begun registering .zip domains which might be related to frequent ZIP archives, similar to replace.zip, financialstatement.zip, setup.zip, attachment.zip, officeupdate.zip, and backup.zip, to show details about the dangers of ZIP domains, to RickRoll you, or to share innocent info.
Open supply developer Matt Holt additionally requested that the ZIP TLD be faraway from Mozilla’s Public Suffix List, a listing of all public top-level domains to be included in functions and browsers.
However, the PSL neighborhood shortly defined that whereas there could also be a slight danger related to these TLDs, they’re nonetheless legitimate and shouldn’t be faraway from the PSL as it will have an effect on the operation of reliable websites.
“Removing present TLDs from the PSL because of this would simply be mistaken. This record is used for many totally different causes, and simply because these entries are dangerous for one very particular use-case, they’re nonetheless wanted for (nearly) all others,” defined software program engineer Felix Fontein.
“These are legit TLDs within the ICP3 root. This won’t proceed,” additional shared PSL maintainer Jothan Frakes.
“Really, the expressed issues are extra of a obtrusive instance of a disconnect between the developer and safety neighborhood and area title governance, the place they’d profit from extra engagement inside ICANN.”
At the identical time, different safety researchers and builders have expressed that they imagine the fears relating to these new domains are overblown.
When BleepingComputer contacted Google about these issues, they stated that the danger of confusion between file and domains just isn’t new, and browser mitigations are in place to guard customers from abuse.
“The danger of confusion between domains and file names just isn’t a brand new one. For instance, 3M’s Command merchandise use the area title command.com, which can be an necessary program on MS DOS and early variations of Windows. Applications have mitigations for this (similar to Google Safe Browsing), and these mitigations will maintain true for TLD’s similar to .zip.
At the identical time, new namespaces present expanded alternatives for naming similar to neighborhood.zip and url.zip. Google takes phishing and malware significantly and Google Registry has present mechanisms to droop or take away malicious domains throughout all of our TLDs, together with .zip. We will proceed to watch the utilization of .zip and different TLDs and if new threats emerge we’ll take acceptable motion to guard customers.” – Google.
What do you have to do?
The actuality is that you don’t want to do something additional than you might be already doing to guard your self from phishing websites.
As everybody ought to already know, it’s by no means protected to click on on hyperlinks from individuals or obtain recordsdata from websites you don’t belief.
Like any hyperlink, in the event you see a .zip or .mov hyperlink in a message, analysis it earlier than clicking on it. If you might be nonetheless not sure if the hyperlink is protected, don’t click on on it.
By following these easy steps, the affect of the brand new TLDs will probably be minimal and never considerably enhance your danger.
However, the publicity to those hyperlinks will doubtless enhance as extra functions robotically flip ZIP and MOV filenames into hyperlinks, supplying you with another factor to watch out about when on-line.